Why active vulnerability detection is a game changer for vulnerability risk management
Open-source software is the foundation of many cloud services and platforms. Whenever you add a new open-source component, or package, into your cloud workload, this also adds other dependent components. Over time, new security vulnerabilities may be discovered, which leaves you with a daunting challenge: determining how to continually track all your open source components, their dependencies, and their vulnerabilities.
The Lacework Polygraph® Data Platform scans all your cloud workloads, identifies all their components, and shows you which components are vulnerable. From that point, the platform suggests how to eliminate those vulnerabilities, a process often called vulnerability risk management.
Lacework recently introduced a new and unique vulnerability risk management capability: the ability to detect what software components you are running (called active) versus not running (called inactive) in your cloud workloads with flawless precision.
Our active vulnerability detection functionality uses a new agent enhancement that detects all package activity and inactivity. It continuously monitors the file system of any machine in the cloud with no visible overhead cost, and near-zero CPU+memory+data volume increases. The monitoring cost is so low that no additional agent budget is needed, and it can be run continuously everywhere.
This capability provides organizations with unprecedented visibility and insight into their cloud workloads. They can find out exactly when and where every package is running. No more guessing, manual investigations, or expensive “debug-style” or “perf-style” workload instrumentations that are problematic in production. Our code-aware agents automatically collect all this data efficiently, safely, everywhere, all the time, in production, and at cloud-scale.
You may be surprised when you see the package activity data for your cloud workloads. Early adopter customers of active vulnerability detection have discovered that most of the packages in their cloud workloads are actually never executed anywhere, at any time.
This level of visibility is crucial because a vulnerable package that is never executed is not a security risk. In fact, a vulnerable package that is inactive (never executed anywhere anytime, is not part of the attack surface of your cloud workload: its execution cannot be hijacked, tricked into leaking sensitive data, or corrupted in any other way, because it is never executed. Therefore, as long as the vulnerable package stays inactive, it is harmless. Fixing it can be safely deprioritized.
Lacework data shows that an average of 65% of all installed vulnerable packages in cloud workloads are never executed on any machine.
To prove package inactivity, it is necessary to monitor all packages all the time, and everywhere. To the best of our knowledge, this new and differentiated capability offered by Lacework has never been available before, either in prior open-source or proprietary agents. Prior agents can track only some package activity; for instance, when monitoring processes related to network connections or traffic (as previously done by the Lacework agent), or when instrumenting workloads for debugging or performance monitoring. But such agents provide only partial monitoring, and are insufficient to prove package inactivity, which requires full package activity coverage. And of course, agentless scanning tools and platforms cannot provide this level of visibility: agentless solutions are blind to package activity.
Lacework active vulnerability detection monitors all package activity on a machine by monitoring its file system in a non-intrusive way. When a process accesses a package file in order to execute it, our agent detects this event and declares its package as active. This data is aggregated locally on the agent, and periodically sent to the Lacework cloud. A lightweight system of file indexes and caches within the agent ensures that the volume of package-activity data stays very low, and as a result, keeps costs down.The runtime instrumentation is also dynamically adjusted so that its cost is extremely low, even when files or packages are executed millions of times per hour. Periodically, the package-activity data sent by all the code-aware agents for a customer account is post-processed, aggregated, and analyzed in the Lacework backend. Customers can then securely access their own data and analysis results in their Lacework account, including through the Lacework UI.
The screenshot below illustrates how Lacework customers can query and search their package-activity data, in conjunction with other parameters already part of the Lacework platform, such as whether these packages contain vulnerabilities and their associated severities, and whether the machines with active vulnerable packages are internet-facing. The combination of all these filters within our risk-based vulnerability score means that customers can reduce 90% of vulnerability noise. It is invaluable in effectively prioritizing vulnerability remediation. Save your valuable time and resources by mitigating only vulnerabilities that pose a true risk, rather than chasing ghosts!
