Keksec & Tsunami-Ryuk
Cloud Security Researcher – Lacework Labs
Key Takeaways
- Keksec is now leveraging a new Tsunami DDoS malware dubbed “Ryuk” (not the ransomware family)
- The group has updated their DGA algorithm used by the Necro python malware
- An inventory of Keksec’s malware distribution infrastructure is provided
- New persona details are included
Keksec, aka Necro, & Freakout, is a prolific actor targeting cloud infrastructure for the purposes of carrying out crypto mining and DDoS operations. The group recently made it into the news again by expanding their infrastructure and capabilities to include new exploits and propagation techniques. This blog takes a comprehensive look at Keksec’s intrusion infrastructure and includes previously unreported content such as the use of a new Tsunami variant named Ryuk, new DGA algorithm, and new persona details.
Necro – DGA
Necro is the name for Keksec’s Python IRC malware and botnet, with the latest version documented by Talos. The malware is characterized by its unique obfuscation that leverages a combination of zlib compression and a multibyte XOR key. In March 2021, Lacework Labs released a script which also decodes this latest variant.
Significant updates were made in the most recent version to include exploits targeting Vesta Control Panel, ZeroShell 3.9.0, SCO OpenServer 5.0.7, and VMWare vCenter (CVE-2021-21972). The malware now also attempts to propagate via SSH brute-forcing. A new DGA algorithm was also included which is very similar to the previous necro version but with a couple of small updates to the see and random-range parameters.
| DGA component | old | new |
| seed | 0x7774DEAD | 0x7228827A |
| randrange parameters | range(random.randrange(10,19)))).lower() | range(random.randrange(8,19)))).lower() |
Two DGA domains have been seen in the wild. There are a total of 255 possible domains. Previously keksec only used the first few domains before changing the DGA scheme so it’s possible that will be the case this time
- ngiwge486ln9daoo.hopto.org
- can6dodp.servepics.com
This script may be used to generate these new DGA domains.
Malware Distribution Infrastructure
Keksecs infrastructure is primarily composed of 20 hosts and is structured around URI path names in download URLs. The most frequently used of these include ‘’/Ryuk/’,’/Simps/’ and ’/S1eJ3/’. Examples:
- http://107.172.156.158/Ryuk/ur0a.x86_64
- http://206.81.26.46/Simps/mipsel
- http://23.95.80.200/SimpsX/m68k
- http://45.144.225.65/S1eJ3/IObeENwjspc
The following table lists these hosts which are ranked by the malware file count (from 2021-01-01 – 2021-06-09 ). Some hosts are unique to URI paths mentioned above while others overlap.
| Host | ASN | country | Hosted malware count | URI Path name(s) |
| 195.133.40.24 | “SPDNet Telekomunikasyon Hizmetleri Bilgi Teknolojileri Taahhut Sanayi Ve Ticaret A.S.” | Russia | 235 | S1eJ3 & Simps |
| 45.145.185.83 | 213035:”Des Capital B.V.” | Netherlands | 81 | S1eJ3 |
| 45.14.224.127 | 62068:”SpectraIP B.V.” | Netherlands | 55 | Ryuk & Simps |
| 185.224.129.235 | 62068:”SpectraIP B.V.” | Netherlands | 54 | Ryuk & Simps |
| 185.224.129.224 | 62068:”SpectraIP B.V.” | Netherlands | 40 | Simps |
| 45.144.225.65 | 35913:”DEDIPATH-LLC” | United States | 39 | S1eJ3 |
| 23.95.80.200 | 36352:”AS-COLOCROSSING” | United States | 34 | fagggotbaggot, Simps, SimpsX |
| 45.144.225.96 | 35913:”DEDIPATH-LLC” | United States | 29 | S1eJ3 |
| 45.153.203.124 | 213035:”Des Capital B.V.” | Netherlands | 18 | S1eJ3 |
