Cloud Access: The Latest Offering for Initial Access Brokers
Cloud Security Researcher – Lacework Labs
Summary
Initial Access Brokers (IAB) have become commonplace across cybercrime marketplaces in recent years. A practice that has evolved from the opportunistic compromise of one-off internet-facing assets for resale as mere proxies, to now including the targeting of corporate networks, assessing the environment for business value, and ultimately selling access into the organization for usage by ransomware gangs, espionage, and everything else in between. Amazon AWS, Google Cloud, and Azure administrative accounts have quickly become the new hotness in underground marketplaces.
Initial Access Brokers
These actors play a pivotal role in the overarching cybercrime ecosystem. By scoping and compromising organizations, they provide a valuable service to other criminals who may not necessarily have the skills required for initial exploitation. Their target buyer likely has access to Ransomware-as-a-Service (RaaS), cryptominers, or other malware and is simply looking for somewhere to deploy. This combination continues to have a critical impact on organizations and individuals alike worldwide, contributing significantly to the explosion of Ransomware and Crypto Jacking that we have seen through generally lowering the bar to entry. While most prolific Ransomware gangs run their own operations end-to-end, there are many smaller and more niche players that now have access to a world of possibilities that did not exist in years prior.
While nation-state adversaries feature prominently on the nightly news, cybercrime groups are often underestimated in their sophistication. This scene is filled with competent and well-connected individuals that often have the advantage of general anonymity. Due to the nature of modern crimeware marketplaces, many can work entirely alone to maximize profits from the companies they victimize. Some may even be insiders of the distressed company themselves. This layer of anonymity plays a critical role in muddying the waters around attack attribution. The individuals initially compromising the organization are often not the same as those deploying ransomware or otherwise following through with the later stages of the attack.
A compromise of any network is no small undertaking, so creativity is crucial in amplifying their return on investment. When you take a step back, many compromises are not simply a single group with a shared goal. The reality is more akin to an intertwined community, with many diverse hands involved along the way, leading to the industrialization of cybercrime we are witnessing today.
According to a report released by Cybercrime Magazine, they estimate that “global cybercrime costs [will] grow by 15 percent per year over the next five years, reaching $10.5 trillion annually by 2025.” An incredibly staggering yet entirely realistic projection.
Ascent of Initial Access Brokers into the Cloud
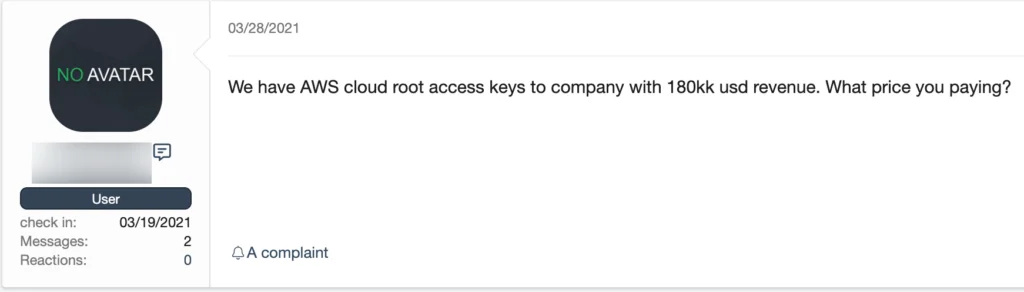
While a majority of attacks involving cloud assets have centered around the exploitation of ephemeral services by cryptocurrency mining botnets, in reality, this is merely scratching the surface. As corporate infrastructure continues to expand to the cloud, so do opportunistic adversaries, adapting their techniques, tactics, and procedures to capitalize on the resale of access to cloud management accounts and related infrastructure.
