Introducing a new approach to code security
In many ways, software is the lifeblood of modern companies, which makes the security of its code paramount. However, code sprawl is a very real and daunting problem. With millions of lines of code that are constantly being reused, forked, and updated, how can teams effectively secure their code and protect their systems, data, and reputations?
While code security tools have been around for over a decade, they are highly fragmented, generate excessive noise, lack the context necessary to understand risk, and fail to give security teams much needed visibility into what developers are doing and who needs help. Lacework solves these challenges with a unified platform that spans from code to run.
Code security is a data problem
At Lacework, we’re pioneering a new approach to code security. Instead of addressing code security and cloud security as separate practices, Lacework addresses them as part of a single security continuum that spans the entire software development life cycle (SDLC).
With today’s release, Lacework is extending our platform capabilities and building upon our previous investments in securing infrastructure as code (IaC). Lacework can now enable customers to prevent third-party and first-party code risks from getting into the wild and rapidly find and fix risks at the source, as developers write and commit code.
This release includes:
- Software composition analysis (SCA)
- Software bill of materials (SBOM)
- Static application security testing (SAST)
With Lacework, teams now gain the end-to-end visibility and context necessary to prioritize source code vulnerabilities. By connecting code with cloud telemetry, companies can now use data to measure each vulnerability in terms of relative risk to their unique environments.
Thanks to these tools, security teams effectively manage runtime risks with downstream development context such as insight into what code is secure, where compensating controls are required, and who owns what code in production. Likewise, development teams can now more efficiently deliver secure code by gaining upstream runtime context such as insight into whether code is running, what version or versions are in use, where it is running, and whether it’s behaving as expected.
Third-party and open-source risk management
A key to code security is knowing what’s in your codebase. But, because of the never-ending web of indirect and transient third-party dependencies, it’s not easy to keep track of your code’s components.
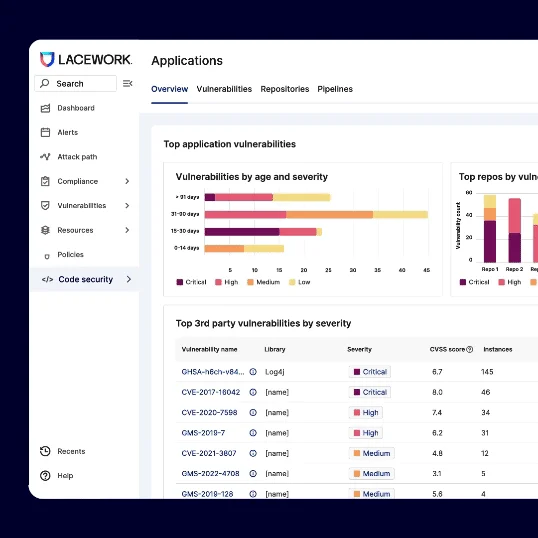
Figure 1: Lacework SCA gives customers continuous visibility into their third-party software, indirect dependencies, and any associated vulnerabilities.
Lacework software composition analysis (SCA) gives customers continuous visibility into their third-party and open-source software packages, indirect dependencies, and any associated vulnerability and license risks.
Our unique approach goes far beyond basic SCA functionality. We provide teams continuous visibility into exactly where and how vulnerable packages are used, how often each is referenced, who owns the code and was responsible for bringing it in, and how to rapidly remediate vulnerabilities.
Know which code is active in production environments
Since Lacework SCA is an integral part of the Lacework platform and shares its cloud telemetry, we can enrich SCA vulnerability findings with runtime context, including whether a vulnerable package is actively used in production environments.
This Active Vulnerability Detection (AVD) is accomplished using an extension of the Lacework runtime agent known as Code Aware Agent (CAA). We previously announced AVD for host packages, and, today, we’re expanding it to support containers, enabling teams to identify runtime package activity across heterogeneous cloud workloads.
With Lacework, teams can gain unprecedented visibility into what third-party packages are active, which allows them to prioritize vulnerabilities in terms of the risk they pose within their specific environment.
“Having visibility into vulnerabilities in our codebase and what’s being used in production helps tremendously when responding to zero-day exploits — like Log4j and what will inevitably come next,” says Zachary Rohrbach, Staff Security Engineer at Quickbase. “Lacework gives us the ability to understand how to prioritize these vulnerabilities based on when and where they are used, helping us to reduce risk, accelerate innovation, and create better incident response outcomes.”
Lacework gives us the ability to understand how to prioritize these vulnerabilities based on when and where they are used, helping us to reduce risk, accelerate innovation, and create better incident response outcomes.