| 206.81.26.46 | 14061:”DIGITALOCEAN-ASN” | Germany | 15 | Simps |
| 45.14.224.197 | 62068:”SpectraIP B.V.” | Netherlands | 15 | Simps |
| 185.203.116.7 | 44901:”Belcloud LTD” | Bulgaria | 14 | S1eJ3 |
| 172.245.36.128 | 36352:”AS-COLOCROSSING” | United States | 13 | S1eJ3 |
| b0tz.xyz | NA | NA | 8 | Simps & SimpsX |
| 107.172.156.158 | 36352:”AS-COLOCROSSING” | United States | 5 | Ryuk |
| 45.14.224.200 | 62068:”SpectraIP B.V.” | Netherlands | 4 | Simps |
| 164.90.164.132 | 14061:”DIGITALOCEAN-ASN” | Germany | 3 | S1eJ3 |
| 134.122.78.91 | 14061:”DIGITALOCEAN-ASN” | Germany | 1 | Simps |
| 192.236.146.182 | 54290:”HOSTWINDS” | United States | 1 | Ryuk & S1eJ3 |
The most active host continues to be IP 195.133.40.43 which is mostly being used in the ‘S1eJ3’ portion of the infrastructure to deliver Keksec’s Tor-based Tsunami variant. Lacework Labs detailed this malware in a blog – ‘The “Kek Security” Network. At the time of that analysis, Keksec was using .onion c2 host vp3te7pkfczmnnl.onion, however new specimens are using host dimumdjenyy4jwlc.onion along with the same cipher key used for decryption:
%q*KC)&F98fsr2to4b3yi_:wB>z=;!k?”EAZ7.D-md<ex5U~h,j|$v6c1ga+p@un
Tsunami-Ryuk
A new component in the Keksec malware inventory is yet another Tsunami-based DDoS malware dubbed ‘Ryuk’. A total of 83 specimens were identified with the first appearing in mid May and going into June . This name is not to be confused with the Ryuk ransomware and is most likely a reference to the fictional character from the manga series ‘Death Note’. Additionally, there are indications that the malware is being used as a payload in Necro’s SSH brute-forcing campaigns, as there are comments in VirusTotal reporting that the files were observed in SSH honeypots.
There are several different variations of Ryuk and are hosted by the previously described ‘Ryuk’ component of the keksec infrastructure. Many specimens are UPX packed and also leverage a simple encoding method to obfuscate C2 IPs, as well as a message that is written to a log file. The encoded version is statically observable as the following string:
Ymnx2Ij{nhj2Nx2Nskjhyji2G~2W~zp2Gtysjy2Nsxyflwfr?Ezw5fdInxhtwi?ZW5F(76>>2W~zp(9;:7
The decoded message reveals Instagram and Discord accounts.
This-Device-Is-Infected-By-Ryuk-Botnet-Instagram:@ur0a_Discord:UR0A#2199-Ryuk#4652
The function in the binary responsible for the decoding is named ‘util_encryption’. The routine simply decrements each character in the string by 5. Examination of the function xrefs revealed that it is leveraged decoding the log file contents, c2, and DDos commands. Searching on this artifact in VirusTotal revealed a number of other Tsunami variants with a similar decoding routing of the same name but with a decrement value of 1 instead of 5.
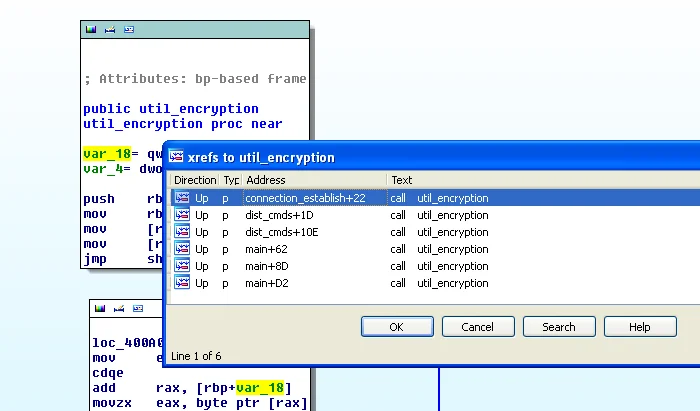
|
Figure 1. Tsunami-Ryuk Decoding Routine IDA Pro
The following python script may be used for decoding these Ryuk configurations as well as for other malware using similar methods.
1
2
3
4
5
6
7
ryuk_strings = ['Ymnx2Ij{nhj2Nx2Nskjhyji2G~2W~zp2Gtysjy2Nsxyflwfr?Ezw5fdInxhtwi?ZW5F(76>>2W~zp(9;:7','9:3693779367<']
for str_ in ryuk_strings:
decoded_ = []
for s in str_:
decrement = chr(ord(s) - 5)
decoded_.append(decrement)
print ''.join(decoded_)Decoding Script for Ryuk configs
There are a few other Ryuk variants, with plaintext versions of the log file contents and c2 IP addresses. This message is consistent with Keksec’s habit of self-attributing malware and infrastructure.