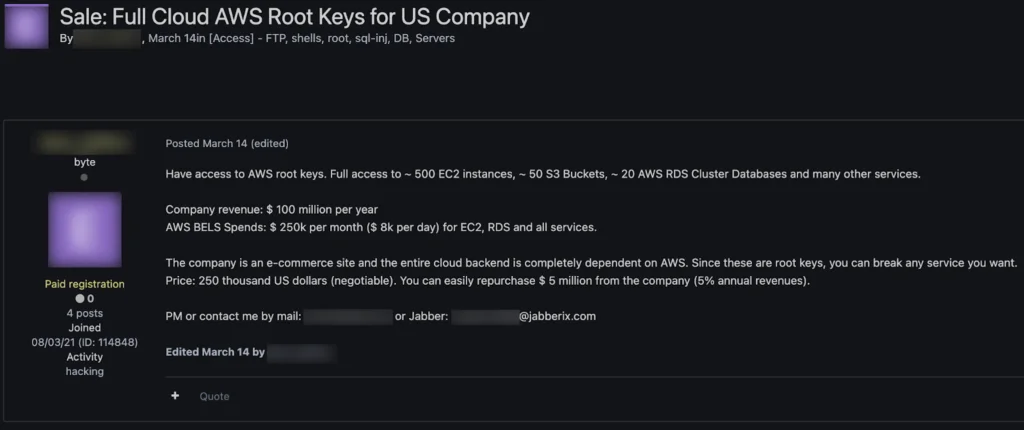
Cloud access resale has primarily centered around free trial accounts with initial credits from prepaid credit card registrations and fake information until recently. Cybercriminals have realized the actual utility in access to corporate cloud infrastructure. Many of the more popular listings indicate SMTP port 25 availability and message relay credits for relaying spam and phishing attacks. The abuse can be very costly and damaging to the organization’s reputation, resulting in a lasting negative impact on their business. However, prime targets are still AWS root keys.
According to a recent paper published by the Cloud Native Computing Foundation, “Identity and Access Management (IAM) is the biggest attack vector, regardless of platform or vendor, and it is critical to carefully manage IAM policies to provide both developers and agents secure access to source code. Pipeline agents and human developers must have their access and privileges calibrated to their roles within the organization and be given secure means to authenticate to those roles.”
Root access into the cloud infrastructure of technology companies with wide-reaching access into other organizations, such as Managed Service Providers, are ideal targets for cybercriminals. Any one organization could provide credentials, sensitive information, and much more from a single compromise than going after one-off organizations directly. Cloud makes this much more accessible and centralizes operations to even automate for quick and easy wide-reaching impact.
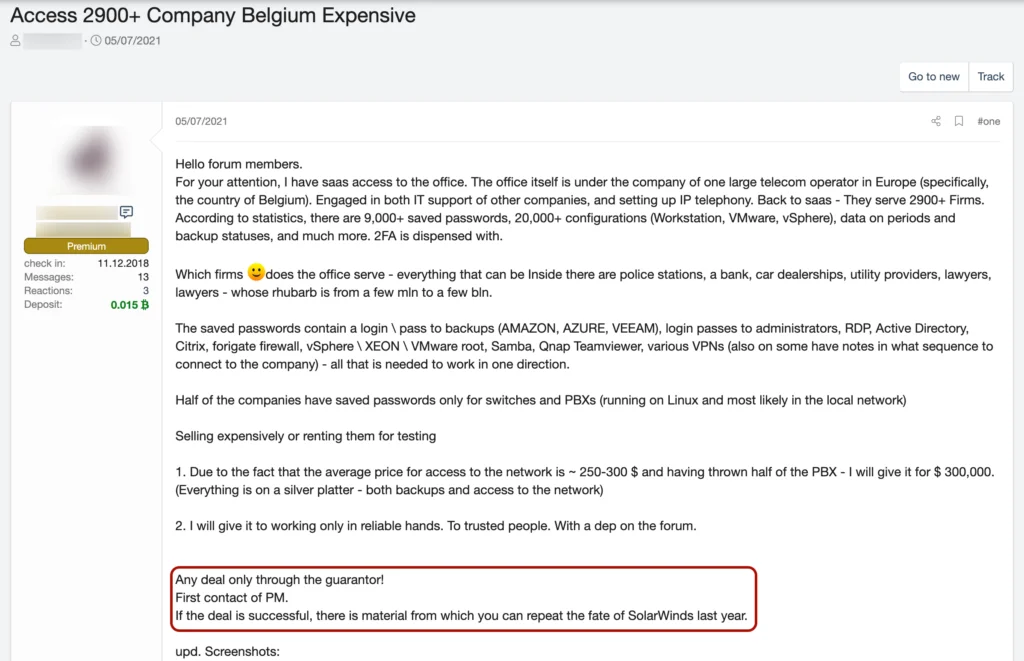
While initial access brokers still primarily target organizations opportunistically through exposed Remote Desktop Protocol (RDP), phishing, and related attacks against core infrastructure and employees, the resale of cloud root keys, access to Kubernetes management nodes, and cloud services, in general, is growing exponentially. What started as one-off marketplace postings continues to escalate as criminals began to understand and operationalize the utility of access to these services above and beyond cryptocurrency mining.
