Container Security: A Popular Topic at BSidesSF ‘19
James Condon
Director of Research, Lacework Labs
Before the masses assembled for RSAC, BSidesSF 2019 took place at the Metreon AMC 16 in San Francisco, CA. As it turns out, a movie theater is an amazing venue for a conference like BSides. Talks were held in the City View movie theaters and even the IMAX theater, which happens to be the 3rd largest screen in the US.
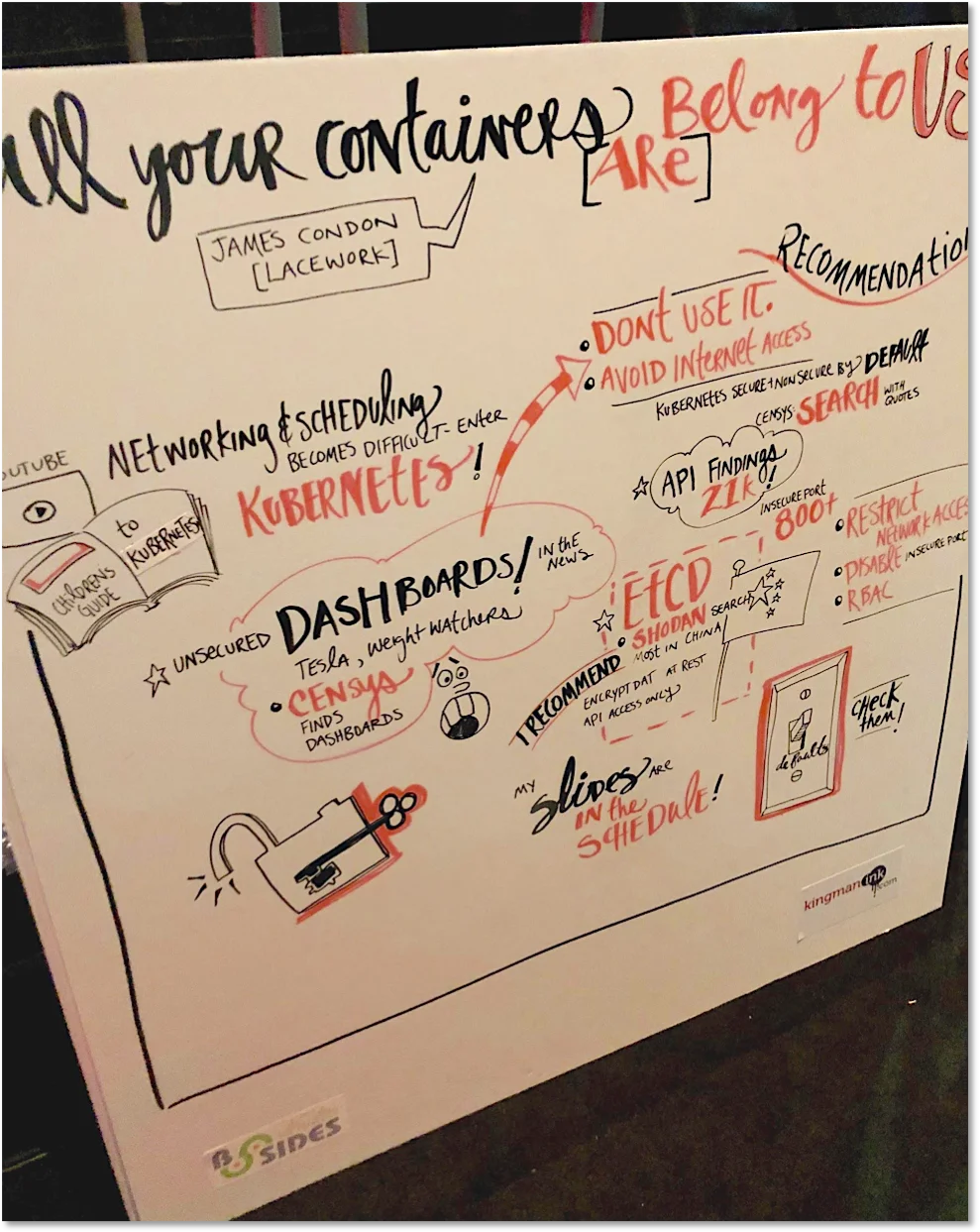
Container security was a hot topic at BSidesSF. Sarah Young of Microsoft gave an excellent talk on container security strategies called “How to Lose a Container in 10 Minutes.” In the talk “Containers: Your Ally in Improving Security,” Connor Gilbert and Connor Gorman of StackRox gave a layered security approach for defense in depth when running containers. They demonstrated how various different controls could prevent a compromise following the exploit of an application in a container. Maya Kaczorowski and Dan Lorenc