Securing the dream: A security makeover for the Dreamhouse
Our story begins in Malibu at the iconic Dreamhouse of the one and only Barbie. Little did Barbie know, her picture-perfect world, filled with hyper-pink hues and impeccable fashion, was about to be shaken.
When Barbie’s® best friend, CISO Barbie, pulled into the Dreamhouse driveway in her hot pink convertible for a weekend visit, she was immediately horrified.
CISO Barbie, stepping out of her car, took one look at Barbie’s house and gasped, “Barbie, this is a security nightmare!”
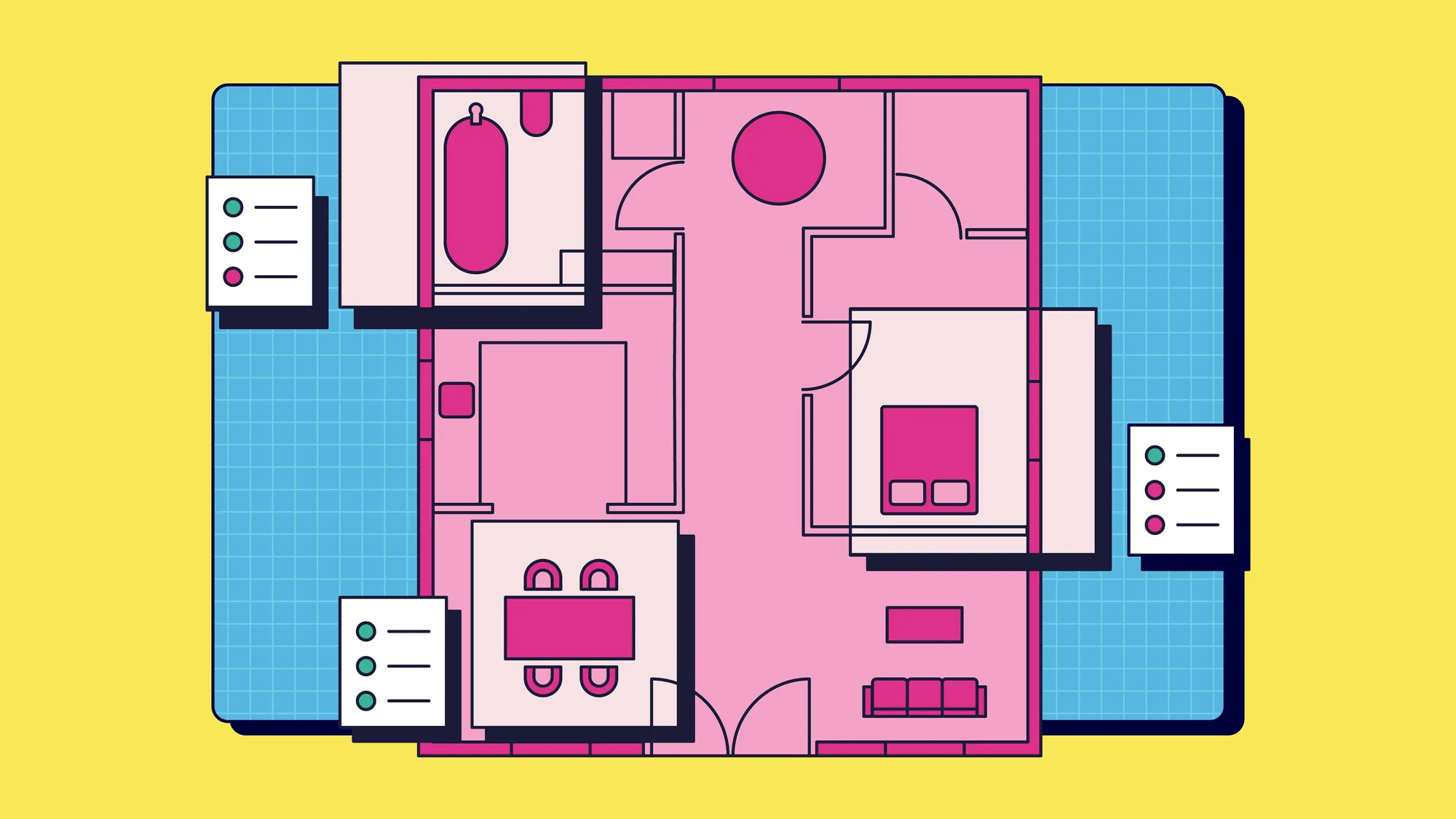
Barbie had apparently gone overboard with her love for abundant sunlight and open-floor layouts, and removed all the walls and doors from her home. This left her Dreamhouse alarmingly exposed to potential intruders. The risk of a break-in was higher than Barbie’s seemingly endless stack of high heels!
Barbie was at a loss, her eyes darting between the open-to-the-world living room and the defenseless staircase.
