Are you compromising data privacy with your security vendor?
Our “three tenets of trust” philosophy for private by design
Security, privacy, trust. These are fundamental ingredients that most consider the cornerstone of protecting one’s critical data, systems, and infrastructure. So, of course, all cloud security vendors prioritize these aspects, right? Unfortunately, that’s not the case.
Each security vendor handles, stores, and protects your data differently — and some of their standard practices might surprise you.
Do you know how your security vendor approaches customer privacy? At Lacework, believe ALL customers (not just highly regulated ones) deserve the most secure deployment model by default — that’s why our agentless workload scanning is private by design, incorporating known industry ‘privacy by design’ principles.
Lacework has designed our agentless scanning around three fundamental tenets of trust. Here’s a deep dive into each.
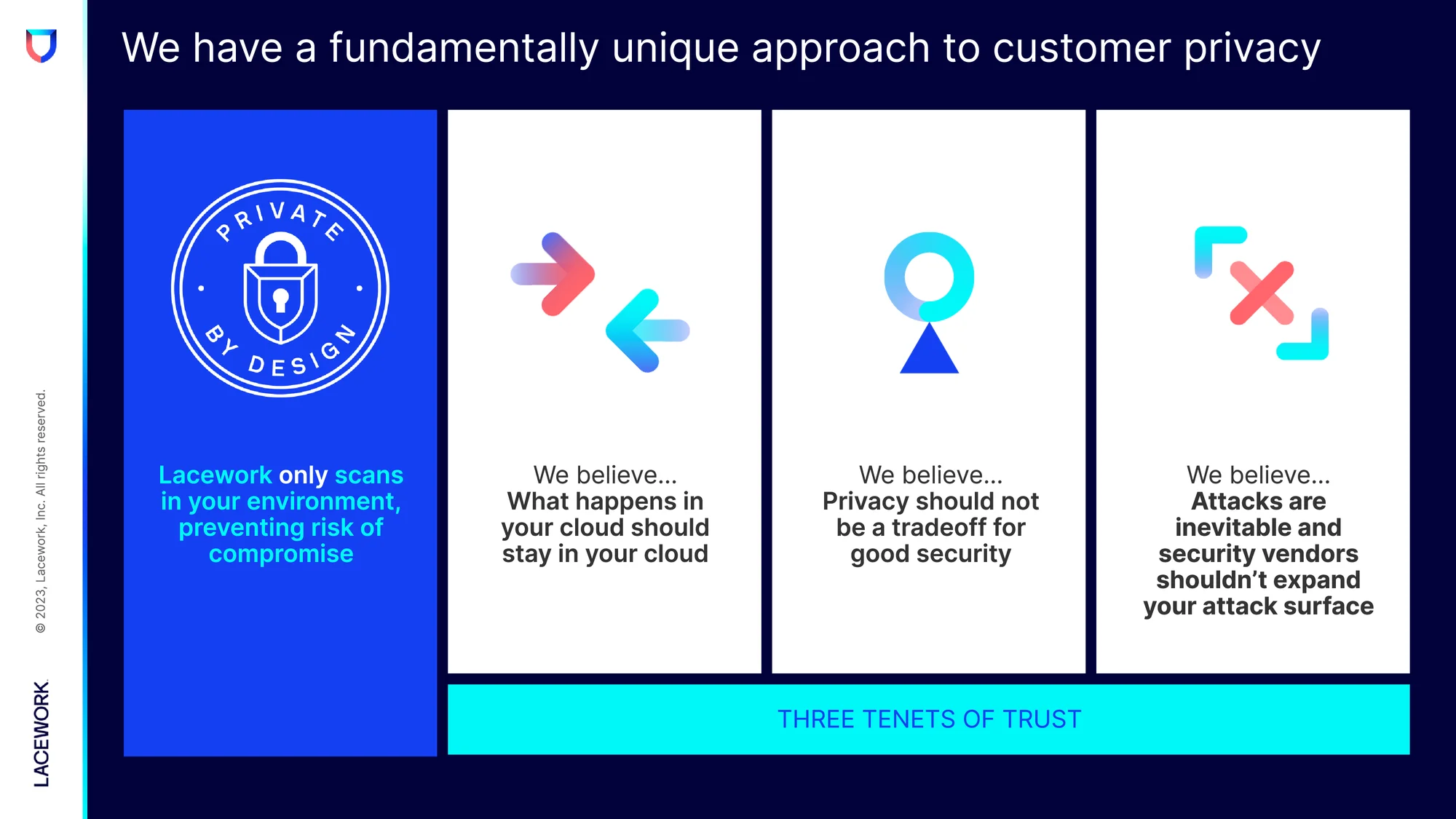
1. What happens in your cloud should stay in your cloud
Which permissions have you granted your vendor?
