Lacework adds cloud entitlement management to its leading CNAPP
Editor’s note: This blog announces the private preview release of cloud infrastructure entitlement management (CIEM) capabilities from Lacework, the latest enhancement to our data-driven CNAPP. With this new set of capabilities, organizations can enforce the principle of least privilege when building, deploying, using, and managing cloud infrastructure services.
If you’re reading this blog, chances are you live in a city or town.
Your city or town is likely filled with buildings, each serving a different purpose, from office spaces, restaurants, and apartment buildings to post offices and retail stores.
And if you’re taking the time to read this, it’s also probably safe to assume you know something about cloud computing. You know the cloud is made up of processing capabilities, networking, resources, and storage. Maybe even a container or two — or 5,000.
In a way, your city and the cloud are similar. They’re collections of entities, each with a unique purpose that’s essential for the functioning of the whole.
Now, imagine that the people who live and work in your city represent the cloud users, applications, and services that require access to those entities. What if each of those people had keys to everything in the city — every apartment, every bank, every store? Well, that wouldn’t make sense.
Yet that’s often how we run our cloud environments. And it breeds a host of problems. But there’s a way to make it right.
Introducing cloud infrastructure entitlement management (CIEM) with Lacework
The cloud may have started simple, but it’s become infinitely more complex — especially when it comes to entitlements. In fact, the three largest cloud service providers now have over 35,000 permissions (and counting). And, for one reason or another, most cloud resources have way more access than they need.
For nearly a decade, Lacework has been committed to helping companies manage and remediate cloud risks and threats. Today, Lacework is extending this mission to cloud identity risk. With Lacework CIEM, security teams gain the ability to easily manage cloud identities and their associated permissions and achieve their least privilege objectives.
With Lacework, organizations can now:
- See all cloud identities
- Know precisely who can perform which actions
- Surface high-risk identities based on identity risk score and attack path analysis
- Automatically receive recommendations for right-sizing permissions based on observed usage
With these capabilities, organizations can now reduce identity risk and limit any impacts related to compromised credentials and accounts.
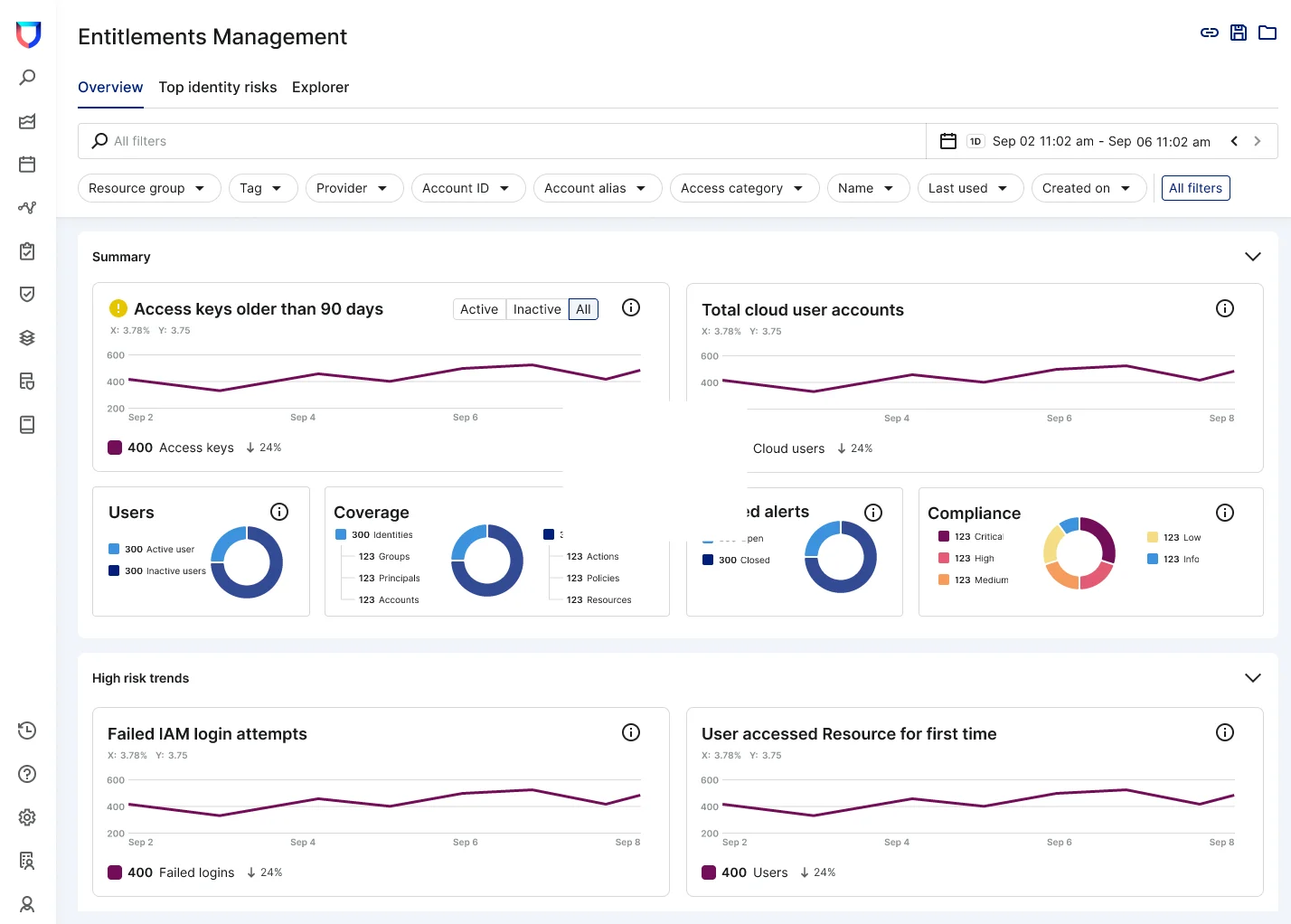
Gain continuous visibility of identities and permissions
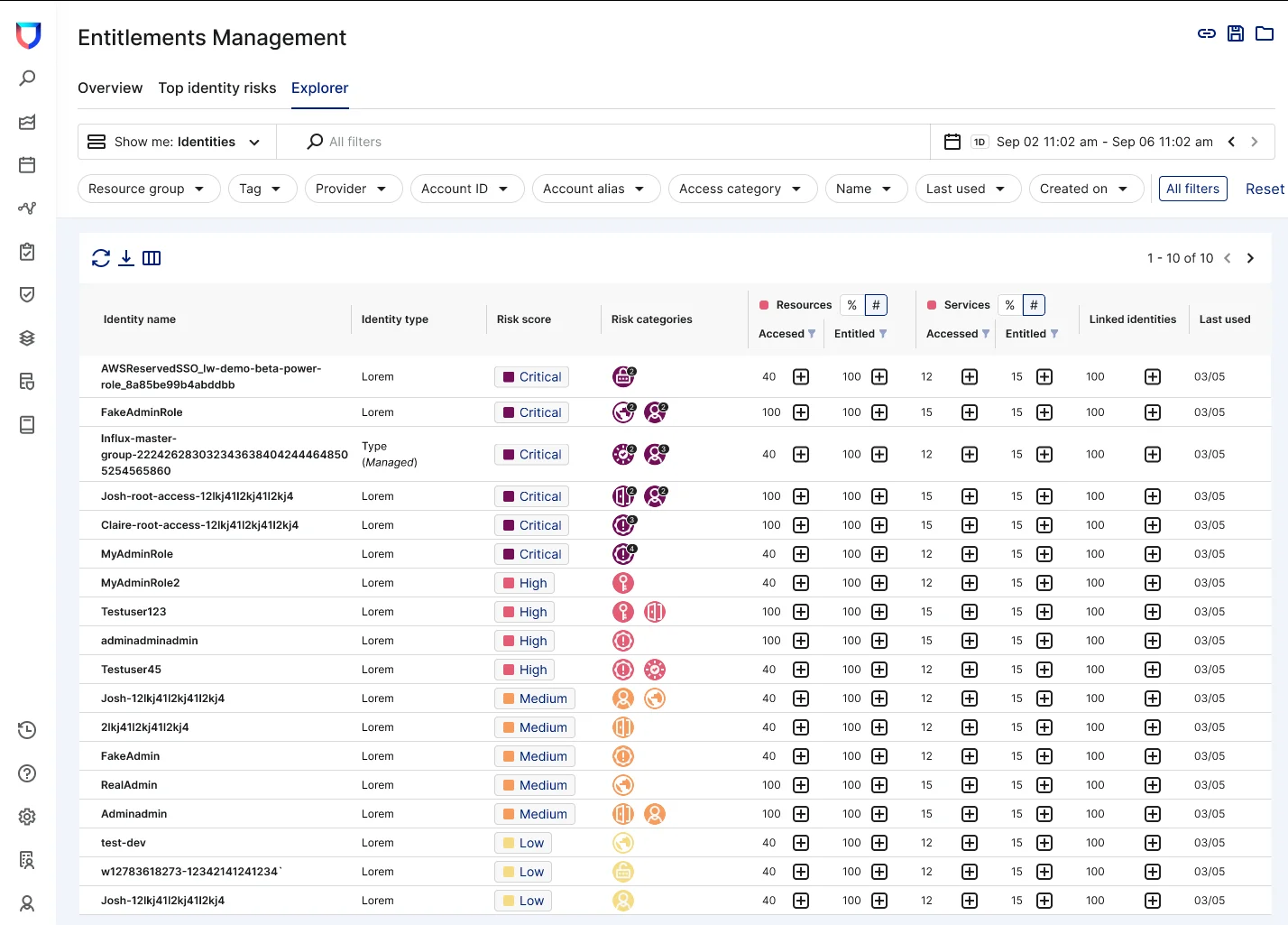
Assessing identity risk starts with visibility, but having an up-to-date inventory of cloud users, resources, groups, and roles is difficult. Lacework now continuously discovers cloud identities and their associated entitlements and presents them within a single view. Teams can explore and investigate identities and their permissions. They can identify the services that an identity has access to and any related identities capable of assuming that identity’s privileges (or, conversely, any identities from which the identity can assume permissions).
With Lacework CIEM, security teams can easily manage cloud identities and their associated permissions.
Further, Lacework automatically correlates identity and resource-based permissions, permission boundaries, as well as service control, trust, and session policies to calculate the net-effective permissions for each identity.
Back to our city analogy — the Lacework platform can run a census for your city and can determine who has the keys to what. And it’s not a once-in-a-decade census; it’s a census that’s always up-to-date.
So, the next time your CEO or compliance officer needs to know which identities have access to a high-value database and what actions each can perform, you won’t break out in a cold sweat. And if you’re worried about which users, applications, and services have excessive permissions, fear not — Lacework helps with that too.
Know which identities are overly-permissive
Lacework reveals which users, resources, groups, and roles have excessive permissions, by automatically comparing each identity’s granted permissions against those that they have actually used. We continuously ingest event and activity data from cloud services like AWS CloudTrail to break down the permissions and actions of each identity, including whether it’s active or inactive, and provide unique insights.
This way, organizations can clearly see which human and machine identities are inactive and for how long. They can also see which entitlements a given identity has never used or rarely uses. For instance, if they uncover a user with permission to add entitlements for themselves or other identities but hasn’t done so in the past 180 days, it may be time to rethink that policy.