“Barbie, we need to give the Dreamhouse a security makeover,” CISO Barbie said. “But it won’t be so bad. You know, securing a dream house isn’t so different from protecting a cloud environment.”
CISO Barbie’s knowledge of cloud security was the perfect toolset to transform Barbie’s wide-open Dreamhouse into a secure yet glamorous sanctuary.
Dreamhouse in distress
As Barbie and CISO Barbie kicked off their Dreamhouse transformation, they summoned their reliable neighbor, Ken, for help. Known for his surfing abilities, Ken also held secret talents as an architect, construction worker, and building inspector. With CISO Barbie and Ken’s expertise, Barbie could surely fix up her home in no time.
But Ken was quick to burst Barbie’s pink bubble. He strolled through the Dreamhouse and immediately started rattling off hundreds of security violations.
According to Ken, Barbie’s deck was as unstable as a stiletto on cobblestones, not one of her staircases was equipped with handrails, and the ceilings were dropping lower than her tolerance for fashion blunders — it was an absolute disaster.
“Barbie, I think you need to start from scratch here,” Ken said. “We need to tear down the Dreamhouse and rebuild it.”
Fashionably safe
Barbie, CISO Barbie, and Ken started their ambitious mission by completely redesigning the Dreamhouse. And now it was CISO Barbie’s time to sparkle.
“Barbie, I think code security is exactly what we need to get started here. We use it all the time at work to automatically analyze code and identify weaknesses as we’re creating our cloud applications,” CISO Barbie said. “It saves us a ton of time because it helps us remediate misconfigurations, vulnerabilities, and compliance violations ASAP, before we actually start deploying code.”
As they delved into building the new-and-improved Dreamhouse, Barbie made strategic use of code security solutions. These tools enabled her to scrutinize the Dreamhouse floor plan, swiftly identifying security gaps, potential entry points for intruders, and any compliance violations. By rectifying these security issues during construction, they saved valuable time and resources, since these sorts of fixes are always more painful once the house has been built.
The perfect posture
