Know your enemy:A look at 4 common attack paths

As cloud threats grow in volume and sophistication, it is almost impossible for businesses to fix every risk or vulnerability in their cloud environment. The lack of skilled cloud security professionals trying to keep pace under pressure only adds to the challenge. Instead of trying to fix it all, the focus now needs to be on how to quickly identify and prioritize the greatest risks facing cloud resources and data.
Thankfully, that’s possible. Today, we can turn the tables on attackers by focusing on the most critical attack paths using your new favorite secret weapon, Exposure Polygraphs.
Wait, what’s an Exposure Polygraph?
An Exposure Polygraph lays out the connections between risky assets from the perspective of an attacker. It visually illustrates potential attack chains and displays details about host and container reachability, critical vulnerabilities, exposed secrets, and misconfigurations — all from a single view. This information is easy to understand and helps you see the connections between your riskiest assets and prioritize your actions to reduce the biggests risks first.
How does it work?
The Lacework® Polygraph® Data Platform uses configuration data and audit logs to create an attack path analysis. This helps organizations prioritize risk-based remediation and alert investigation by correlating risk factors like vulnerabilities, network reachability, secrets, and identity and access management (IAM) roles (from multiple sources) in a single view.
This information is displayed as an Exposure Polygraph when a user clicks on an alert. The alert contains details about host and container reachability, critical vulnerabilities, exposed secrets, misconfigurations, and more.
Let’s take a look at some actual attack path scenarios.
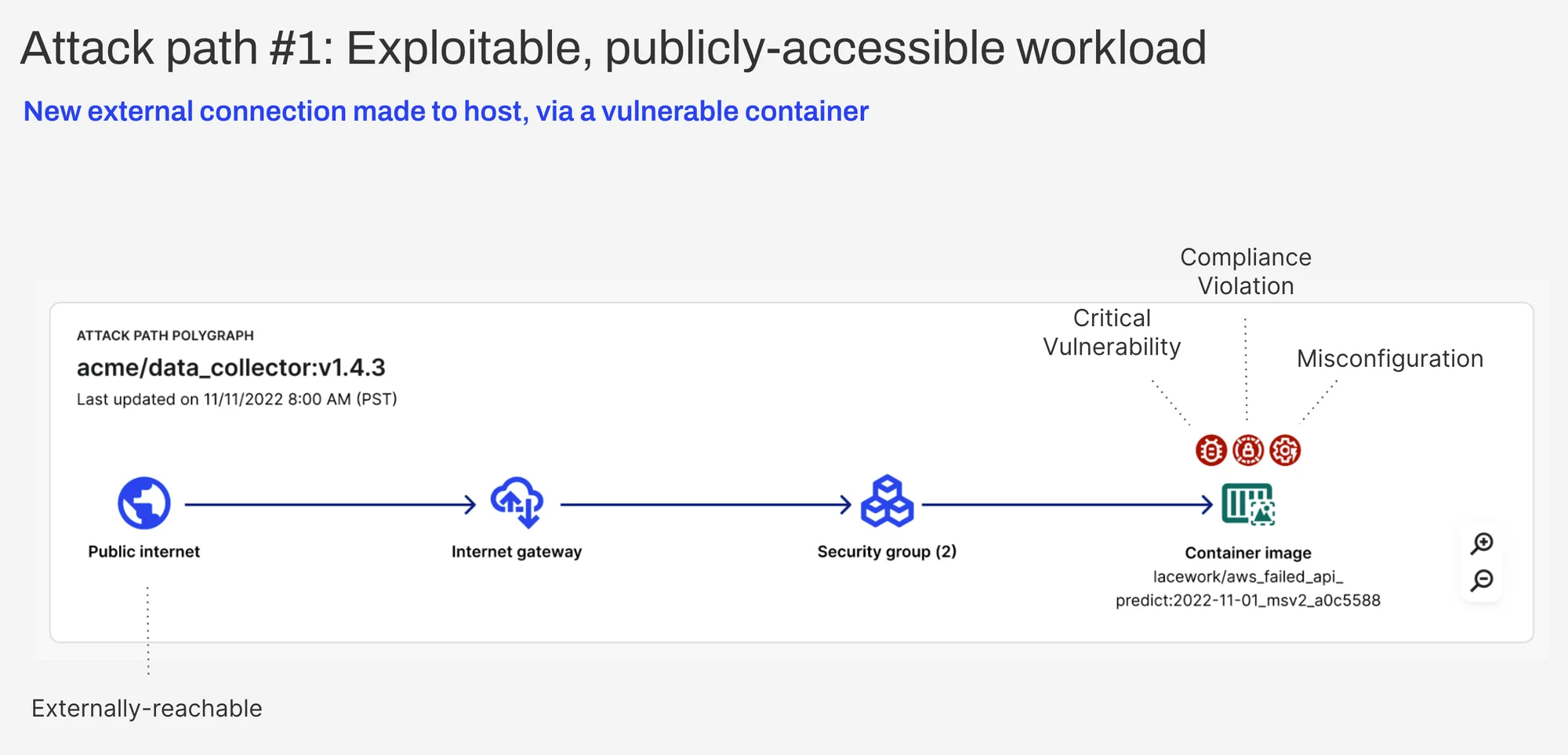
Attack path #1: Exploitable publicly-accessible workload
Attackers can access a public workload because it is exposed to the internet. If a workload has vulnerabilities, it’s even easier to exploit.
