Who’s Attacking My Containers?
Chris Hall
Cloud Security Researcher, Lacework Labs
If you’re concerned about the security of your cloud resources then you may have asked yourself: “Who’s attacking my containers?” This blog will attempt to answer that question. As described in the kill chain model, the first phase of any attack is reconnaissance. This entails some form of information gathering about the target and usually involves service port and or vulnerability scanning.
For cloud resources, this would include scanning for Docker and/or Kubernetes. Enter GreyNoise. In our last blog we described how we used GreyNoise to provide context on cloud servers from the H2miner botnet.
For this blog, we leveraged GreyNoise to identify suspicious hosts that were specifically scanning for containers.
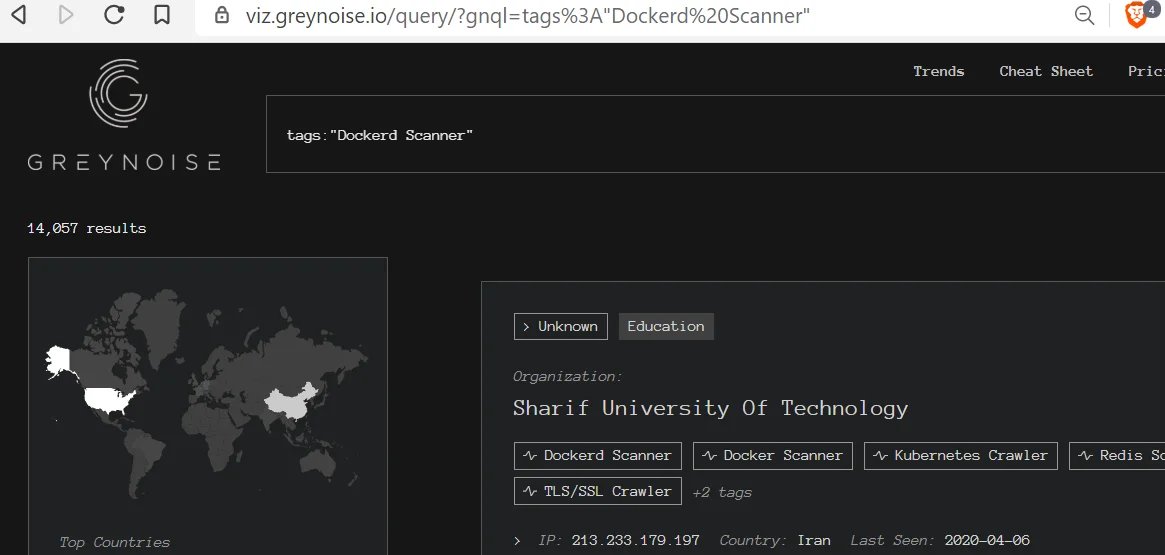
Figure 1. GreyNoise tag searches
The first step was to identify the appropriate tags which included:
- Docker Scanner
- Dockerd Scanner
- Kubernetes Crawler
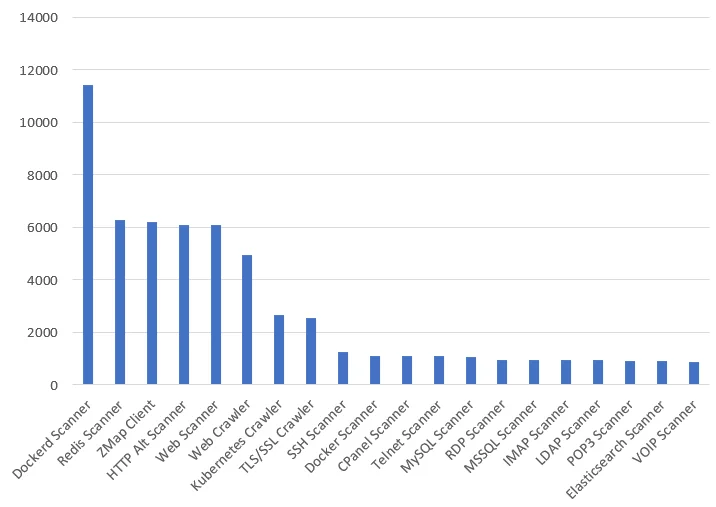
These inputs returned over 14K hosts from GreyNoise. Ranking of all the tags from the outputs allowed for additional insight. For example, the scanning application of choice was revealed with the tag “ZMap client.” ZMap is an open-source security scanner that was developed as an Nmap alternative. Several tags relating to web scanning were also observed such as “Web Scanning,” “HTTP Alt Scanner,” and Web Crawler,” and may have been a precursor to web app exploitation attempts.
