SolarWinds & the Software Supply Chain
Chris Hall
Cloud Security Researcher, Lacework Labs
The software supply chain is often overlooked when it comes to security. Perhaps the latest SolarWinds incident will give it the attention it deserves. By trojanizing a software update delivered from SolarWinds, unknown actors were successful at achieving malware installation at numerous organizations and across multiple verticals.
Supply chain has long been an attractive target for both state-sponsored actors and cyber criminals alike. There are several reasons for this:
- Supply chains by their very nature are vulnerable due to their complexity and multiple points of entry
- A given supply chain is built on numerous trust relationships, each having their own vulnerabilities
- A successful compromise enables a “one-to-many” opportunity which is highly advantageous
In supply chain exploitation, “one-to-many” opportunities can be enabled in multiple ways: targeting of transportation and logistics entities, platforms such as those used for IT, ERP and procurement, targeting of raw material manufacturers, and of course through software. With regards to software, the more popular the better. As such, SolarWinds is the ultimate case study with roughly 300K customers across public and private sectors and across multiple industries.
The specific tactic used involved the modification of a software package and deployment via the vendor’s infrastructure. Many organizations do not scan files from trusted sources and even so, the trojanized software only had 1 AV detection as of December 14th. The result is a recipe for mass exploitation.
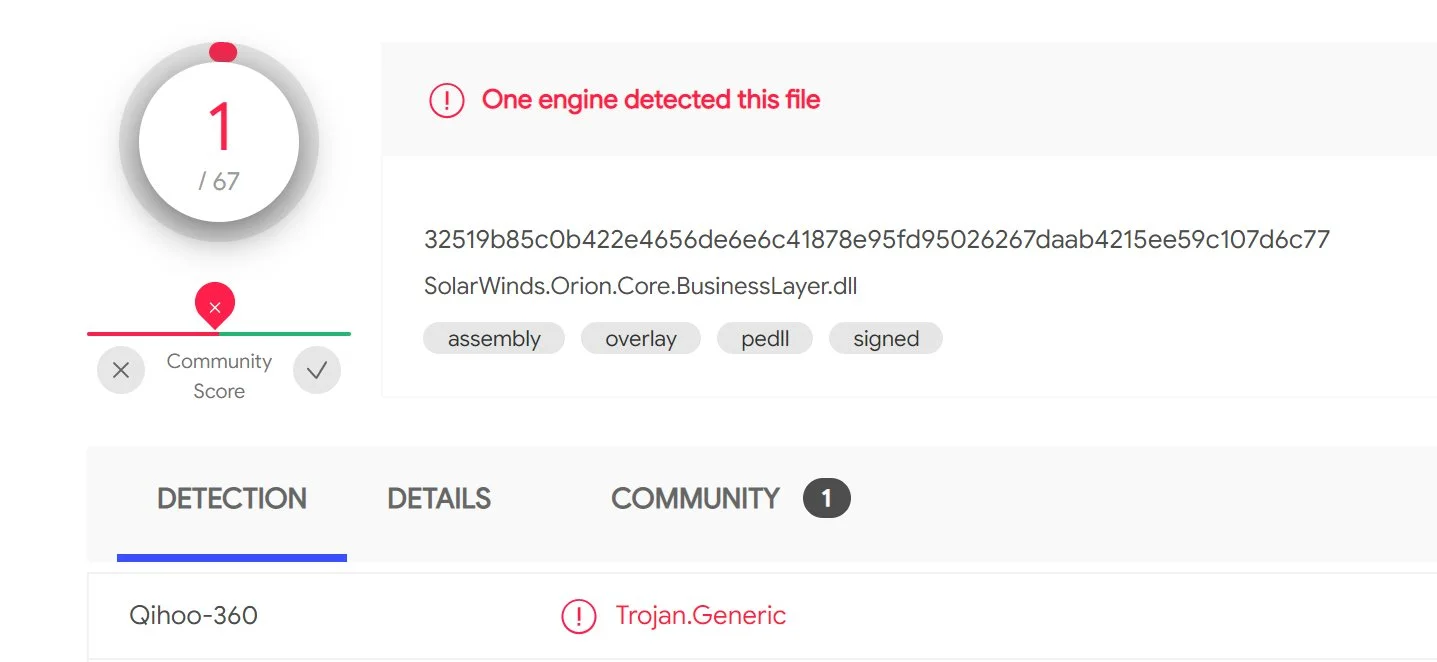 |
Figure 1: AV detection – 14 December
This is not unprecedented. In 2013 and 2014, a Russian actor (Energetic Bear) similarly trojanized software downloads from eWON, MB Connect Line and Mesa Imaging. These companies provide services in the pharmaceutical industry. In one instance, Energetic Bear trojanized a driver used in optical imaging software, suggesting engineers were among the intended targets. Note: FireEye has not categorized the SolarWinds adversary however others have pointed towards Russia attribution.