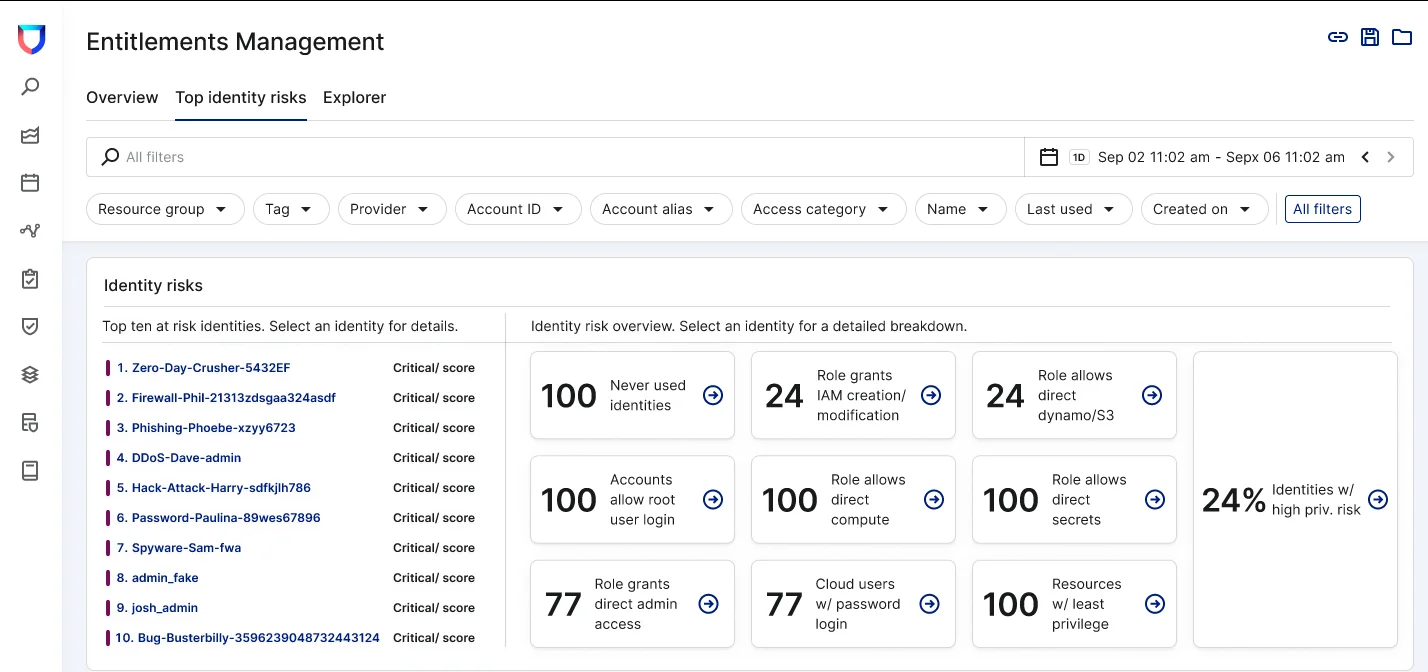
Prioritize identities that pose the greatest risk
While identifying unused identities and permissions is a critical step in understanding identity risk, how will teams know which ones to mitigate first? After all, just like any other facet of cloud security, your list of potential fixes is likely to be really long. And, just like any other facet of cloud security, no two fixes are inherently equal in potential impact on your environment.
Lacework helps here too. Similar to our recent custom risk scoring platform enhancement, the Lacework platform calculates a risk score for each identity, based on multiple factors such as excessive permissions, low usage, hard coded secrets, and compliance violations. Risk severity is determined based on a number of properties, including unused admin and identity and access management (IAM) write privileges, toxic combinations, privilege escalation via role chaining, and more.
In addition, Lacework uses attack path analysis to illustrate how an attacker could use an overly-permissive identity to gain access to high-value resources like an Amazon S3 bucket or Relational Database Service (RDS) database. This allows security teams to holistically understand an identity’s relationship to an attack path and to pinpoint the handful of identities that will make the biggest impact in reducing their attack surface risk.