Impact
Cryptojacking (T1496) alone can be extremely costly to businesses. When considering the possibility of an attacker gaining administrative access over the cloud infrastructure, the paradigm shifts dramatically. Attackers could access sensitive data; disrupt, degrade, and destroy entire environments; and even attacks as seemingly innocuous as cryptomining become incredibly impactful once the keys to the kingdom are unleashed. Spinning up new resources and mining at scale can be astonishingly costly, with an immediate impact on the organization’s finances as a whole if guardrails are not in place.
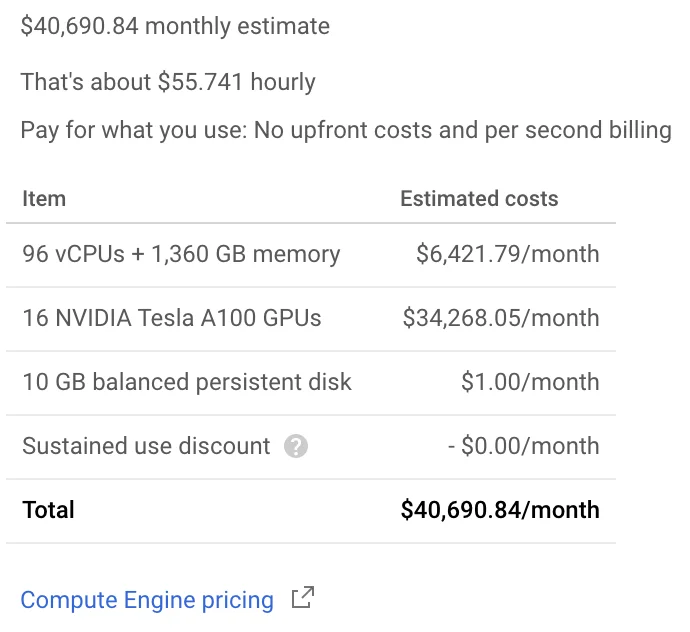
It doesn’t stop at access to resources either. Often the logs and other sensitive information that may be accessible in the environment can be a treasure trove of profitable data. There are even entire marketplaces dedicated to the resale of logs from web servers, and cloud service logs can provide even more valuable information to adversaries. Allowing them to extract credentials, session tokens, and related data that they can then use to expand their operations.
