Workload security
starts and ends with
threat detection
Go beyond the basics. Our advanced detection capabilities identify even the most elusive threats in real-time to stop bad actors in their tracks.

Uncover hidden threats
Discover never-before-seen attacks with patented behavioral anomaly detection and context-rich Composite Alerts

Stop threats up to 100x faster
Automatically aggregate and analyze evidence and context of emerging threats with machine learning, delivering a consolidated, actionable alert

Most effective agent in cloud security
See and protect every workload with a modular, adaptive agent to gather the security telemetry you need to focus on your true threats and vulnerabilities

Protect all workloads
Zero snapshots—protect your cloud infrastructure with a security platform that is private by design and keeps your data where it is
Complete protection for your workloads
No other platform comes close to breadth and depth of ML-driven training to detect anomalous behavior across containers, hosts, Kubernetes, and other workloads at runtime
Detect suspicious activities early
- Uncover incidents from a weak signal anywhere across your clouds
- Continuously append and automatically provide rich, contextual details to the detection
- Intelligently collect evidence from multiple signals to form a single, consolidated alert of a bad actor
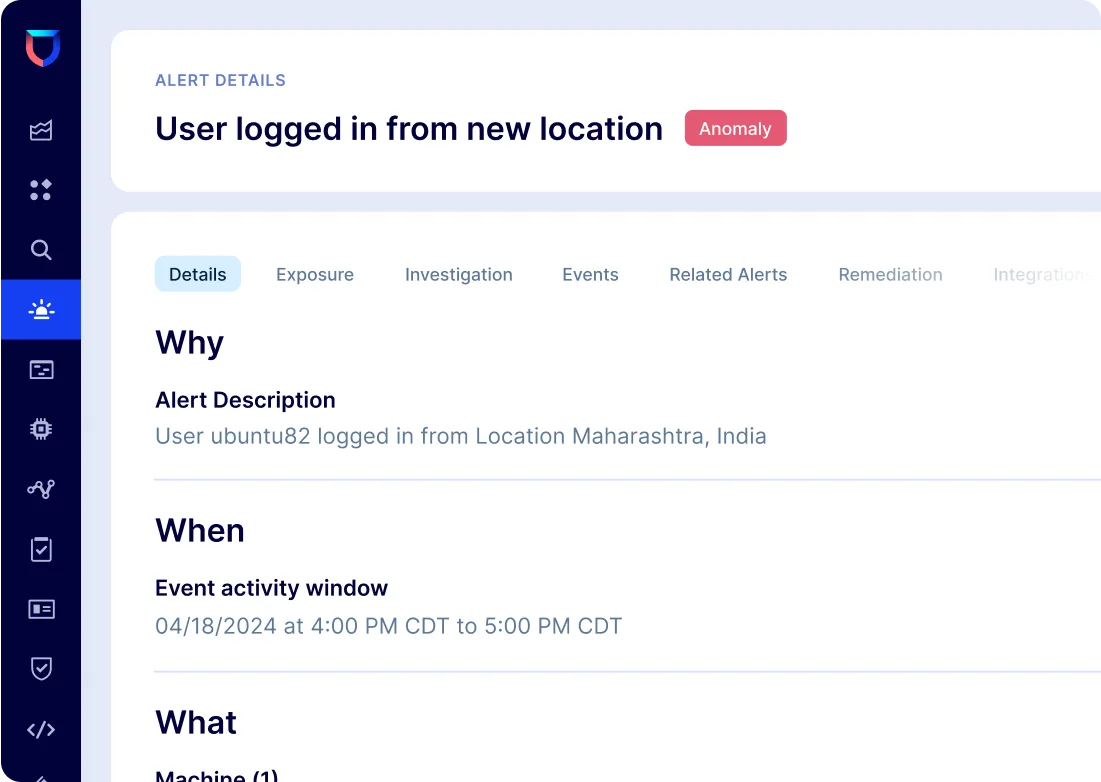
Exponentially accelerate investigations
- Cut down attacker dwell time and minimize business impact
- Eliminate alert noise by up to 1000x with Lacework Composite Alerts
- Correlate known attack patterns with anomaly detections while continuously adapting against new attack tactics
Predict how attackers may infiltrate your organization
- See the attack paths across your multicloud environment and proactively mitigate these weak points across your organization
- Increase visibility with a single, unified platform to assess vulnerabilities and enforce security policies to protect your cloud workloads
- Implement security recommendations to prevent costly issues such as fines and lost revenue
“We avoided hiring four full-time employees, eliminated spend on the human resource side, and freed up resources that we already had.”
John Turner | Senior Security Architect
Read the story
“Lacework is set up with a regulatory environment in mind and it’s a very data-driven solution. We’re able to actually show our customers our responses to events in the environment in real time. It’s a tremendously important part of our data security toolkit.”
David Odmark | Chief of Security
Read the storyLearn more about CWPP
Featured Insights
FAQs
As a best practice, a CWPP should be deployed early on in cloud adoption journeys to embed security. Taking full advantage of automation and advanced analytics maximizes the value gained.
Both agent-based and agentless CWPP deployments are essential as they enhance proactive security, threat detection, and address risks in code and at runtime.
A CWPP is part of a larger cloud-native application protection platform (CNAPP). CNAPP offerings bring together multiple disparate security and protection capabilities into a single platform.

