Impactful, end-to-end cloud security with CNAPP
Stop wasting time. Our all-in-one CNAPP integrates data across silos to uncover your most critical security issues.


Fix actual risks
Focus on real, exploitable issues by linking risk data with live workloads.

Find threats faster
Speed up threat detection. Equip SOC teams with the data they need for fast investigation and response.

Regulation ready
NIS2? No problem. Stay ahead of rising regulations with our unified security platform.
DATA-DRIVEN CLOUD SECURITY
Efficient cloud security by breaking down data silos
Your own data holds the keys to protecting your entire cloud. Let Lacework connect the dots for you.
CWPP
Rapidly identify and mitigate hidden threats
- Detect malicious activities, rule-based or not, with our AI-driven anomaly detection
- Quickly assess potential impacts with alerts enriched with posture and identity insights
- Remediate issues fast through a library of integrations with existing workflow tools
CSPM
Detect suspicious activities and automate investigations
- Achieve complete visibility into your multicloud environment with diverse data ingestion options
- Prioritize only active and exploitable cloud issues by tying risk data with running workloads
- Map potential breaches and lateral movement with security graph, attack path analysis, and more
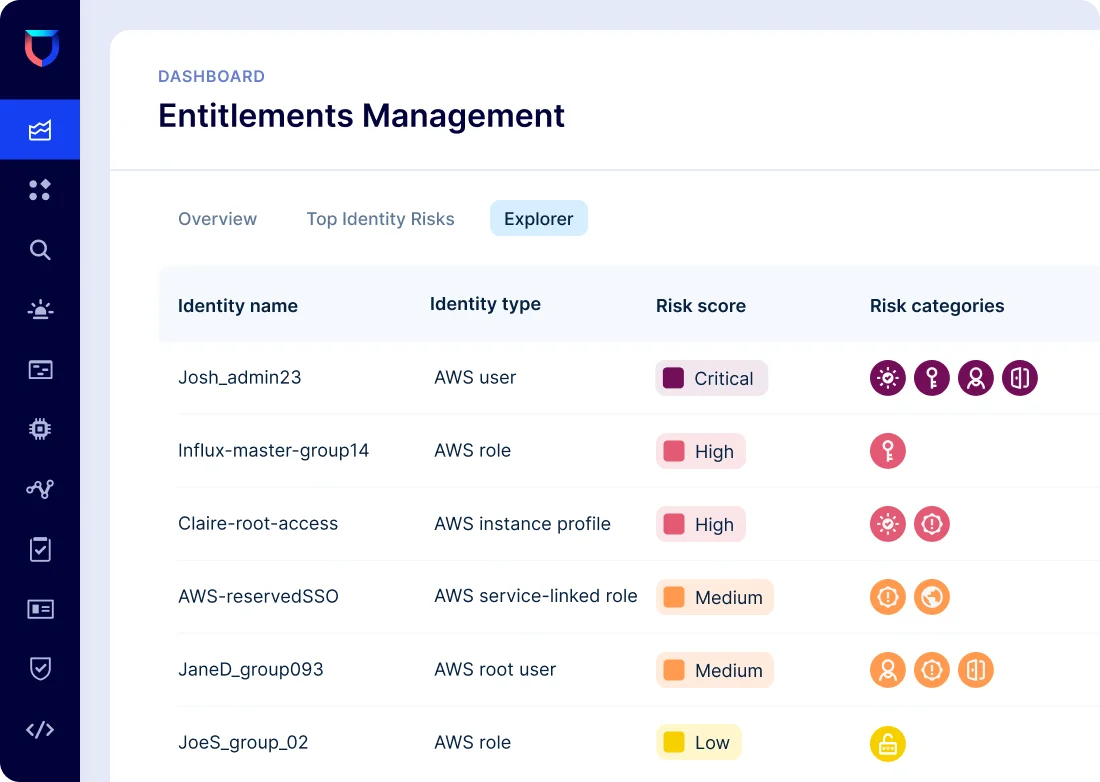
CIEM
Understand which cloud identities pose the greatest risk
- Gain visibility into over-privileged users, resources, groups, and roles across clouds
- Get a custom risk score for each cloud identity, based on relative risk to your unique environment
- Instantly see abnormal behavior tied to risky identities with ML-based anomaly detection
CORRELATION IN ACTION
Detect elusive threats with Lacework Composite Alerts
Composite Alerts combine multiple low severity signals across build time and runtime into a single high severity alert.
Read the 2-pager
"Lacework has freed up my team from spending 2 to 3 hours a day configuring, tweaking, and looking at alerts to less than 15 minutes. It’s freed up so much time to do other things that are security-related."
Mario Duarte | Director of Security
Read case study"With a lot of tools, you get a few thousand alerts, but on an operational level, it doesn’t really work because you’re getting flooded with information. This is the great thing about Lacework. Lacework doesn’t get rid of humans. It actually allows humans to focus on the most important parts."
Kevin Tham | CISO
Read case studyResources & Insights
Featured Insights
Watch Lacework CNAPP in action
On-demand feature demo videos and guided tours

