An overview of Living Off the Land (LOTL) attack techniques
Living Off the Land (LOTL) attacks have emerged as an advanced attack vector that all organizations need to understand and defend against. Unlike traditional malware, LOTL techniques exploit trusted system tools already present in the environment, making detection incredibly difficult. To protect critical systems and data, security teams must grasp the nuances of LOTL methods being actively utilized by attackers. This article will provide an overview of the major LOTL technique catalogs, highlighting how seemingly benign binaries can be weaponized and explaining the unique challenges of safeguarding both Windows and Linux environments. Whether you’re defending enterprise networks or securing cloud infrastructure, understanding these subversive attacks is essential for every security professional.
LOLBAS: Living Off The Land Binaries, Scripts and Libraries
LOLBAS is widely regarded as the original catalog dedicated to documenting Living Off the Land techniques. This project focuses specifically on cataloging Microsoft-signed binaries that can be exploited for malicious purposes on Windows systems.
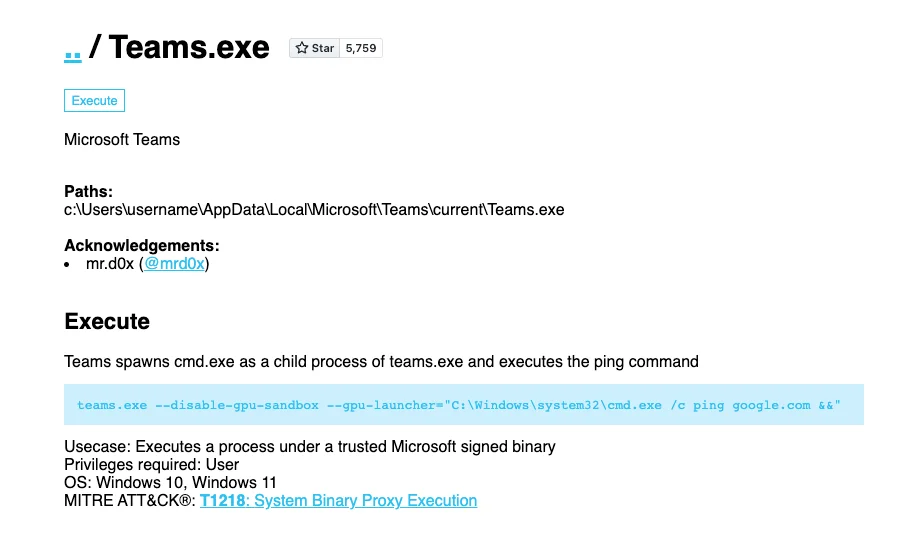
Utilizing an application like Microsoft Teams can be particularly advantageous for attackers aiming to bypass automated security measures. For instance, it’s possible to spawn a child process using Microsoft Teams. To an incident responder, such activity might immediately raise red flags as suspicious. But from the perspective of automated detection systems, Teams is a trusted, Microsoft-signed binary and would typically be considered safe.
Figure 1: Applications like Microsoft Teams can be particularly advantageous for attackers aiming to bypass automated security measures
GTFOBins: Get the **** Out Bins
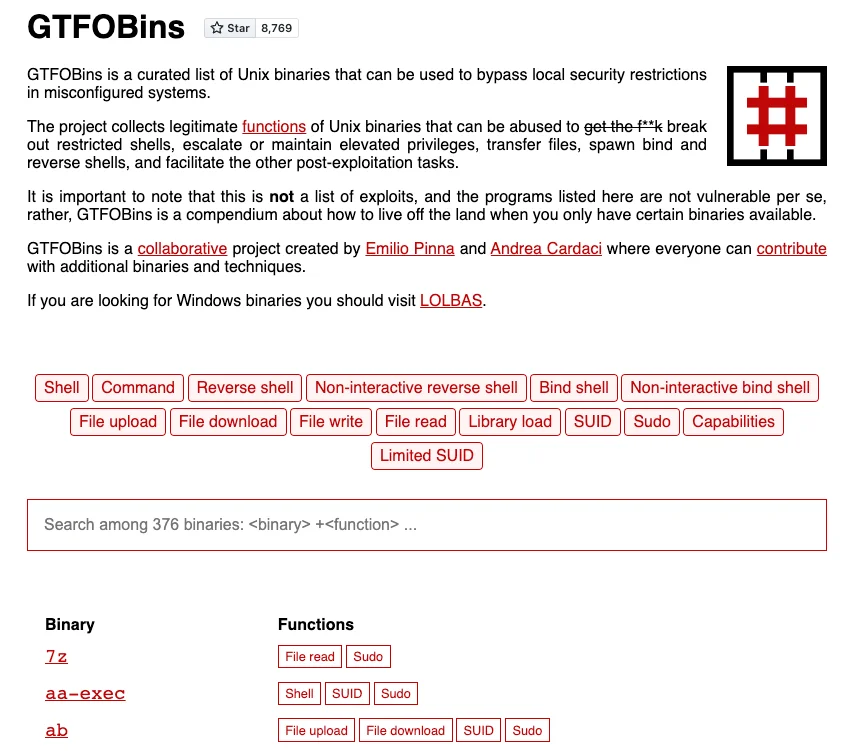
GTFOBins was inspired by the maintainers of LOLBAS and focuses on UNIX binaries. The overall concept remains the same (i.e., how known binaries are abused) but the specific approach differs between Windows and Linux systems.