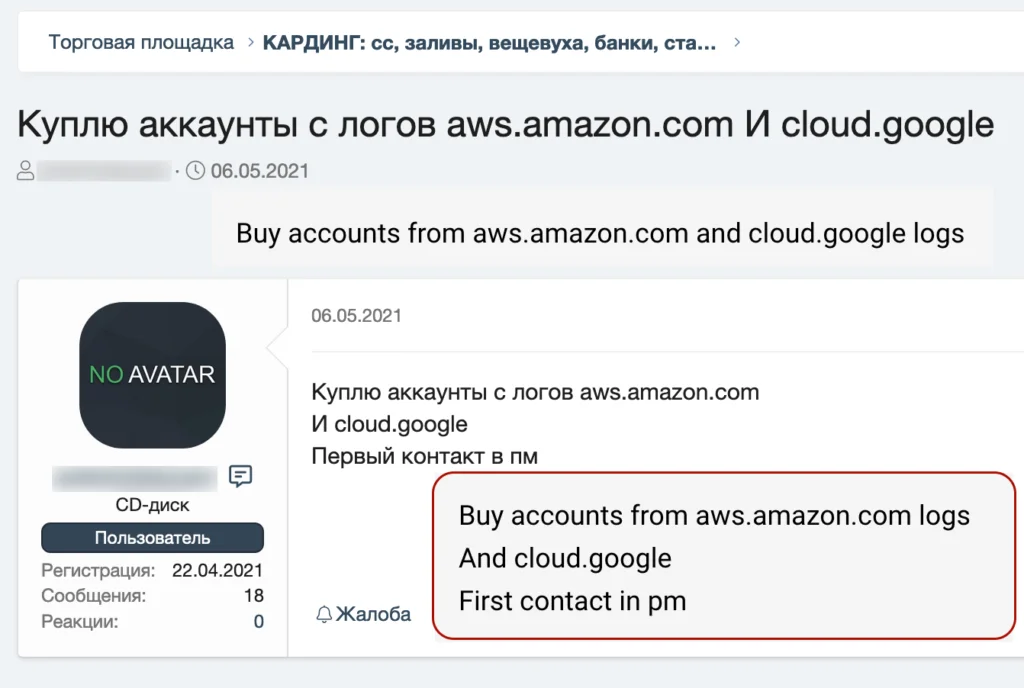
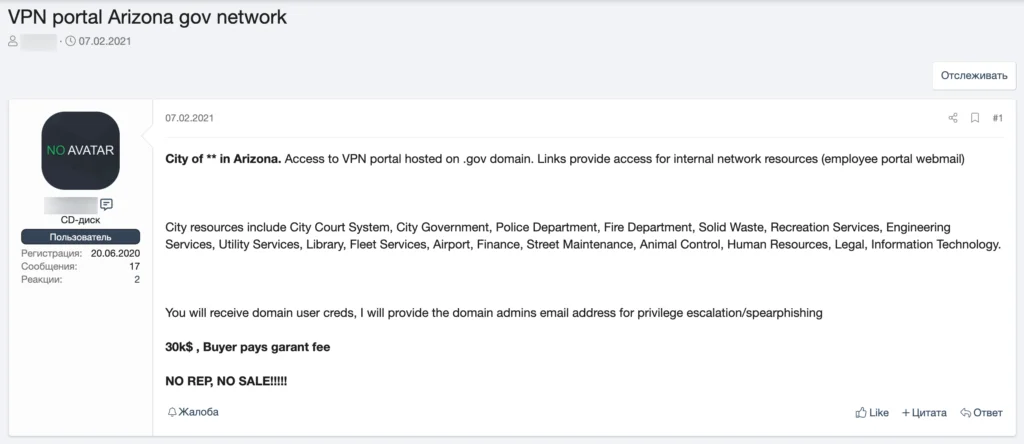
Regardless of the end goal, marketplace listings for AWS, GCP, and Azure root credentials are flying off the shelves.
