Lacework expands workload security capabilities to protect Windows Server

Today, we are happy to announce expanded coverage of this agent-based workload protection, which includes new support for the following operating environments:
- Windows Server: New support extends runtime workload visibility and threat detection to Windows Server OS in the cloud or on-premises.
- Linux: Building on an extensive list of previously supported systems, Lacework now supports Flatcar Container Linux and Rancher OS, which are lightweight operating systems optimized for running containers.
In addition, we have expanded support for customers to continuously monitor host OS and send activity to Lacework for logging and threat detection for the following environments:
- Kubernetes: Added support for Red Hat OpenShift, Red Hat OpenShift on AWS (ROSA), Azure Kubernetes Service (AKS), Rancher Kubernetes Engine (RKE), and Linkerd. This provides coverage for both on-premises and managed Kubernetes workloads and gives visibility into Kubernetes clusters, nodes, pods, and containers.
- PaaS: In addition to existing support for AWS Elastic Container Solution (ECS) on Fargate, Lacework now supports AWS Elastic Beanstalk, which is a workload PaaS offering commonly used to manage containers and deploy applications.
Choice is critical when it comes to the cloud. Now organizations can choose to deploy their cloud applications in the environment that works best for their businesses.
The benefits (and challenges) of workload security
So what’s the benefit of an agent-based approach? As organizations build within or migrate towards the cloud, it is critical to monitor and protect all workloads. Workload security requires an agent on running systems to complement other layered defenses such as agentless cloud configuration checks or vulnerability scanning of containers prior to deployment. An agent is uniquely positioned to perform activities such as runtime threat detection of unknown and known threats, file integrity monitoring, host-based intrusion detection, and vulnerability scans.
However, many existing security agents, especially traditional on-premise endpoint detection and response (EDR) agents, come with a number of problems, including:
- Not built for the high-velocity, ephemeral nature of cloud components including hosts, containers, and pods.
- Lack of support for a wide range of cloud environments, including Kubernetes, serverless, and PaaS.
- Reliance on manual detection rules that struggle to detect unknown threats and overwhelm security teams with false positive alerts.
- Heavy weight that can slow or crash the systems they run on, especially if built for on premise.
- Create gaps by not providing build time to runtime security.
Lacework workload security capabilities
At Lacework, we have always provided workload security capabilities to protect a wide range of workloads and components, both in the cloud and on-premise. Powered by a robust, lightweight agent built for the scale, velocity, and temporal nature of cloud components, Lacework secures host operating systems, containers, Kubernetes, and PaaS environments. The agent is easy to install and maintain and includes several deployment options, along with automatic updates. For more information about our coverage, check out the details here and here.
Workload security is part of the broader Lacework data-driven cloud platform that delivers build to runtime security for hundreds of customers across the globe. The platform utilizes control plane logs for threat detection and configuration checks, vulnerability scans on containers in CI/CD pipelines and registries, compliance reporting, and Infrastructure as Code security.
The Lacework agent provides runtime monitoring and logging to track network, application, process, and user activities across hosts and containers, and includes the following capabilities:
- Threat Detection
-
-
- Signature-based detection to compare files, domains, and URLs against threat intel feed
- Anomaly-based detection to uncover known and unknown threats. Lacework Polygraph® surfaces accurate alerts with context using unsupervised machine learning.
- Host Intrusion Detection (HIDS) to identify intrusions automatically with the visibility and context to resolve events before they turn into damaging breaches
-
- File Integrity Monitoring (FIM)
-
- Monitor all critical files for changes, plus identify and receive alerts on malicious, and non-packaged-installed files
- Alert on suspicious changes to the Windows Registry
-
- Vulnerability management
- Vulnerability scans of hosts, containers, and pods
- Vulnerability management
- Compatibility
-
- Physical Machines
- Virtual Machines
- Containers
Many of these capabilities are required by compliance regulations and frameworks (SOC 2, PCI DSS, etc.) that typically require threat detection or anti-malware and file integrity monitoring that includes OS coverage.
