Bringing together code and cloud security
Discover and prioritize the most significant code risks using runtime intelligence from the cloud.

Secure code fast
Streamline security assessments for developers and empower security engineers to swiftly assist those in need.

Get precise insights
Reduce time wasted on false positives, close false negative gaps, and prioritize the most impactful risks.

Scale expert reviews
Automatically interpret complex code like an expert, uncovering deep exposures at millions of lines per minute.

Unify security tools
Operationalize security, reduce complexity, make smarter choices faster, and gain visibility into running code.
Software Composition Analysis
Secure open-source software and software supply chain
- Gain continuous visibility of direct and transient dependencies and their associated vulnerabilities
- Prioritize CVEs based on exploitability and impact, and expedite remediation with smart, automated fixes
- Know what third-party software is used and its license requirements with software bill of materials (SBOM)

Static Code Analysis
Automate expert code reviews in minutes
- Empower developers to assess code fast, and give security teams visibility into effective practices
- Accurately analyze call chains and control paths to minimize false positives, and avoid missed weaknesses
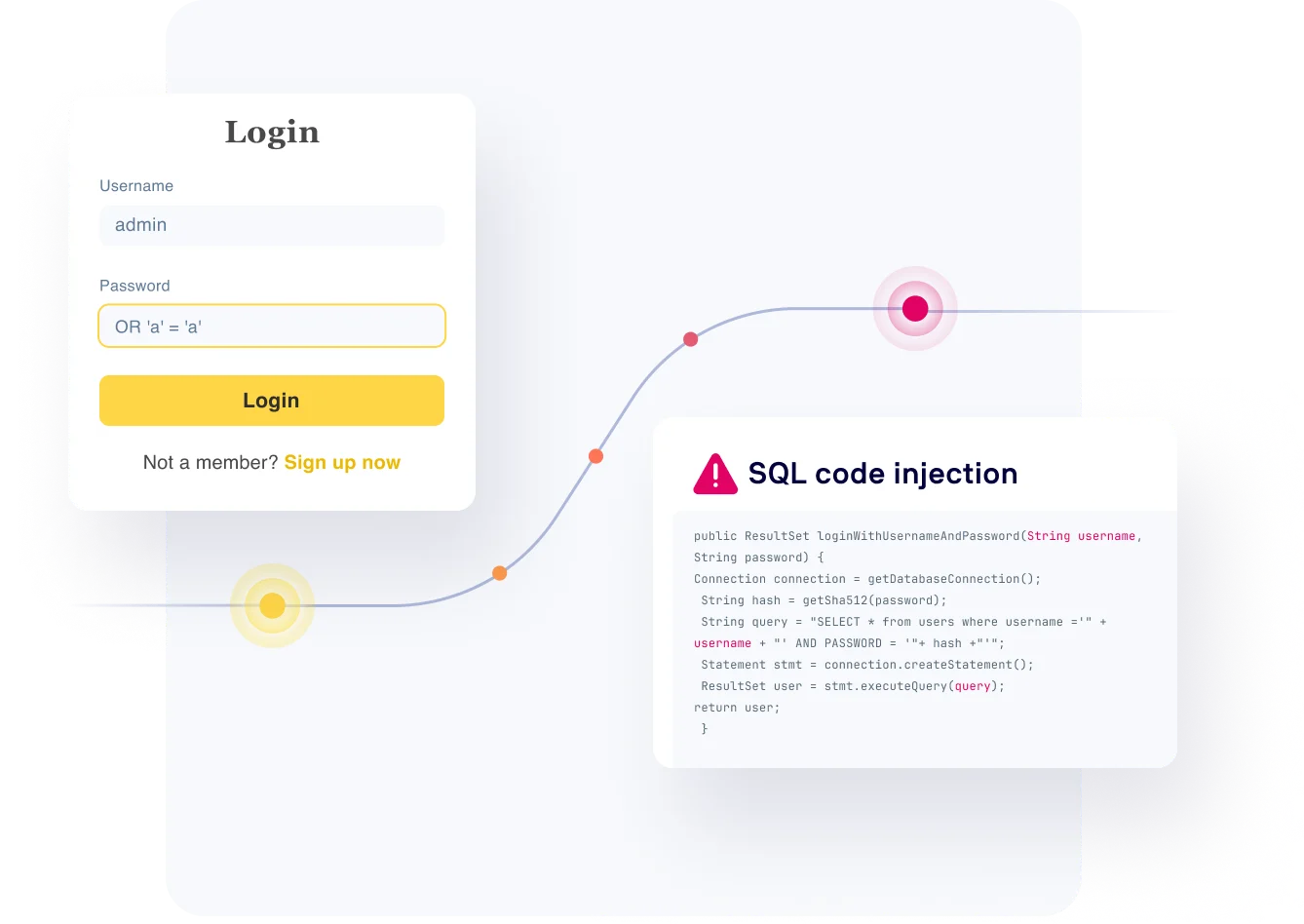
- Pinpoint application weaknesses that may result in SQL injection and other OWASP top 10 related risks
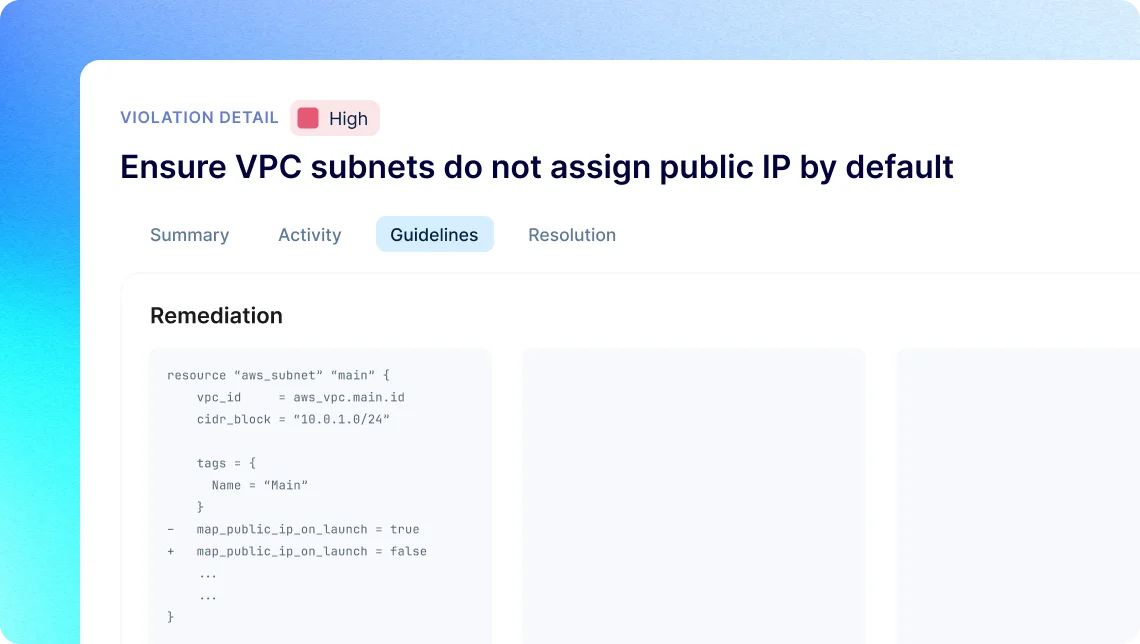
Infrastructure as Code Security
Automate security guardrails for cloud services
- Automatically discover IaC files, identify misconfigured services, and pinpoint the highest risk ones
- Allow developers to secure code fast, address security within their tools, and fix issues with one-click