This Device Has Been Infected by Ryuk Botnet Made By ur0a And Keksec Group 🙂
Additionally, the ‘ur0a’ handle is also used for several of the Ryuk payload names. For example:
- ur0a.mipsel
- ur0a.mips
- ur0a.i686
Social Media
Kekec, similar to TeamTNT is notorious for self-promotion. This was illustrated in the Ryuk malware artifacts listing social media information for Discord, and Instagram. While the Discord account was a dead end, the Instagram account is online.
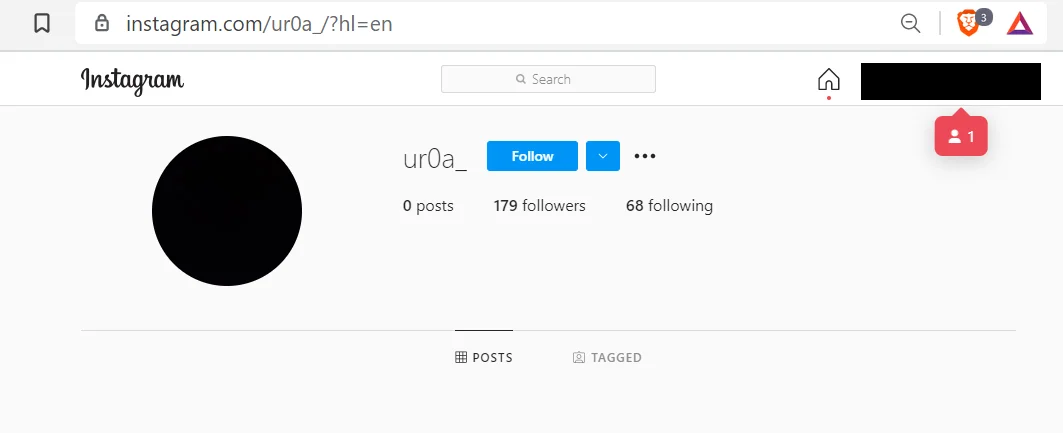 |
Figure 2. Instagram Account of Actors
The ur0a_ Instagram account does not have any posts however several accounts followed by ur0a_ are of interest. One of these is named “hellabootersonbotnet”. On May 10th, this account posted a screenshot of the Necro IRC control channel. This was identified as Necro by the Irc messages, especially the MB RAM total and [HAX| artifacts in the IRC messages. These are observable as formatting strings in the Necro source code. Additionally, the account mentions Freakout as a comment to the post – ‘Freak out on top’.
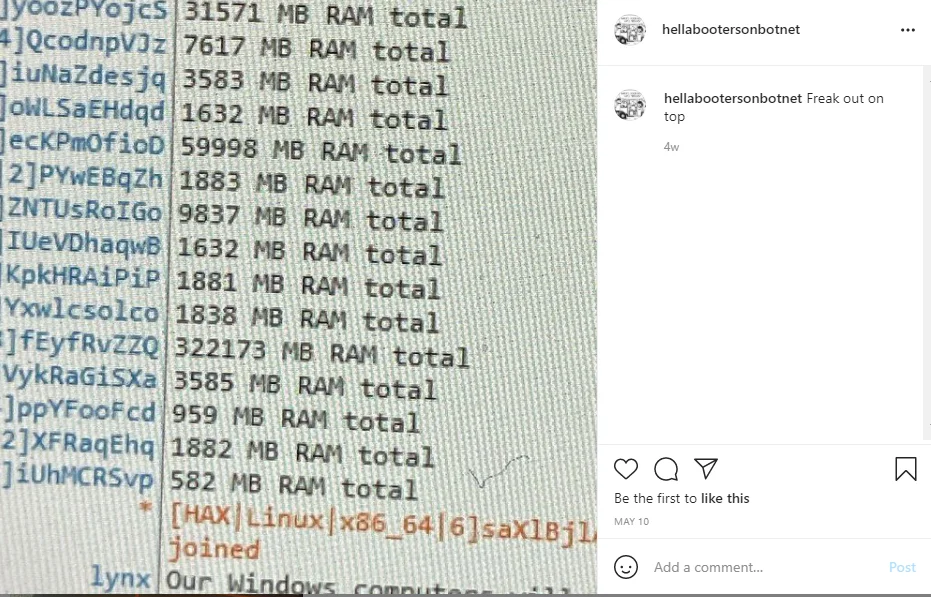 |
Figure 3. Necro IRC bots – “hellabootersonbotnet” Instagram
Keksec frequently updates their toolset and suite of exploits making them an evolving threat. Fortunately, their habit of self-attributing malware and infrastructure makes for easier tracking. Indicators and tools for this activity are available on our GitHub. If you found this blog useful then please share and follow us on LinkedIn and Twitter!
Categories
Suggested for you


