Understanding the latest curl vulnerabilities: CVE-2023-38545 and CVE-2023-38546
Two vulnerabilities have been disclosed for curl, a popular command line tool and library to access URLs. At the time of writing, these common vulnerabilities and exposures (CVEs) are still listed as reserved by NVD, but the curl project and some OS vendors have released detailed descriptions of the issues. These two vulnerabilities are respectively categorized as high and low severities by most vendors. However, we believe these are unlikely to see widespread exploitations in cloud workloads.
What is CVE-2023-38545?
CVE-2023-38545 is a heap buffer overflow in curl, which will impact some, but not most, users of curl and libcurl between 7.69.0 and 8.3.0.
This vulnerability affects curl/libcurl only in limited cases. This is because the vulnerability only exists when curl/libcurl is used through a SOCKS5 proxy with a specific set of configurations.
A proof-of-concept demonstrating denial of service is available on GitHub here. As with any heap buffer overflow, arbitrary code execution is a possible consequence. Users are advised to update to curl 8.4.0 out of an abundance of caution.
This vulnerability is rated as high; however, few cloud workloads will meet the preconditions above and we believe the risk of widespread exploitation is low.
What is CVE-2023-38546?
CVE-2023-38546 is another low severity vulnerability in libcurl in which an attacker who can create a file called ‘none‘ can also inject cookies into transfers made by an application that uses the curl_easy_duphandle API. The curl command line tool is not impacted.
Exploiting this vulnerability requires local access to the system with sufficient access to create specific, named files. In the presence of such an attacker, we believe the additional risk posed by this issue is negligible.
Find all your vulnerabilities in curl and libcurl
Curl and libcurl are installed on many Linux systems. There have been many vulnerabilities reported for curl — 16 were reported just this year, according to the official curl security advisories page. While these two new vulnerabilities are not critical and difficult to exploit in practice, this is a good opportunity to upgrade curl to the latest version and eliminate many known flaws.
You can easily find all your curl (and derivative curl packages) running on your hosts and containers with Lacework. Go to Vulnerabilities > Hosts, and Vulnerabilities > Containers, to see your vulnerabilities grouped by package name. Set the filter Package/Application name to include curl. Lacework displays all the curl packages (curl-minimal, libcurl, libcurl-minimal, etc.) and their list of vulnerabilities (Figure 1):
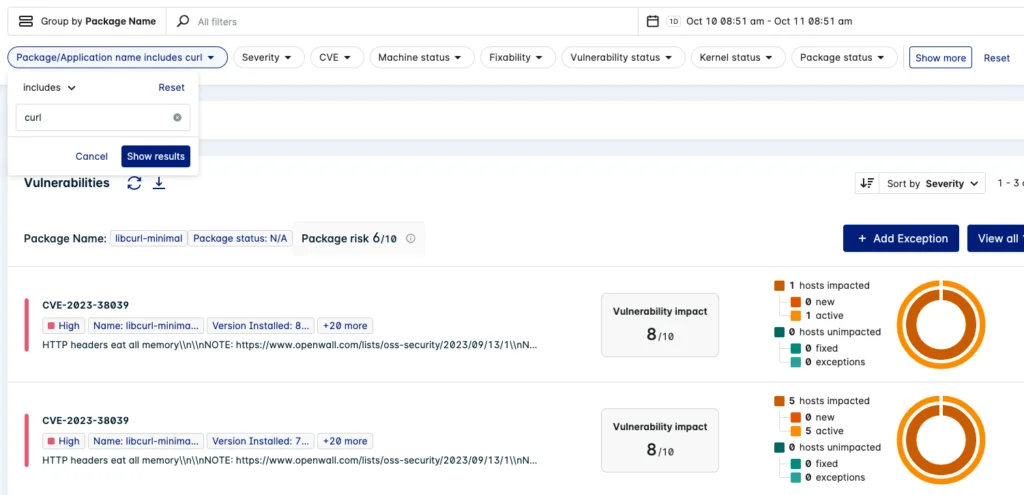
Figure 1: List of vulnerable curl packages running on hosts
The list of vulnerable curl packages might be too long to remediate all of them at once. Users can further reduce the list to focus on active packages first, with exploits available, and vulnerabilities with a fix available:
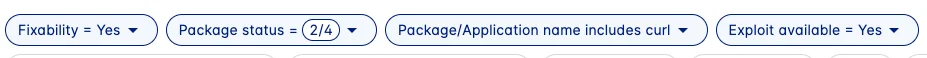
Figure 2: Prioritize active packages with known fixes and known exploits
Such well-publicized vulnerabilities, even if they’re not likely to be exploited, present good opportunities to fix many low and medium vulnerabilities simultaneously. Bring together your security and development teams to accomplish a very targeted goal to make progress in a short period.
Suggested for you