- Move beyond checklists, effortlessly author custom policies to meet unique and evolving business needs
Common questions
Shift left security, another word for code security, is a practice of embedding security into the early stages of the application development process. This means that vulnerable code is identified and addressed as it is being developed, rather than waiting until testing or deployment phases. By moving security checks earlier in the development process, vulnerabilities can be found and fixed more easily and cheaply. This approach requires collaboration between security teams and developers, and a deep understanding of DevOps automation culture.
Fixing cybersecurity risks during build time is beneficial for several reasons. It’s cost-effective as defect rectification is more expensive in production. Early detection allows prompt risk mitigation, preventing potential major issues. It also avoids service disruptions from exploited vulnerabilities, protecting revenue and reputation. Moreover, integrating security from inception enhances application reliability. While there are merits to testing in production, it shouldn’t replace addressing risks during build time.
Application security stands out in the cybersecurity landscape due to its focus on the security of software applications, including web, mobile, and enterprise software. Its unique approach is proactive, emphasizing on ‘shifting left’ to integrate security early in the software development lifecycle, rather than reacting to incidents post-occurrence. It involves secure coding practices to prevent vulnerabilities and requires continuous monitoring and management for regular updates, patch management, and response to emerging threats. Furthermore, by ensuring the security of critical business applications, it plays a crucial role in maintaining business continuity.