In addition, Lacework enables development teams to deliver secure code fast by automatically identifying the vulnerabilities that each developer has introduced with their changes, instead of getting a list that includes thousands of longstanding issues. The platform can also auto-generate pull requests for each vulnerable package it finds to accelerate the process of bumping them to a safer version.
Continuous visibility into application components and licenses
With Lacework SCA, teams also gain continuous visibility of their software supply chain through an always-up-to-date software bill of materials (SBOM) for each application. Lacework eliminates the risks associated with stale or outdated SBOMs by dynamically generating them each time a merge or pull request is committed.

Figure 2: Gain continuous visibility of your software supply chain through an always-up-to-date SBOM.
For existing SBOMs, we identify what is new or has changed and continuously append that data to the previous version. We also make it easier for customers to share sensitive supply chain information with their customers and partners by giving them the means to programmatically control access to SBOMs.
Finally, Lacework SCA helps assess risk and compliance with open-source software licenses by identifying if the package use conflicts with a particular license. The platform can identify different types of license restrictions and any imposed obligations such as attribution, source code disclosure, and copyleft requirements. This can help teams avoid packaging software that may create downstream open-source compliance risks, which can help mitigate potential IP or financial risks resulting from open-source non-compliance.
Fast and accurate first-party code security
Companies must also secure their own first-party code — the code that provides innovative capabilities and helps them differentiate their businesses. To that end, Lacework static application security testing (SAST) identifies source-code weaknesses and defects in first-party code that an attacker could exploit to bypass security controls, run malicious commands, or exfiltrate sensitive data. Lacework essentially automates an expert-level secure code review, which enables application security teams to scale and meet the demands of much larger development teams.
Secure code without slowing down
Lacework understands that because application security teams are heavily outnumbered by software developers, secure code assessments must take place when developers are coding. Lacework SAST allows developers to rapidly find and fix configuration-level vulnerabilities. These are easily found patterns and well-known defects like using hard coded secrets or previously compromised algorithms like MD5. With Lacework, developers gain fast and accurate results that minimize security obstacles and friction as they write and commit code.
Deeper SAST for hard-to-find defects
With Lacework SAST, application security engineers also gain visibility into complex and elusive security defects that can be hidden deep within their companies’ most exposed internet-facing applications. Our analysis is both precise and fast. The platform grants the ability to assess millions of lines of code in minutes and boasts low false positive and false negative rates.
Figure 3: Lacework analyzes and monitors the flow of contaminated data throughout the application to identify risks like SQL injection.
Lacework uses our in-depth knowledge of language libraries and frameworks to minimize inaccurate findings while maximizing true positives. Lacework creates a highly-accurate model of an application that tracks the path of untrusted data across call chains and control paths to weed out zero-days that could result in dangerous exploits like SQL injection and cross-site scripting. In addition, our deep analysis learns when a developer has added compensating controls to mitigate a potential risk.
Historically, tuning SAST engines has been very complex — if even possible. Lacework SAST was built by security engineers for security engineers, and our highly-configurable engine allows security engineers to easily customize and add rules to meet the specific needs of their unique codebases.
Secure applications start with solid infrastructure
Effective code security requires securing both your application code and the cloud services surrounding it. To that end, Lacework SCA and SAST build upon already-existing IaC security capabilities within the Lacework platform.
Lacework offers automated security and compliance checks of IaC early in the development process to prevent misconfigured cloud services from being deployed. The platform alerts developers of policy violations as they’re writing code. In a similar vein to SCA and SAST, Lacework understands that IaC templates are committed to code repositories and automatically detects new code repositories, identifies IaC files, scans them for misconfigurations, and provides actionable guidance and automated remediation.
Continuous visibility at each stage of development
Lacework can seamlessly integrate with a number of source code management (SCM) tools, continuous integration (CI) tools, or integrated development environments (IDEs). As they code, developers receive clear, automated guidance on how to fix security issues in a familiar language. And, by capturing git history, the platform will always remember who introduced what vulnerable lines of code in case issues need to be retroactively remediated.

The data-driven cloud security platform
Since our founding in 2015, our North Star has been (and will always be) to simplify cloud security for our customers. We do this by ingesting and correlating massive amounts of data from code to build to run — and every place in between — to empower customers to quickly detect, investigate, and respond to risks faster than ever.
In the earliest days of cloud computing, it became clear that this would only be possible by avoiding data silos — by building a cloud security platform. And this expansion into code security is just the next chapter of that same story.
Cloud threat detection. Cloud posture management. Cloud compliance. Cloud vulnerability management. Cloud application and code security. None of these things can be fully realized in a vacuum. They are interdependent upon each other and can only be achieved within a platform that correlates insights across those use cases. From code to runtime and back.
Suggested for you