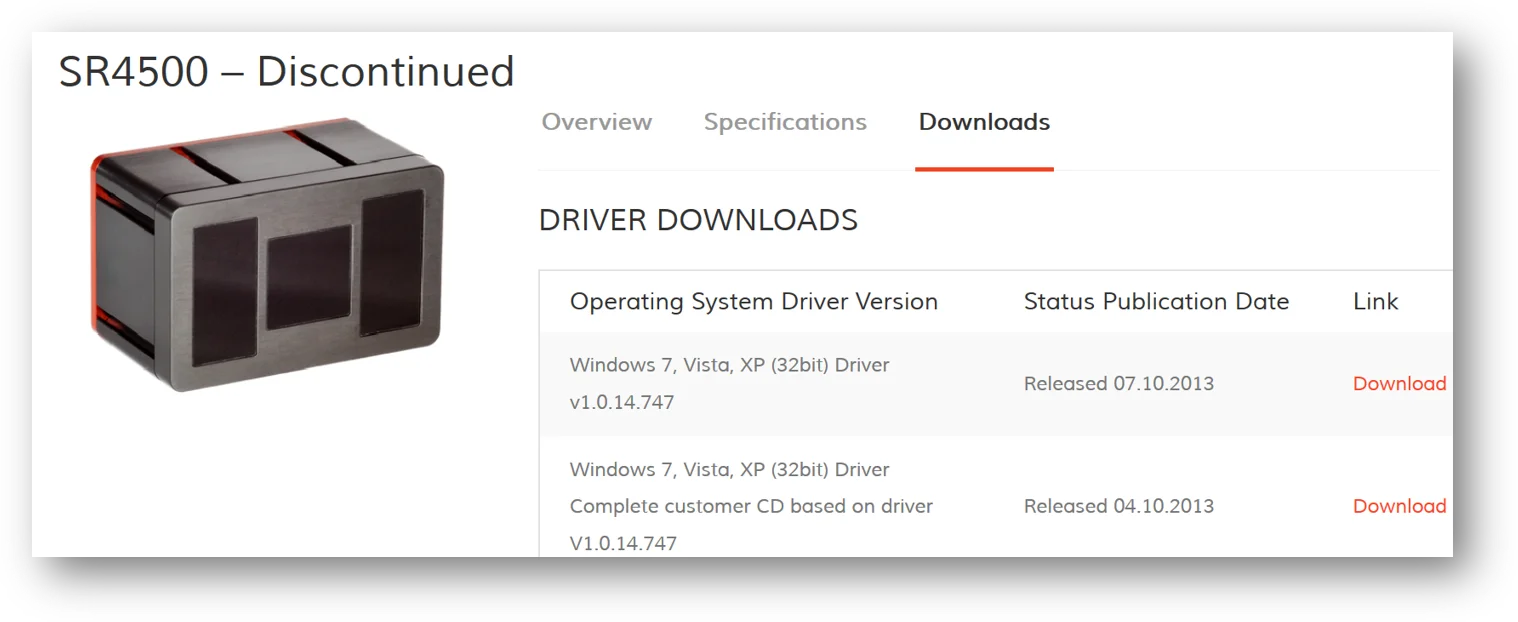 |
Figure 2: Driver trojanized by Energetic Bear
The malware leveraged in SolarWinds compromise was characterized by a unique DGA (Domain Generation Algorithm) that offered insight into targeted entities. The functionality leverages either a substitution cipher or custom base64 to encode names for targets. Examples of domains names and their referenced organization:
|
|
Decoded target |
|
0ms9s6cmpd7s3mhcun0c2dioho7r1p0g.appsync-api.us-east-2.avsvmcloud.com |
ad.optimizely |
|
0olcrtj4bsjtulfburso2ve2sd0ee2h.appsync-api.us-west-2.avsvmcloud.com |
aerioncorp.com |
|
060mpkprgdk087ebcr1jov0te2h.appsync-api.us-east-1.avsvmcloud.com |
belkin.com |
It is currently unclear if actors conducted follow-on exploitation at the organizations derived from the DGA domains. At the very least we can confidently say that they were specifically marked for targeting. One finding from these targets is that there does not appear to be any single trend with regards to the type of organization. This extensive scope would indicate widespread espionage intended to serve multiple intelligence requirements including those involving government, financial institutions, tech, mining, and manufacturing.
Malware infection via software updates is particularly insidious as it occurs through trusted channels and can completely bypass protections. For example, it doesn’t matter if an application is externally facing or not when the vendor is leveraged as the vector. This was evident with SolarWinds Orion Platform of which there are few externally facing instances relative to the number of customers.
If the software supply chain for a trusted provider has been compromised, then it can be extremely difficult to prevent malware installation.. This explains why organizations with mature security postures can fall victim to such attacks. This also pushes defense to the right of the kill chain where identification of post-exploitation activities and anomaly detection capabilities are essential.
If you’ve been affected by this attack, then please reference DHS’s emergency directive for a list of mitigations.
Categories
Suggested for you


