How Lacework detects each attack technique on the Kubernetes threat matrix
Microsoft’s threat matrix for Kubernetes offers a detailed framework outlining potential security risks associated with Kubernetes deployments. While this matrix provides clarity on what to watch out for, translating that knowledge into practical defense strategies isn’t always straightforward. In this blog, we explore how the Lacework platform helps cloud users effectively detect Kubernetes threats and mitigate them promptly.
Kubernetes threats and the role of MITRE
MITRE publishes attack matrices, which are widely used in the security industry to classify security events into different stages of an attack, for multiple environments. The matrices also help companies ensure they have security countermeasures to cover attacks. There is no official threat matrix for Kubernetes; however, Microsoft published its own version of the threat matrix for Kubernetes in 2020 and a revised version in 2021. While not official, it’s a helpful tool for understanding the potential risks specific to Kubernetes. See the matrix below (Figure 1).
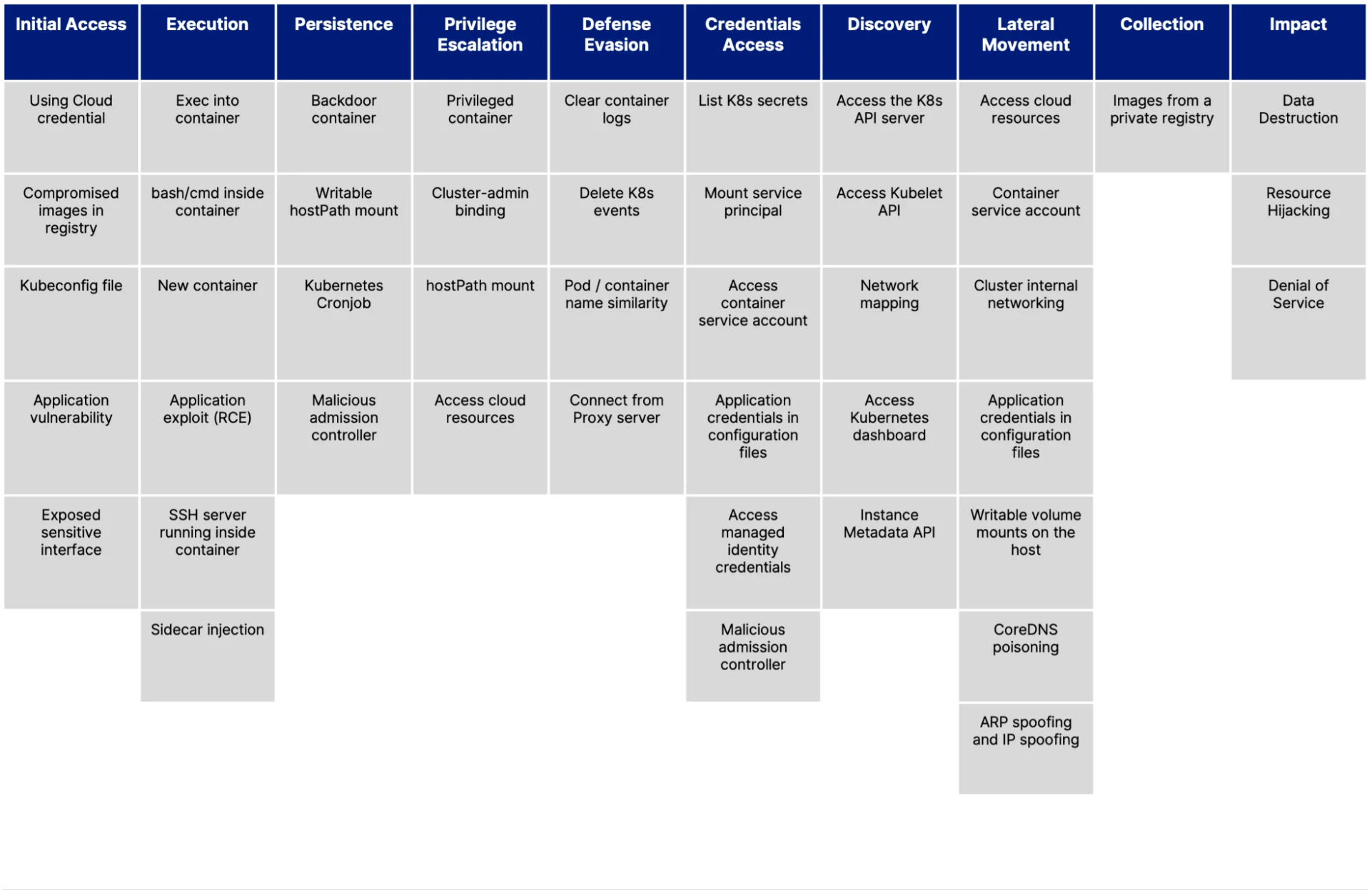
Figure 1: The unofficial threat matrix for Kubernetes (Source: Microsoft)
Comprehensive coverage from Lacework
Microsoft’s threat matrix classifies attacks into 10 stages, from “Initial Access” to “Impact” (e.g., breach). It’s important to note that not all attacks will use techniques from all 10 stages. For example, there might not be a lateral movement to expand the scope of the impact.
It is critical to have a security solution for Kubernetes that can detect
attack techniques across as many stages as possible. Because these attack
techniques occur at different layers of Kubernetes (container, node level,
Kubernetes API, cloud, etc.), an effective tool must monitor many different
aspects of Kubernetes through a single pane of glass, including:
- Network connections and processes that rely on an agent for complete visibility inside the containers
- Kubernetes resources that rely on Kubernetes audit logs or an admission controller
- Cloud access that requires visibility into cloud activities and configuration
To be effective, tools must also be able to scale to process millions of events given the ephemeral nature of containers. The Lacework platform processes millions of observations to find the most relevant security events for customers. To do so, it incorporates several security components and techniques:
- The agent: A Kubernetes daemonset that provides visibility into all processes running in the containers and on the nodes, including network connections
- Kubernetes audit log monitoring: Tracks all new resources (workloads, K8s RBAC, Network exposure, etc.)
- Kubernetes compliance (e.g., the CIS Benchmark for Kubernetes): Highlights unsafe configurations
- Vulnerability management: Provides deep insights into all packages and libraries installed in a container image
- Cloud audit log monitoring: Uses cloud log streams (e.g., the AWS Audit Trail) that detect user activities and access to sensitive cloud resources
Importance of continuous monitoring
The importance of continuous monitoring becomes obvious when compiling the data: agent and the Kubernetes audit log monitoring cover 37 of the 45 techniques (82%). Traditional security posture management tools, such as vulnerability and compliance management, play a small role as each focuses on hardening Kubernetes clusters, not detecting live attacks.
Lacework provides a comprehensive security solution for Kubernetes, which includes hardening controls from code to runtime. It can detect attacks at all three layers: hosts, containers, and cluster.
To learn more about securing Kubernetes and containers, read our ebook, 10 security best practices for Kubernetes.
Suggested for you