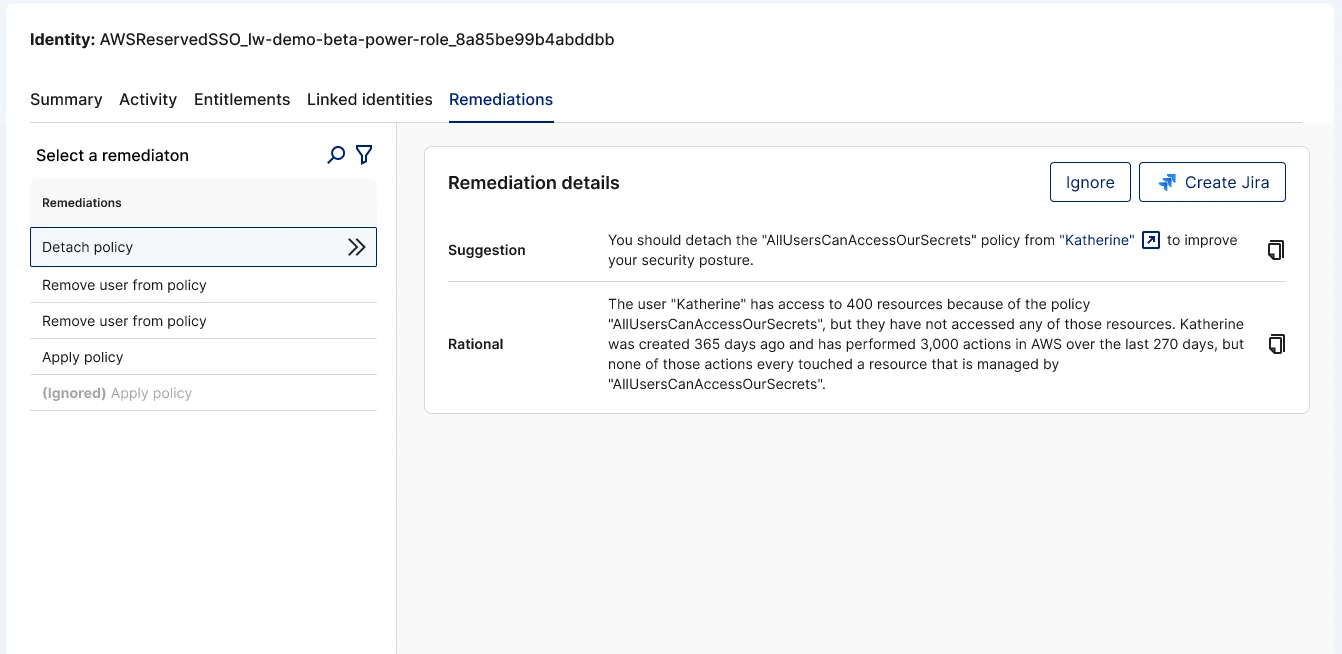
Right-size entitlements, reduce identity risk
With a clear understanding of which identities need immediate attention, security teams need guidance on what policy changes are required to reduce the risk associated with overly-permissive identities. Lacework automatically generates suggested changes for scoping down and right-sizing permission artifacts based on risk assessments and historical usage observations.
Lacework automatically generates suggested changes for scoping down and right-sizing permission artifacts.
Our remediation suggestions allow security teams to recommend — with high-confidence — policy changes such as removing a policy from a specific user, to reduce the risk and potential impact from a security incident. These high-confidence suggestions will also allow you to execute the most impactful identity security fixes without fear of revoking needed permissions and, thus, disrupting workflows for other teams operating in your cloud environment.
From identity crisis to identity control
Just like a well-managed city would need to ensure secure and efficient use of its buildings, the same applies to cloud infrastructure. It prevents unauthorized access, reduces the risk of security breaches, and ensures resources are used efficiently.
Remember, a city without proper regulation could descend into chaos, with people accessing buildings they have no business in, or crowding into resources leading to inefficiency. Similarly, a cloud environment without robust entitlement management is vulnerable to internal and external threats, data breaches, and inefficient use of resources.
Thankfully, Lacework CIEM can ensure that’s not the case.
Ready to take the next step in your cloud security journey? See how Lacework can help you understand your cloud identity architecture, identify overly-permissive identities, pinpoint the ones that pose the greatest risk, and right-size permissions to achieve least privileged access and reduce your identity risk.
Suggested for you