Benefit from expanded coverage
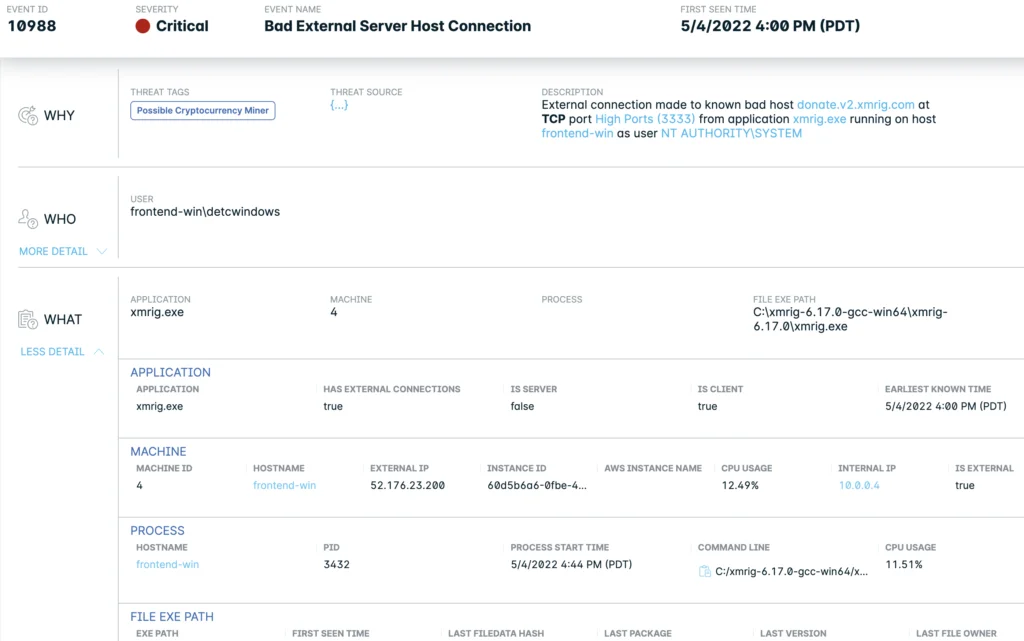
So what does this coverage expansion mean for customers? It means better visibility, better coverage, and ease of use. And now, with the Windows coverage, customers can easily see whether a malicious application on a Windows Server is connecting with a malicious external domain.
We’re committed to making protection for Windows Server workloads even easier. As seen below, now customers receive a consolidated view of important details for any critical event. This includes the who, what, why, when, where, and how. We’re eliminating the guesswork and helping customers drive faster remediation.
But don’t take our word for it. With more than 40 happy customers in Beta, the rave reviews keep pouring in. We’re excited to be able to provide our customers with choice and the flexibility they need to help them grow their businesses. A director of DevOps & IT at a US-based HR software service explains, “With the agent for Windows, we can now meet our need of 100% coverage of all hosts in the cloud, including those running Windows Server. Unlike some other cloud security vendors, Lacework ensures all our hosts are protected with threat detection, file integrity monitoring and intrusion detection, all of which we need to be secure and compliant.”
A commitment to innovation
With our expanded agent-based workload security, Lacework provides choice and flexibility for organizations to deploy their cloud applications in the environment that works the best for their business. Lacework combines an agentless and agent-based approach for a multi-layered security strategy that reduces security risks in the cloud. Lacework is committed to closing visibility gaps, enabling robust and accurate threat detection, and ensuring security and compliance, all from a single platform.
Interested in hearing more about a multi-layered security strategy? Register for our webinar with IDC to see how layered protection can help you secure tomorrow, starting today.
Also, learn more about how a combination of agent-based and agentless solutions is the most effective way to secure your cloud.
Categories
Suggested for you