Figure 2. GreyNoise tag rankings
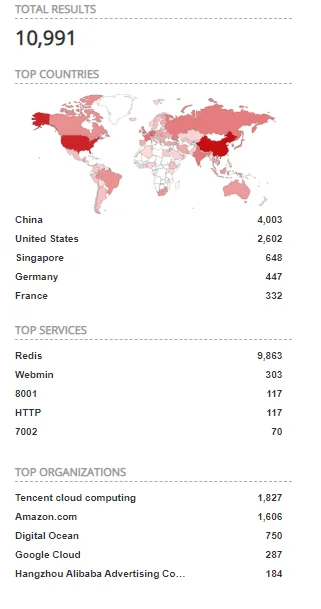
The 2nd most common tag was for Redis Scanner indicating a probable exploitation vector. Redis was similarly seen in our last blog as the vector used in the H2miner botnet propagation. This is probably due to its popularity as well as many associated vulnerabilities. Furthermore, no-auth Redis instances are easily discovered as illustrated with the following Shodan query which returned around 11K hosts:
product:”Redis key-value store”
Figure 3. No-auth Redis instances in Shodan
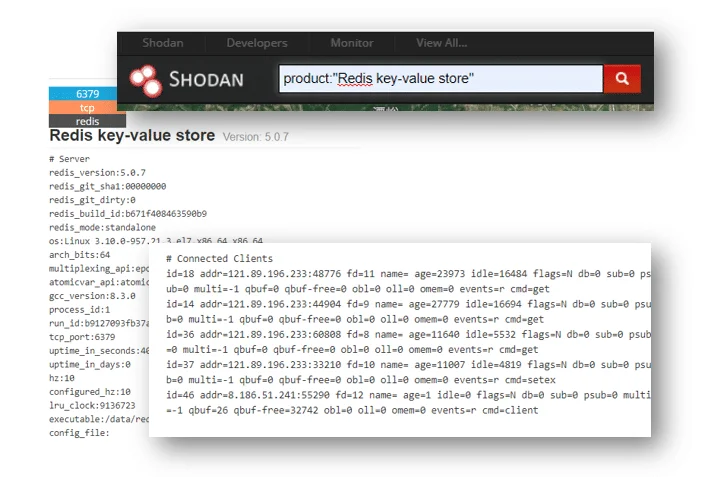
Shodan also lists connected clients in their key-value store. Using the API, we extracted all these IPs from the cloud scanning hosts with no-auth Redis instances.
Figure 4. No-auth Redis Search details
The following table shows the top IPs for the Redis connected clients. Interestingly, some of the hosts are from legitimate scanners, however, they’re observed connecting to multiple instances.