With the design foundation firmly established, Barbie, CISO Barbie, and Ken shifted their focus to implementing cloud security posture management (CSPM) measures. This wasn’t about maintaining Barbie’s perfect stance on the runway — it was about implementing CSPM measures to ensure that Barbie could effectively manage the security of her Dreamhouse once it was built.
CISO Barbie, an expert at using CSPM tools in the cloud to uncover risks and ensure compliance, took the lead. “CSPM tools evaluate cloud environments, comparing them against industry best practices to identify potential security risks,” she explained.
“And for the Dreamhouse, we’ll apply the same principles. CSPM tools will help us detect any signs of intrusion, like an open window or door. It’s all about maintaining the perfect security posture,” CISO Barbie said.
The Dreamhouse wasn’t just going to be stylish, it was also going to be safe.
Protected in pink
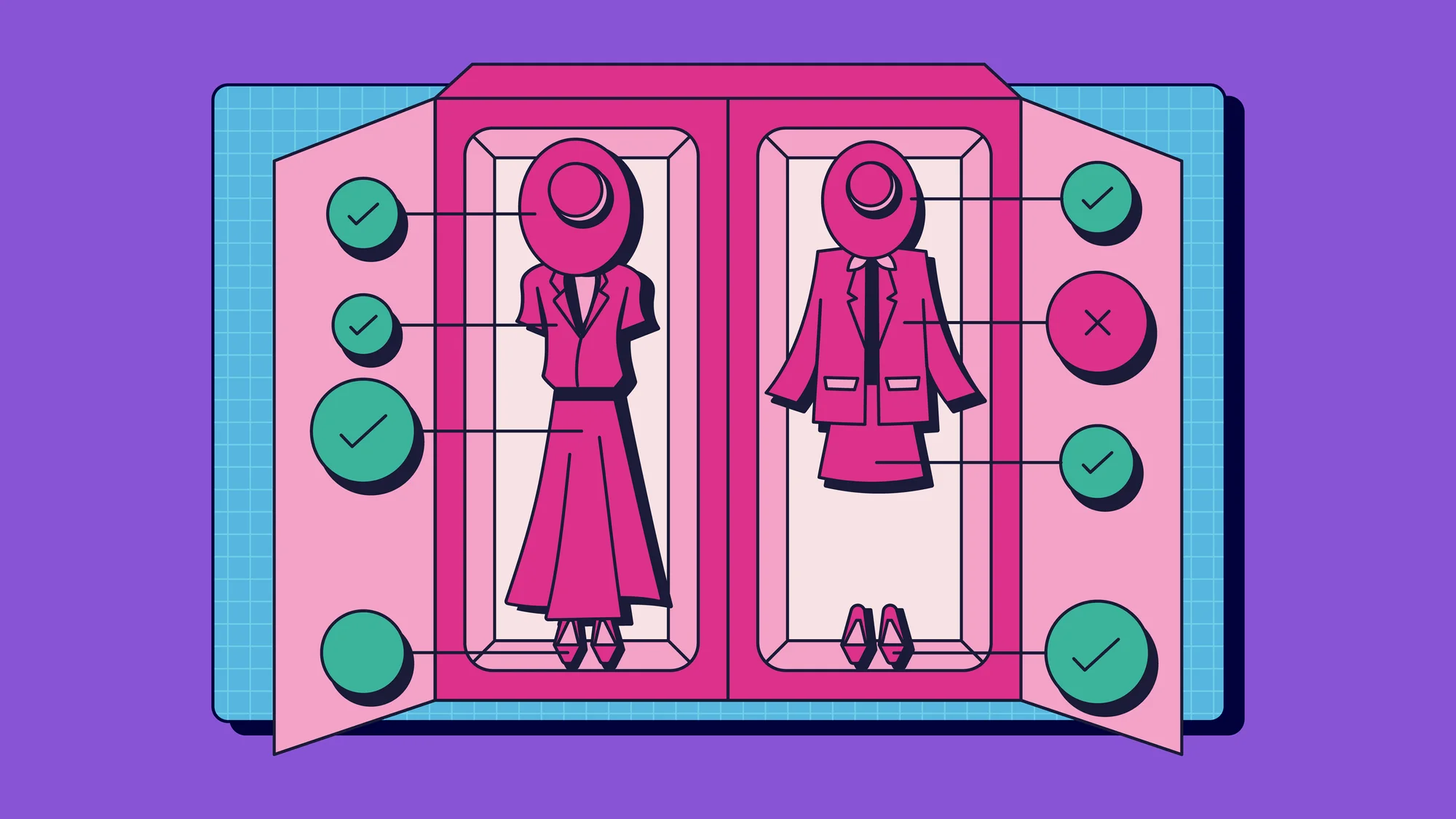
Next, our trio turned their attention to the crowning glory of the Dreamhouse: Barbie’s bedroom. Their mission was crystal clear: to outfit this fashion fortress with the precision and efficiency of Cloud Workload Protection Platforms (CWPPs).
Starting with an intricate surveillance system cleverly disguised as twinkling accessories, they introduced state-of-the-art locks and installed shatterproof glass on the windows.
But the piece de resistance was undoubtedly Barbie’s closet, a treasure trove filled with outfits that could rival any fashion week lineup. To protect these prized possessions, they deployed a CWPP to keep a vigilant watch on every item. Like an invisible security guard, it constantly monitored for potential threats or vulnerabilities, ensuring that Barbie’s fashion secrets stayed as exclusive as a VIP party. At the first sign of any suspicious activities, the CWPP would alert Barbie, enabling her to view the situation on her phone’s app instantly.
In the cloud, CWPPs serve as guardians of every process and application. They shield against unauthorized access and raise the alarm the moment a potential breach is detected. Our team was bringing the same level of protection to the Dreamhouse, creating a fashionably safe haven.
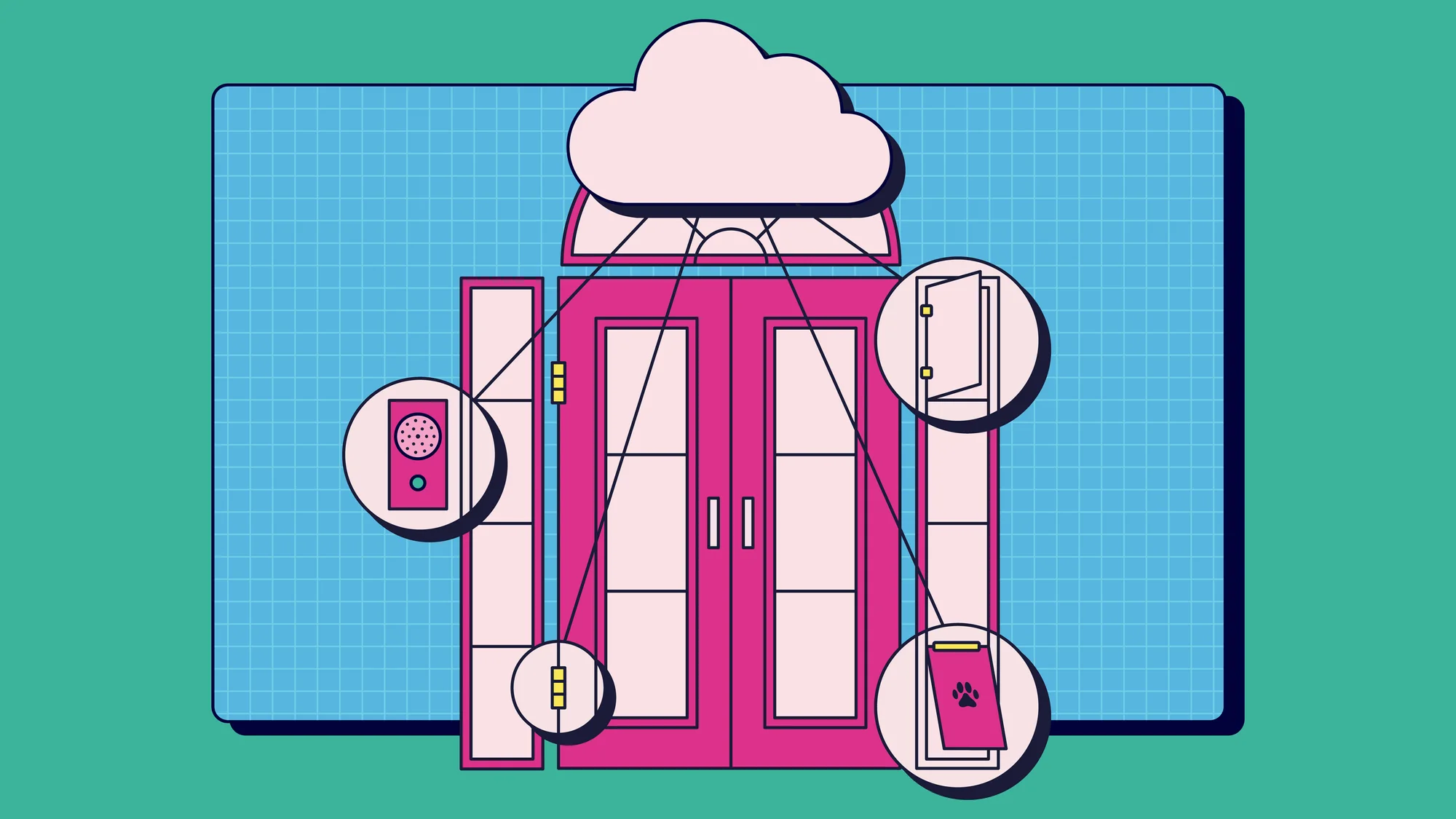
Who has the keys to the Dreamhouse?
Just as a sophisticated hostess exercises discretion over her guest list, Barbie wanted to regulate access to her Dreamhouse and its various rooms. Barbie entrusted Cloud Infrastructure Entitlement Management (CIEM) solutions to control who could enter specific areas within her home. The ultimate key bearer, CISO Barbie, was granted an all-access pass to the Dreamhouse, while Ken received a security code with limitations on areas he could access.