described the future of patch management using containers in their talk “You might still need patches for your denim, but you no longer need them for prod.” At the end of the talk, they raced to see if it was faster to patch a container or add an actual patch to a jean jacket. Lastly, I gave the talk “All Your Containers are Belong to Us,” where I discussed techniques for discovering major Kubernetes components exposed to the internet and the results from recent research (check out the cool drawing of the talk by Kingman Ink below).
In this talk, I focused on the Kubernetes dashboard, API server, and etcd. For each component, I discussed what the component was, and risks associated with the service exposed to the internet. I then walked through methods for finding each service on the internet along with our results, and some security recommendations.
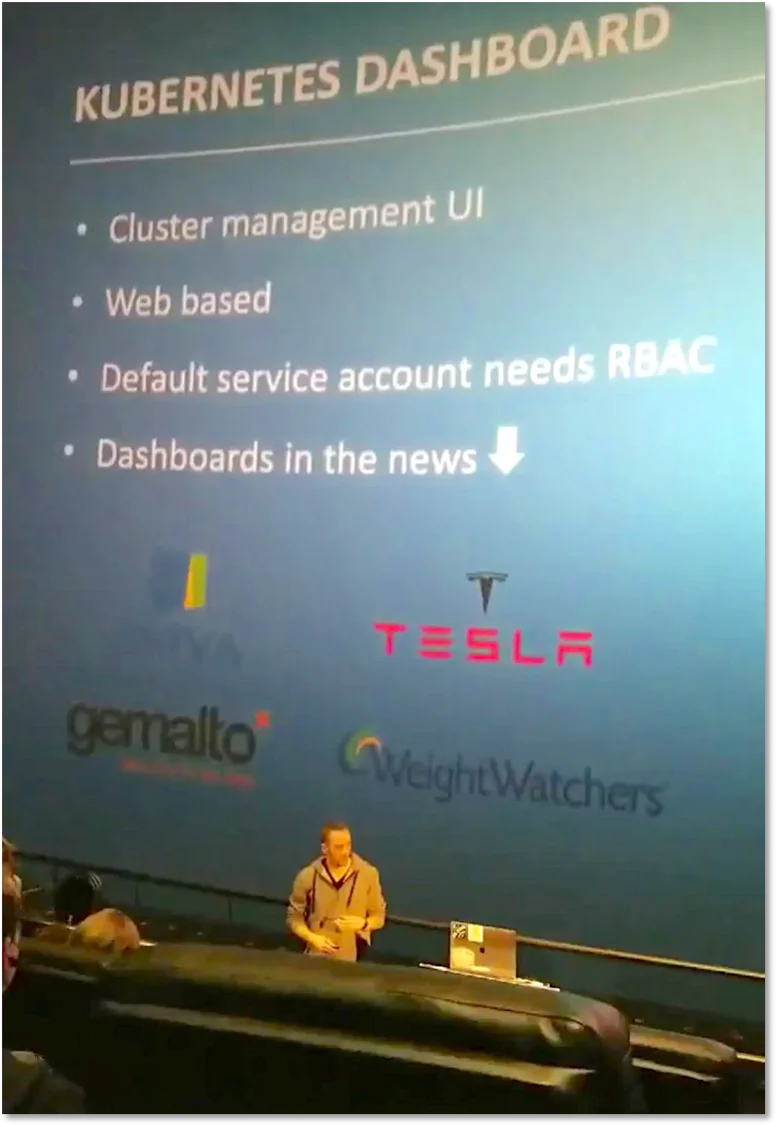
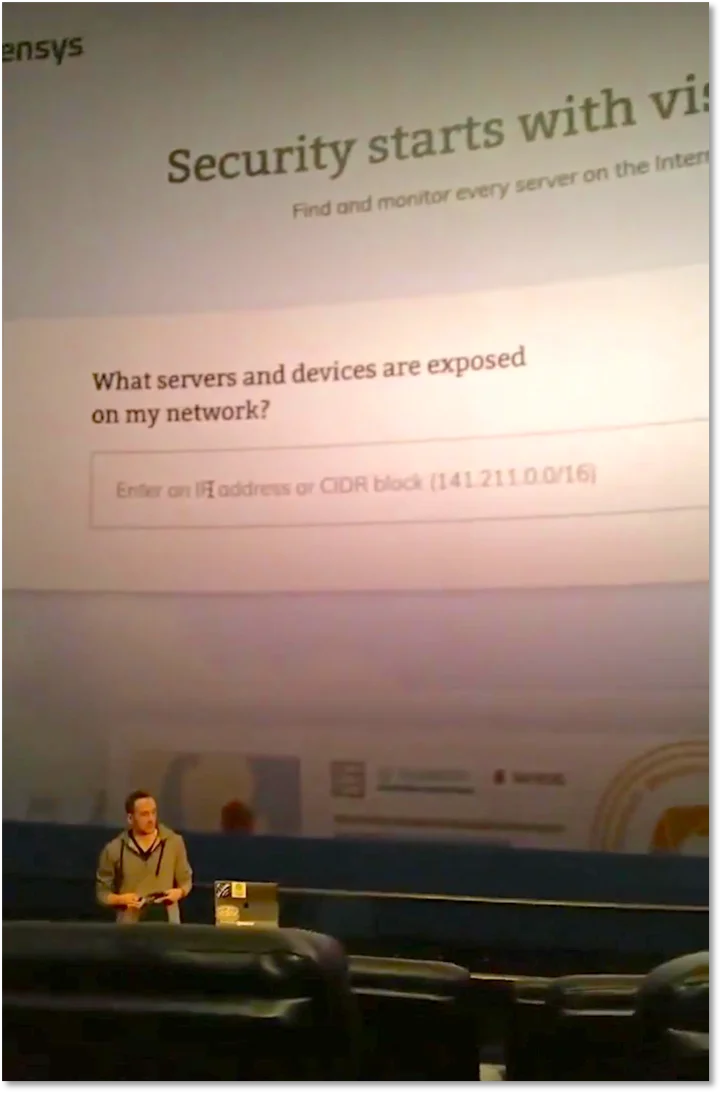
For the Kubernetes Dashboard, we used Censys to discover open dashboards. In our recent analysis, we found over 500 exposed to the internet. For the API server, we again used Censys and found over 21,000 accessible API servers and 800 insecure API servers (no authentication or authorization, more to come on the research!). We used Shodan to discover etcd clusters in the same fashion as our post a few weeks back. Here we discovered over 2,400 clusters with no authentication, many of which appear to be associated with Kubernetes clusters.
It was great being able to talk on the topics of container and Kubernetes security in San Francisco along many other leaders in the space. You can find the slides to the talk here and the video of the talk here.
If you would like to learn more about how Lacework provides workload security for containers and Kubernetes follow this link to get kick off a Free Cloud Risk & Threat Assessment and learn more.
Photo by Lorenzo Herrera on Unsplash.
Categories
Suggested for you