Containers At-Risk: A Review of 21,000 Cloud Environments
Securing your workloads in public clouds requires a different approach than that used for traditional data centers. The need to operate security at cloud speed, respond to continuous change, adapt at scale, and operate with a new operating model all require a dramatic shift in the type of container security solution required by today’s operation. In a world where APIs drive the infrastructure and create ephemeral workloads, organizations can develop control over their cloud security posture through real-time visibility, anomaly detection, and deep understanding of the behaviors of users, resources, and connections.
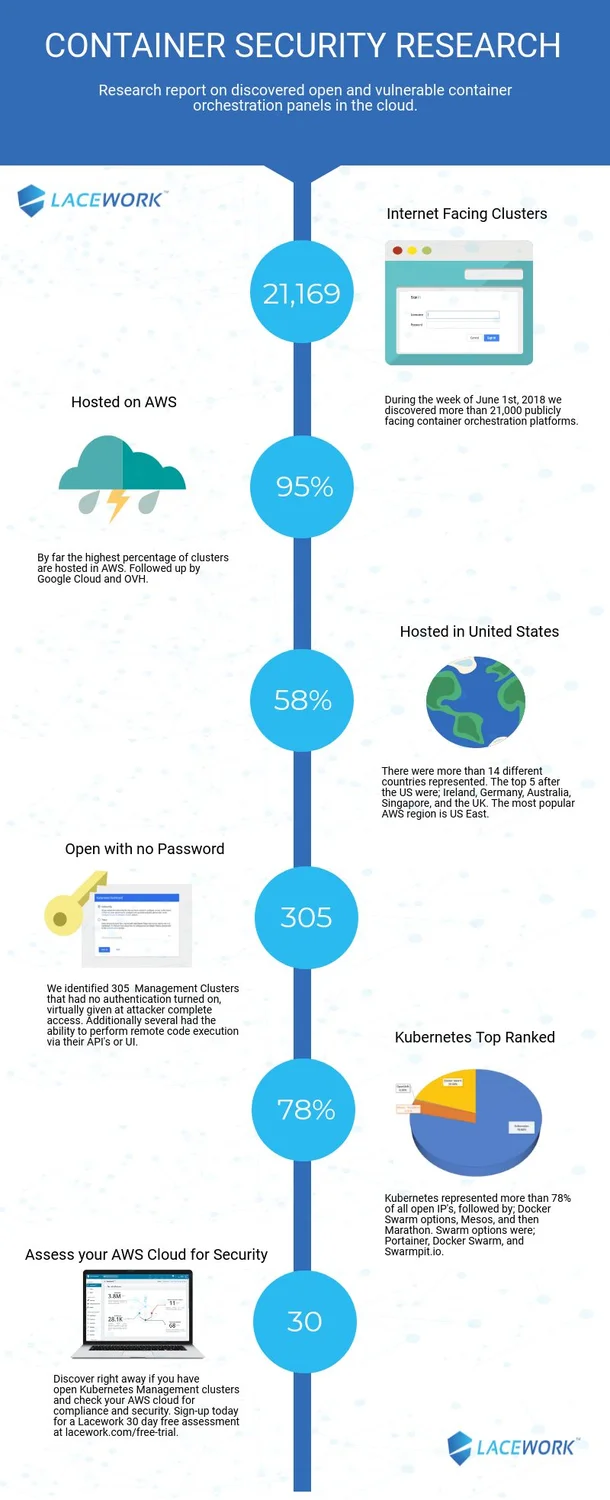
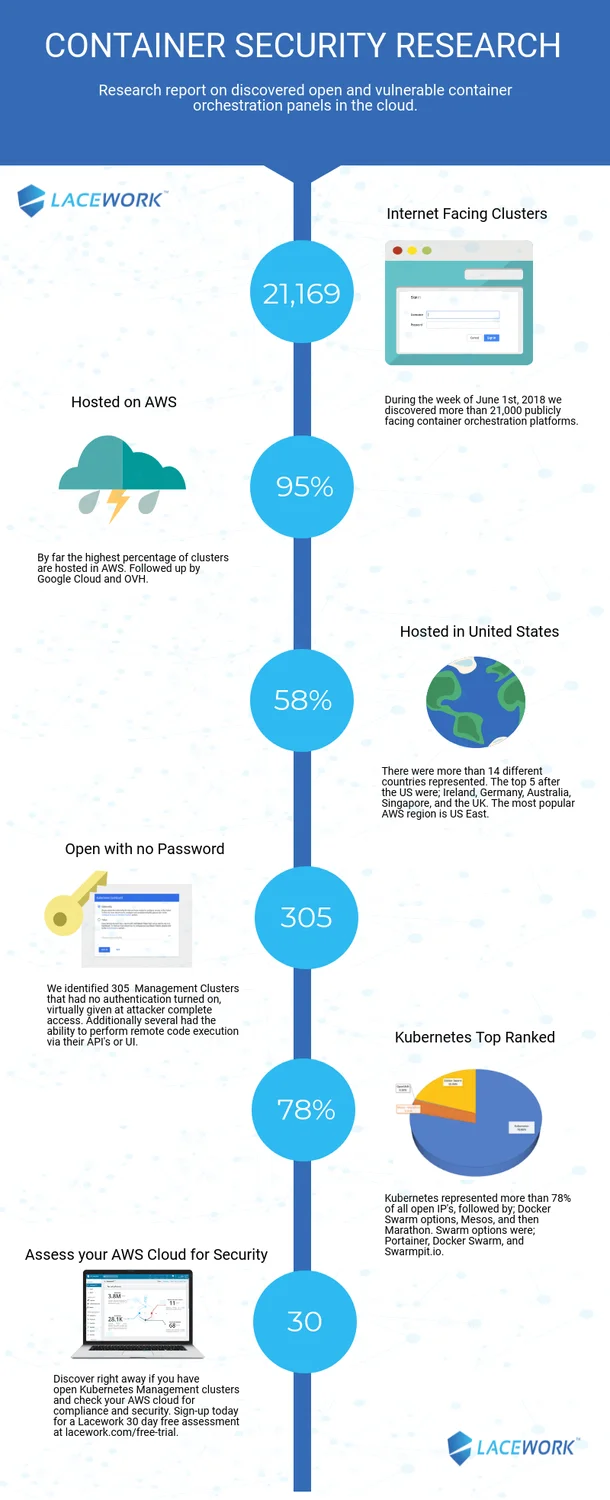
The reality of the risks of operating workloads in the cloud is highlighted in this research conducted by Lacework. In early June 2018, Lacework discovered more than 21,000 container orchestration and API management systems on the Internet, and these results highlight the potential for attack points caused by poorly configured resources, lack of credentials, and the use of non-secure protocols. Read the full report here:
The following platforms were all discovered as part of the research:
- Kubernetes
- Docker Swarm
- Mesos Marathon
- Redhat Openshift
- Portainer.IO
- Swarmpit
- Swagger
This report describes the risks and threats that can be created by deploying workloads in the public cloud without the proper security guardrails, security services, and the systematic use of security best practices.
Infographic (downloadable PDF or PNG).
Categories
Suggested for you