|
IP |
# of Redis connected instances |
ASN |
Country |
|
193.106.31.98 |
147 |
AS50297 Infium, UAB |
Ukraine |
|
198.108.67.48 |
131 |
AS237 Merit Network (censys.io) |
United States |
|
23.225.183.234 |
120 |
AS40065 CloudRadium L.L.C |
United States |
|
92.118.37.64 |
114 |
AS204655 Donner Oleg Alexeevic |
Russia |
|
169.197.108.34 |
94 |
AS21859 ZENLA-1 (internet-census.org) |
United States |
|
78.128.113.46 |
93 |
AS209160 Miti 2000 EOOD |
Seychelles |
|
128.14.136.18 |
92 |
AS21859 ZENLA-1 (internet-census.org) |
United States |
|
202.107.207.229 |
77 |
AS4134 CHINANET Zhejiang province network |
China |
|
202.107.226.3 |
75 |
AS4134 CHINANET Zhejiang province network |
China |
|
193.106.31.162 |
75 |
AS50297 Infium, UAB |
Ukraine |
|
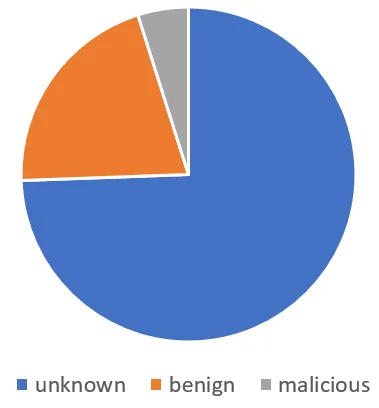
It’s important to note that just because a host is scanning your environment, it’s not necessarily malicious. For example, legitimate internet scanning services such as Shodan and Censys are frequently observed. While these could be used for malicious reconnaissance, failing to identify will result in false positives. GreyNoise classifies benign IPs as such and will provide an actor name if known. For the cloud scanning IPs, approximately 20% were from known benign sources. |
|
Figure 5. Host Classifications |
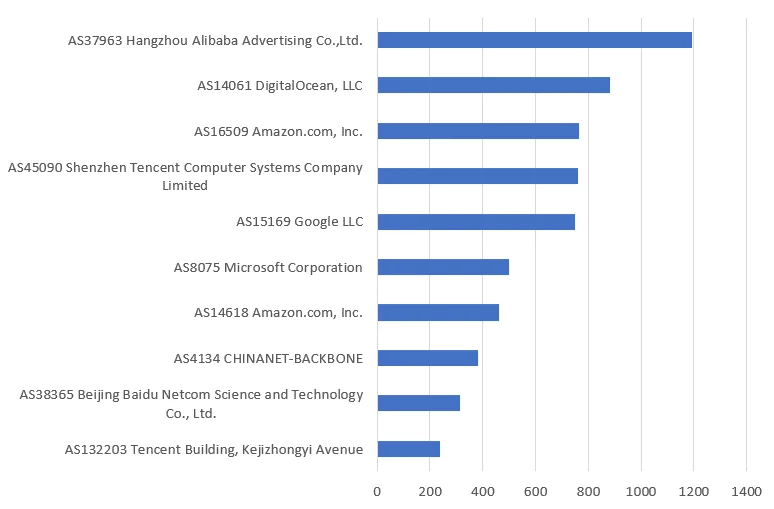
After filtering benign hosts, we’re left with 11,459 out 14,448. Sorting by ASN and organization gives us the chart in Figure 6. The top ASN is for Alibaba/Aliyun computing which appears to be a common source for a lot of scanning activity. Furthermore, the ASN breakdown is also consistent with the Shodan hits and the no-auth Redis instances in general.
Figure 6. ASNs Cloud scanning hosts
To summarize, Redis appears to be the low hanging fruit that many are taking advantage of. And since many cloud servers use Redis, these are being exploited and subsequently leveraged for additional scanning. This was the likely same tactic used in the H2miner botnet’s self-propagation detailed in our last blog. It’s safe to say that any Redis misconfiguration will likely be exploited in short order. For an example of a Redis exploit in the wild, refer to our “Anatomy of a Redis Exploit” blog from 2018.
Past activity indicates financial motivation with the deployment of cryptomining malware, however, any sensitive data in your Redis database will likely be stolen and distributed if accessed by a bad actor. Fortunately, many cloud security products such as the Lacework agent can reduce your exposure with active monitoring.
If you found this blog useful then please share on your social media!
Photo via GreyNoise Intelligence
Categories
Suggested for you