On Windows, most user activities are conducted through graphical user interface (GUI) applications. Rarely would one find a need to execute Teams.exe from the command line, much less spawn a child process like cmd.exe.
Defending against LOTL abuses in Linux environments is much more difficult. The exploitation often involves command-line utilities such as cp and cat — tools that are integral to daily operations.
Figure 2: GTFOBins focuses on UNIX binaries
LOLDrivers: Living Off The Land Drivers
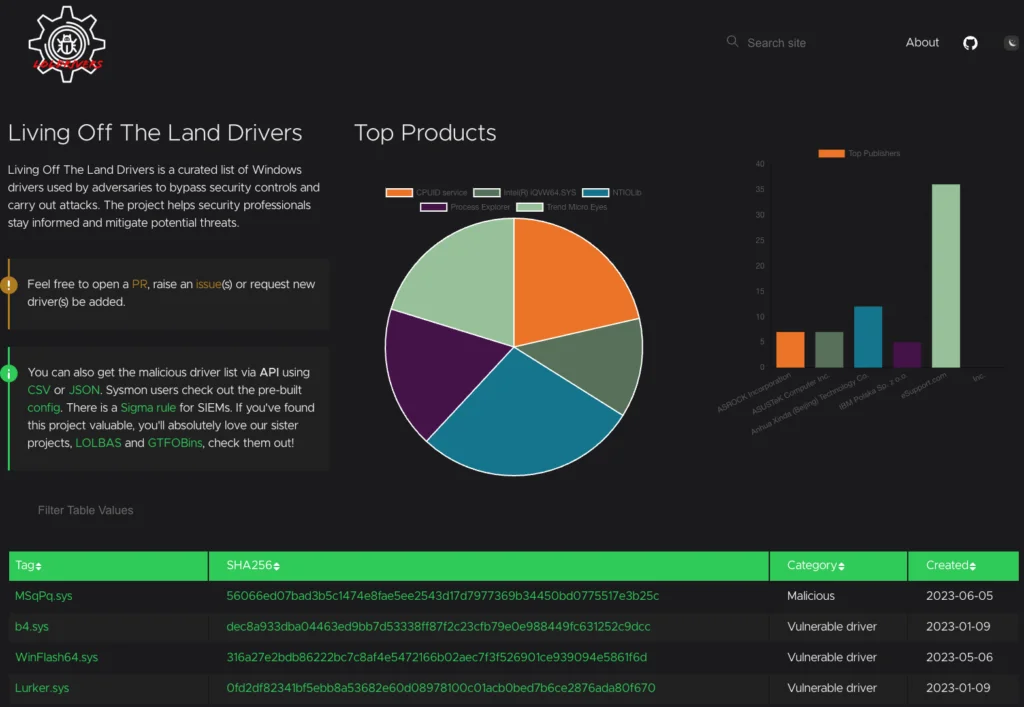
LOLDrivers is a curated list of signed Windows drivers with known vulnerabilities or that are outright malicious.
Figure 3: LOLDrivers is a curated list of signed Windows drivers with known vulnerabilities or that are outright malicious
Drivers, in essence, communicate with hardware components — like changing LED colors on a motherboard through a GUI application. This application, or client, interfaces with the hardware’s driver to enact changes.
One key thing to understand about drivers is the concept of the DriverEntry routine. Think of it as the starting point of a driver, similar to the main (function in C-like programming languages). This routine is responsible for initiating the driver and exporting entry points for various dispatch routines, which are essentially functions within the driver development realm. An example of interaction with these dispatch routines is through the Win32 DeviceIoControl()function, employed by userland applications for tasks such as altering LED colors on peripherals.
The crux of the vulnerability lies in how drivers, which operate with elevated system privileges, can be exploited through these dispatch routines. A flaw in the logic of a dispatch routine, such as improper handling of memory addresses for executing tasks, can open the door for attackers to redirect these routines to execute malicious code instead.
The inherent risk is magnified by the privileged access drivers have within a system. However, it’s worth noting that not all drivers can be maliciously loaded onto a system; since Windows Vista, only signed drivers are permissible, and with Windows 10 (version 1607 onwards) imposing even stricter signing requirements. This creates a hurdle for attackers, though it may not be insurmountable for organized groups.