In the cloud, CIEM solutions function similarly, as the guardian of access permissions, dictating who (or what) can enter specific areas of cloud infrastructure. CIEM solutions are used to manage permissions to cloud resources and ensure that individuals and services have only the minimum necessary privileges to carry out their jobs.
The CNAPP secret spilled
With all of the Dreamhouse’s new security controls in place, it seemed like Barbie, CISO Barbie, and Ken could finally relax. As they were cleaning things up, Barbie stumbled upon a crumpled note hidden under a pile of security manuals. She unraveled it, her eyes widening as she read its contents aloud. “Do not, under any circumstances, tell Barbie about CNAPPs.”
Barbie turned to Ken with a perplexed expression. “Ken, what in the world is this? This is your handwriting!”
“Barbie, I… I just wanted to spend more time with you,” Ken admitted, revealing his intentions to keep CNAPP a secret.
Barbie’s confusion was quickly cleared up as CISO Barbie explained that a CNAPP stands for Cloud Native Application Protection Platform. CNAPPs are security tools that combine various cloud security capabilities into one holistic platform. They provide a more efficient approach by breaking down cloud siloes, ingesting data across the cloud, and making sense of it all through automation.
“So basically, we could have saved a ton of time by consolidating and using a CNAPP instead of all of those different tools and technologies we used to make the Dreamhouse secure,” CISO Barbie said. “But Ken wouldn’t let me tell you about it!”
“Well, Ken, that’s sweet and all, but next time, let’s not hide incredibly useful tools, okay?” Barbie said.
As they laughed and admired their secure Dreamhouse, CISO Barbie added, “And when we’re redoing my house, Ken, we’re absolutely using the CNAPP!”
✨✨ ✨
We couldn’t resist joining the Barbie security fun this summer, and just like CISO Barbie, we’re passionate about cybersecurity. Schedule a meeting with us to learn how our CNAPP can turn your cloud into a dream cloud, and see the new Barbie movie on us.
Note: The ‘Barbie’ name, brand, and likeness is a trademark of Mattel Inc. and not affiliated with Lacework.
Suggested for you