Your cloud, your data. Do you know which permissions you’ve granted your cloud security vendor? Many vendors ask users to link their cloud accounts and give them access to create and export snapshots of infrastructure data volumes. Such broad permissions allow vendors access to almost anything that could reside on your cloud infrastructure filesystem. It’s crucial to ensure your provider isn’t one of those with this default setting, which puts your data and potentially your customers’ data at risk.
Where is your data?
Your data’s location is vital to privacy. If you give your security vendor access to create snapshots of your data, check if you are also allowing them to move those snapshots out of your environment. While it’s a security best practice to keep your data in your own environment, some vendors’ agentless workload scanning export it outside of your environment for analysis. Why does this matter? If a vendor with export permissions gets compromised, the implications to your environment can be severe. Attackers could exploit these permissions, access every account, extract data, and potentially execute targeted assaults. Imagine those snapshots containing your essential credentials — thus providing an open gate for attackers to infiltrate your systems directly.
Private by design: The Lacework approach
Lacework agentless workload security scans your data and reads analysis results only within your cloud environment, ensuring that your data doesn’t leave your account. This means that even in the unfortunate event of a breach of the vendor, your data (and your customers’ data) remains safe.
Can other security vendors say the same for their agentless scanning? We suggest you ask them directly if they export snapshots out of your cloud account. If they do, it’s a huge red flag your privacy and security team should be aware of, because if they get breached, potentially you could be as well.
Beware of alternative solutions
As other security providers continue to realize the importance of keeping customer data in the customer’s environment, they’ve tried to come up with workarounds. One that we’ve seen recently: the security provider may suggest that customers use their company’s own cloud infrastructure and permissions to scan workloads so data doesn’t leave the customer’s environment. But there’s a catch.
When customers deploy these solutions, they often are faced with two issues. One is the potential for visibility gaps if the scanning infrastructure isn’t deployed in every single region of each of your cloud providers. Without the scanning infrastructure in a particular cloud region, customers may not be able to scan workloads, whether they created them or they were created by threat actors (e.g., during cryptomining attacks).
The second is that a certain security vendor will require the ability to create, manage, and destroy the scanning infrastructure on a customer’s behalf. This means creating an IAM role that allows an external party very broad permissions into your cloud account. This alternative to maintaining data privacy doesn’t seem like a step in the right direction, as your attack surface is once again increased.
2. Privacy should not be a tradeoff for good security
Ensuring compliance without compromising privacy
Regardless of your organization’s size or industry, complying with privacy regulations is critical. For example, the General Data Protection Regulation (GDPR) Article 25 requires companies to incorporate privacy requirements from the first stages of product and service design in order to protect customer data.
If your security solution is exporting your data, not only is privacy potentially compromised, but you might also jeopardize complying with GDPR and other international data or privacy standards. That’s why it’s critical to understand these regulations and ask the right questions to make sure your vendor aligns with them. And if they don’t align, you should be asking ‘why not’?
True security shouldn’t come at a premium
You might be wondering why some of these cloud security vendors don’t realize that moving your data around and granting themselves excess permissions is putting you at risk. Many vendors actually do recognize the vulnerabilities of their default settings — and they are taking advantage of that. Their solution has been to monetize enhanced privacy features. Instead of addressing these gaps at no additional cost, they charge users extra for the privilege of secure scanning within their own accounts. They’re nudging customers toward pricier options just to attain what should be standard security features. The GDPR says ‘Privacy by Default,’ not ‘Privacy for a Premium.’ So why are these vendors charging you extra for something that by regulation should be the default?
3. Attacks are inevitable, and breaches happen
Some security providers stand behind the claim that identifying all attack paths can allow customers to prevent 100% of attacks. But this claim is not grounded in reality, especially considering the fluid nature of development teams. Even with the most rigorous security practices, an organization can oscillate between secure and insecure states, sometimes multiple times a day — especially when changes are made using legitimate credentials and permissions.
Rather than pursuing the unattainable illusion of absolute security, Lacework uses a data-informed approach. Our method doesn’t merely identify different risk scenarios; it also identifies unusual patterns and activities, presenting a holistic perspective on potential threats and notifies you about the ones that slip through the cracks, so you can address them ASAP before they become big problems.
Lacework is private by design
Lacework agentless security is private by design and by default. Our priority is always preserving the privacy and confidentiality of our customers. We believe that the default setting for any security solution should be its most secure. Clients should not find themselves in a position where enhanced security is an upgrade or an added feature. Instead, the highest level of security should be the norm, the baseline upon which everything else is built.
Check out our blog to learn more about how to ensure your data stays private.
Suggested for you