The following resources are helpful for learning more about the specifics of driver development and exploitation techniques:
- Writing Dispatch Routines – Windows drivers | Microsoft Learn
- GitHub – hfiref0x/KDU: Kernel Driver Utility
- Exploiting System Mechanic Driver – VoidSec
LOLOL: Living Off the Living Off the Land
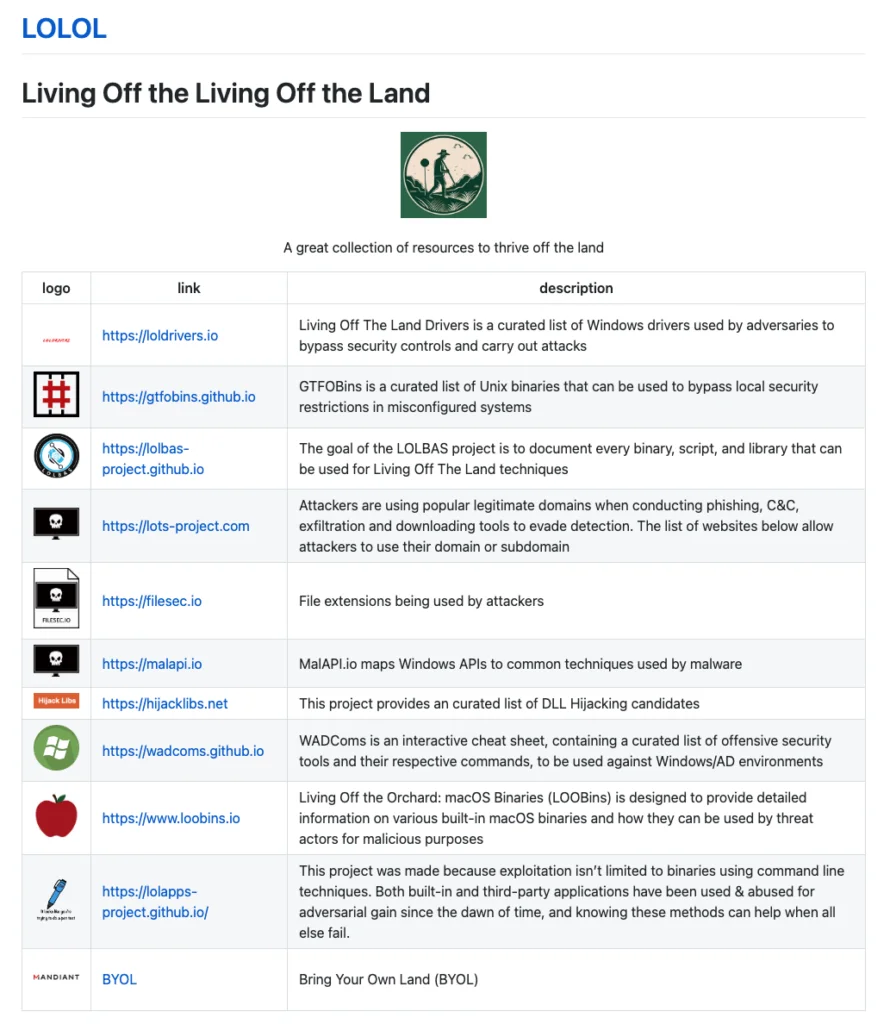
LOLOL is a catalog of catalogs.
Figure 4: LOLOL is a catalog of catalogs
There are many different philosophies and opinions on what should be included in such a catalog.
For instance, the MalAPI catalog, which maps Windows APIs to common LOTL techniques, includes the sleep() function as an evasion technique. While some may view this as a stretch, malware authors can utilize it to “bypass” malware detection sandboxes by delaying execution, leading the sandbox to inaccurately conclude the application is benign.
Similarly, the GTFOBins catalog lists netcat for network access use, which arguably aligns with the intended purpose of the netcat binary. The LOLDriver project’s approach goes beyond merely listing binaries; it provides actual drivers for reverse-engineering, along with detection rules (e.g., YARA, SIGMA, and Sysmon) for defenders to benefit from programmatically. While LOLBAS offers similar features, including mappings to the MITRE ATT&CK framework, it is not as comprehensive as LOLDrivers, likely due to the inherent challenge of providing such features for built-in Windows and Linux binaries or Windows APIs.
Learn more about LOTL
From LOLBAS to LOLDrivers and beyond, LOTL techniques empower attackers with diverse options tailored to various platforms and use cases. While daunting to defend against, awareness of the specific binaries and weaknesses being exploited is the first step. Cataloging and sharing techniques, as the projects covered here have done, enables defenders to implement targeted detections and controls.
To learn more about LOTL, check out our step-by-step guide on how to protect containers from Living Off the Land (LOTL) attacks. If you’re interested in learning how Lacework can help protect your organization from attacks like these, please reach out to us.
Suggested for you