How to detect CVE-2023-4863: A libwebp out-of-bounds memory write
What is CVE-2023-4863?
CVE-2023-4863 is an out-of-bounds write access vulnerability impacting libwebp that was disclosed by Google on September 11, 2023. This library is used to encode and decode images in the WebP format. WebP is a relatively new image format that is optimized for the web and was popularized by Google through the Chrome browser.
CVE-2023-4863 was also disclosed by Google as CVE-2023-5129 (Critical, CVSS v3 score of 10/10), which was later marked as a duplicate and discarded. CVE-2023-4863 has a CVSS v3 score of 8.8 and is rated as high severity.
The vulnerability was remediated in libwebp 1.3.2 and updates are available through standard package managers. This vulnerability can only be remediated by upgrading because there are currently no mitigations available. As always, adopting a defense-in-depth strategy can help reduce the blast radius of any potential exploitation of this vulnerability.
How to detect CVE-2023-4863 with Lacework
Lacework can detect CVE-2023-4863 in OS packages and language libraries, on hosts and containers.
Search for your vulnerable assets
Lacework allows you to search for a CVE across all your clouds through its API and web console. In the Lacework web console, go to Vulnerabilities to look for CVE-2023-4863 or “libwebp” in hosts and containers. You can search for the assets affected by that CVE, or for the vulnerability itself. In this example, CVE-2023-4863 was found in the libwebp library installed as an OS package, and the pillow Python library.
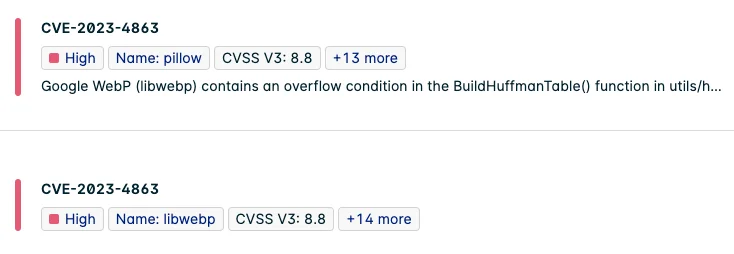
Figure 1: CVE-2023-4868 found in the libwebp OS package and pillow Python library
This vulnerability is present in several open-source container images:
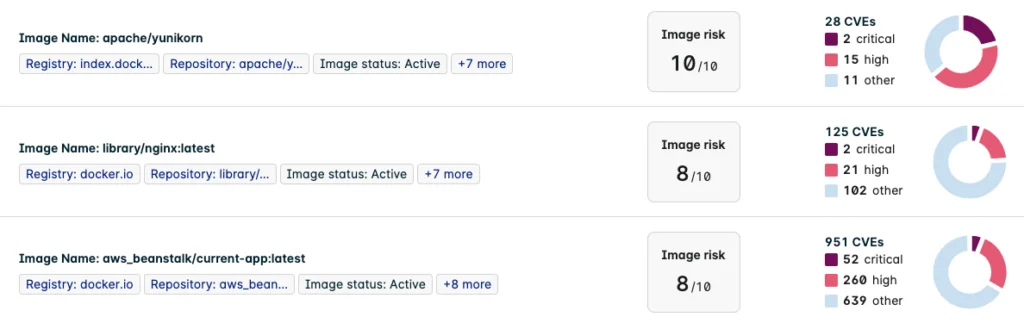
Figure 2: CVE-2023-4868 found in popular open-source containers hosted at docker.io
Lacework automatically reassesses all active hosts and containers. You don’t need to rescan your assets to find new vulnerabilities such as this one.
Prioritize which assets to fix first
You may be overwhelmed by the number of assets that include this high CVE. But not all are equally at risk: on many workloads, this library is not actually used. Workloads directly exposed to the internet are more susceptible to exploitation.
Lacework provides information about active and inactive packages and libraries, and exposure to the internet through the API and the web console. In the Lacework UI, use the filters shown in Figure 3 to find your most exposed workloads:
Figure 3: Filter workloads with active vulnerable packages and exposed to the internet
Customers can also use a more holistic approach in the form of the Lacework risk score that takes multiple attributes into consideration (all vulnerabilities, exploits available, active packages, etc.) to prioritize which assets to remediate first.
Get alerts for critical vulnerabilities
Lacework users can set up alerts to take a more proactive approach to responding to newly discovered critical severities. Users can set a Slack notification for critical vulnerabilities, send these details directly to Jira, ServiceNow, or other applications that Lacework natively integrates with.
CI/CD integration
Now that CVE-2023-4863 has been identified, users should ensure that none of their container images are affected by this vulnerability. Integrate the Lacework inline scanner to your CI or CD system to block the deployment of container images that contain high or critical fixable vulnerabilities. You can find more details in our documentation.
Remediating CVE-2023-4863
Upgrade all packages and libraries flagged with vulnerability CVE-2023-4863, or remove them if they are not used. Upgrade libwebp to version 1.3.2 or newer.
Suggested for you


