Protect yourself for Cyber Monday
Cyber threats and attacks tend to pick up around the holidays, particularly those against consumers. But what about attacks involving cloud infrastructure? Lacework Labs had the same question and decided to look at the data.
Before we delve into the details, let’s take a quick inventory of common threats. For end users, it’s usually scams, financial malware, and phishing. But for cloud infrastructure, attackers typically take advantage of a misconfiguration, application vulnerability, or compromised credentials. In both cases the motive is often financial: fraud and cryptomining respectively.
Lacework collects a wide scope of data from customer cloud environments which not only allows for insight into malware and breaches, but attempted attacks and reconnaissance as well. For example brute forcing, exploits, and probing against cloud resources such as Docker, K8s, S3. First we reviewed logs and events involving known bad IP addresses and domains and then for each customer we ranked the top months by total volume of unique attacks. The data revealed (Figure 1) attacks do indeed tend to pick up around the holiday months albeit not dramatically.
Also this was not the case for all customers. In general more customers saw an increase in attack volume around November and December however many also experienced an uptick throughout the year.
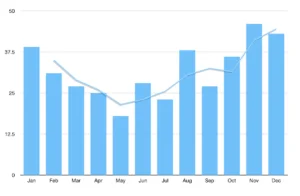
Figure 1. Attack frequency by month. Y axis = percentage of Lacework Customers, X axis = most active months
So what are some practical cloud security precautions you can take around this time of year? One of the most effective is always multifactor authentication (MFA). Failure to implement any MFA protections to your cloud infrastructure increases the risk of successful brute force attacks or stolen credential use. This is especially true during the holiday season since we’ve shown that brute force attacks increase this time of year. MFA is also a universal protection and applies to home users, enterprise and cloud.
Unfortunately attackers sometimes get access to credentials which means accounts must not have any unnecessary privileges. This leads us to our next common sense cloud security precaution – principle of least privilege (PoLP). PoLP defines the idea that any resource should have only the bare minimum privileges necessary in order to perform a task. PoLP can be particularly complicated in cloud environments given that many attacks can be successful with limited privileges. In AWS, there are thousands of IAM tasks which can just convolute things even more.
A good starting point however would be to avoid wild card permissions in your managed policies and follow PoLP when attaching policies to a specific entity. For example, do attached policies contain only the permissions that are absolutely necessary for an entity to complete its function?AWS IAM Access Analyzer can also assist by identifying unintended access to your resources and data. Account management comes into play as well when reducing attack surface. Are you removing or updating accounts when employees leave or change positions?
Automated cloud security vendors can provide a level of visibility into your infrastructure that’s just not possible with other solutions. For example credential theft is typically discovered when an account’s behavior deviates from the norm. This could be overlooked around the holidays when many employees are on vacation. In this case automation can alert on anomalous behavior.
There is always a sufficient volume of attacks throughout the year to exploit an existing vulnerability. An increase in targeting of low-hanging-fruit may just result in a quicker infection time. Successful attacks are also more dependent on a particular environment or timeliness of software updates and patching as opposed to seasonality.
Ultimately, whether it’s the holiday season or not, it’s important to protect your network and data. As the world of commerce braces for another Cyber Monday, we wish you happy and safe shopping. If you want to hear more, be sure to follow Lacework Labs on LinkedIn, Twitter, and YouTube to stay up-to-date on our latest research.
Copyright 2021 Lacework Inc. All rights reserved.
Categories
Suggested for you