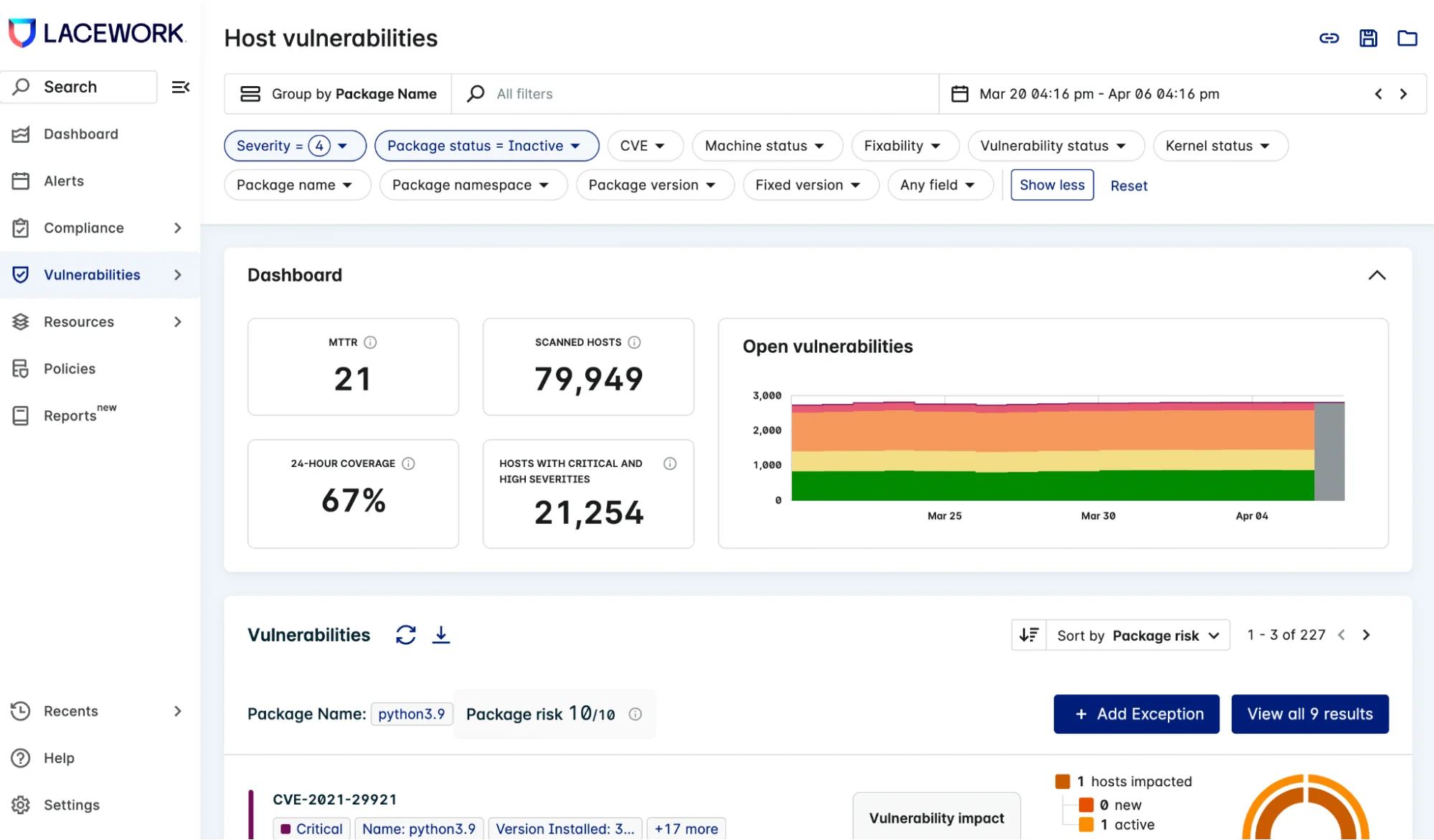
For instance, the Lacework customer example above shows 227 unique vulnerable packages that have never been executed from March 20 to April 6 anywhere in their entire cloud workloads, that are composed of tens of thousands of machines – a real eye opener.
As another example, here are typical results from another customer account, broken down by severity:
Results from 2428 machines from 2023/03/20 to 2023/04/03:
Number of unique packages: 1361
Number of unique ACTIVE packages: 235
Breakdown by severity:
14 Critical, 33 High, 43 Medium, 8 Low, 137 Not vulnerable
Number of unique INACTIVE packages: 1126
Breakdown by severity:
25 Critical, 130 High, 176 Medium, 49 Low, 746 Not vulnerable
Active packages vs total packages: 235/1361 = 17%
Active vulnerable packages vs total vulnerable packages: 98/478 = 21%
Active vulnerable packages vs total packages: 98/1361 = 7%
Inactive vulnerable packages vs total vulnerable packages = 79%This cloud workload contains 1,361 unique packages running on 2,428 machines (including short-lived VMs). It includes 14 active packages with a critical vulnerability. But it also includes 25 packages with a critical vulnerability that have never been executed anytime anywhere from March 20 to April 3 on the 2,428 machines monitored by Lacework agents. Guess which critical vulnerabilities should be fixed next by this customer? You got it.
Additional data about the frequency of package activity is also available. For instance, you can find out what packages are executed daily, weekly, or monthly, and on how many machines, ephemeral VMs or long-running servers, of what sizes, in what microservices, and more. This new data available at your fingertips unlocks all kinds of new analyses, including some that may only make sense for your specific workloads, and to your security or dev team – it is your data, you can do whatever you want with it, and not just for security applications! Imagine the possibilities…
The package-activity data generated by the new active vulnerability detection feature is a game changer for vulnerability risk management. It is transforming the way in which our customers look at and manage risk within their cloud workloads.
Please contact your Lacework account team to be part of the active vulnerability detection public preview, and discover what code gets executed when and where in your cloud. Welcome to the future of cloud security!
Suggested for you