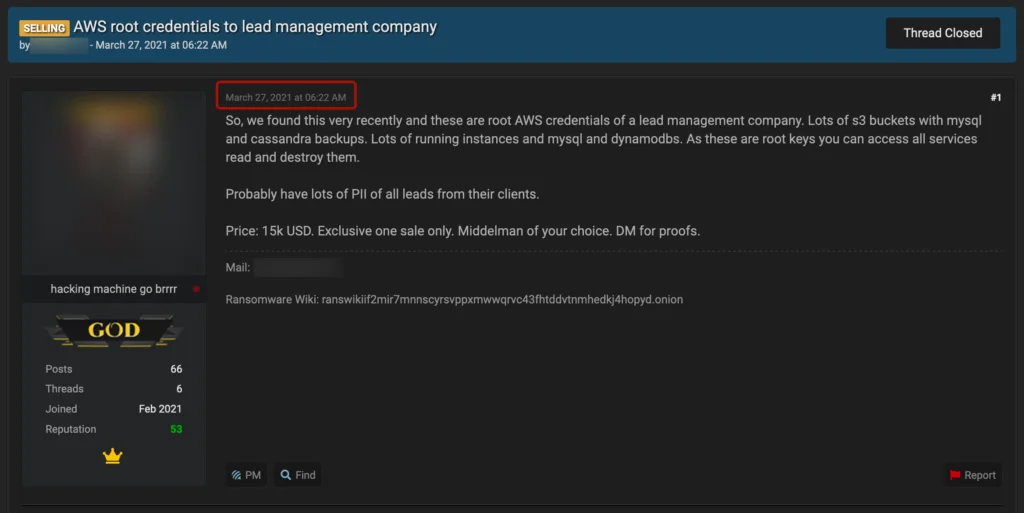
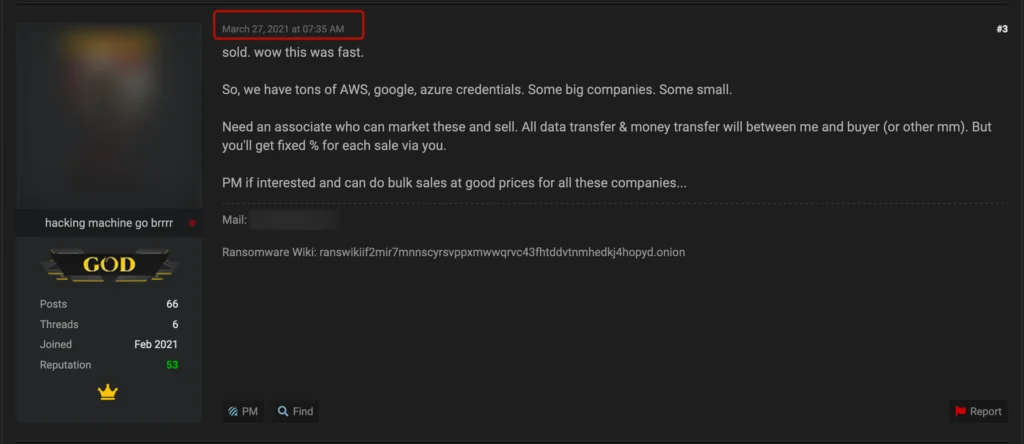
With many high-dollar sales completing in only a matter of hours.
Mitigation
To combat the acceleration of Cloud Access Brokers, organizations must think holistically about the protections in place to secure, monitor, and protect our cloud infrastructure.
- Train staff to ensure security is a core tenant of your organization and reinforce through phishing simulation and continuous end-user testing + verification.
- Ensure multi-factor authentication is in place for all external-facing assets.
- Rotate master keys regularly – every 45-days is recommended and can be automated.
- Implement instance, billing, and utilization threshold limits with alerting + prevention.
- Monitoring for internet-exposed vulnerabilities and patching quickly and efficiently.
- Following compliance standards and ongoing tracking + notification of changes.
- Alert on never-before-seen IP addresses accessing the infrastructure.
- Look for changes in permissions, particularly new grants added to master keys.
- Implement Cloud Workload Protection and baseline routine activities + alert on deviations.
Please follow @LaceworkLabs on Twitter and LinkedIn to keep up with our latest research.
Categories
Suggested for you