Vulnerabilities are one of the top attack vectors in the cloud. 82 percent of attacks on organizations in Q1 2022 were caused by the external exposure of known vulnerabilities. By leveraging the publicly available exploit, attackers were able to enter the victim’s cloud environment.
Once access is granted, the sky’s the limit. Bad actors can use resources for illicit cryptomining and other malicious activities, or they can exploit related risks for privilege escalation, data compromise, and far worse things.
Prioritized patching is key
Every day, new and dangerous vulnerabilities are identified. But patching everything in your cloud environment is virtually impossible. How do you know where to begin?
What’s risky to one organization, may be less risky to another. The challenge is prioritizing the list of to-dos based on the greatest risk facing the organization. To prevent exploitation of external vulnerabilities, organizations first need to understand their attack surface and know the risk of the attack vector and what’s happening in their production environment. Without this visibility, it’s just a guessing game.
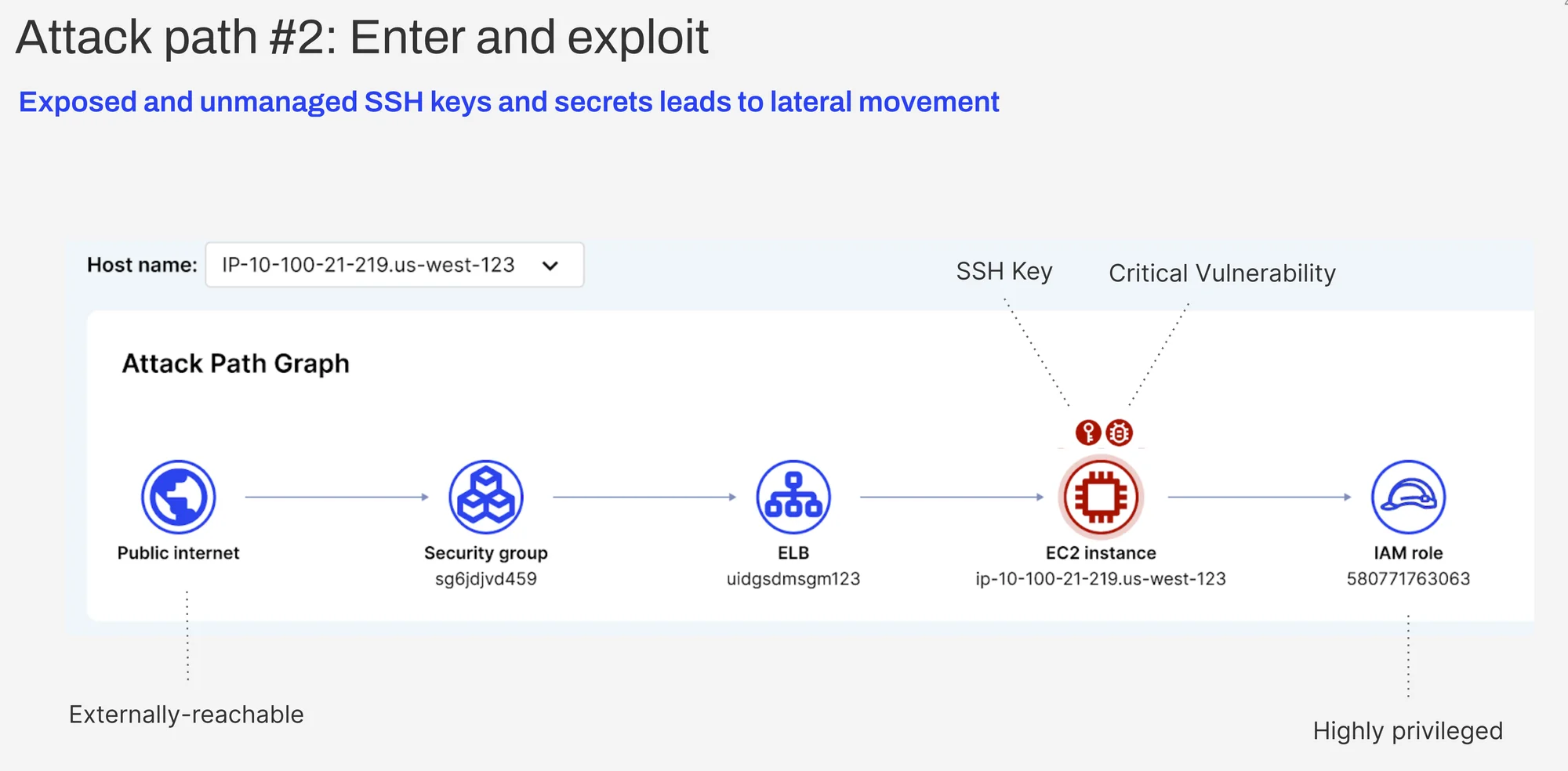
Attack path #2: Enter and exploit
Upon entry, malicious attackers seek to exploit and steal unsecured API credentials, private SSH keys, and other secrets. They move through the networks undetected, perform SSH attacks, and access more systems and privileges.
Bad actors love SSH keys because they are widely used to secure access and connections to remote systems like servers, routers, firewalls, and networks through elevated privileges. With a stolen key, attackers can access any server or system where that private key is used for authentication. Once they are in, they use these elevated privileges to find or create a key that allows access to another server or system, ultimately allowing the attackers to move laterally to compromise the system.
With Exposure Polygraph, you can clearly see if an SSH key in your environment can be misused by an attacker for lateral movement.
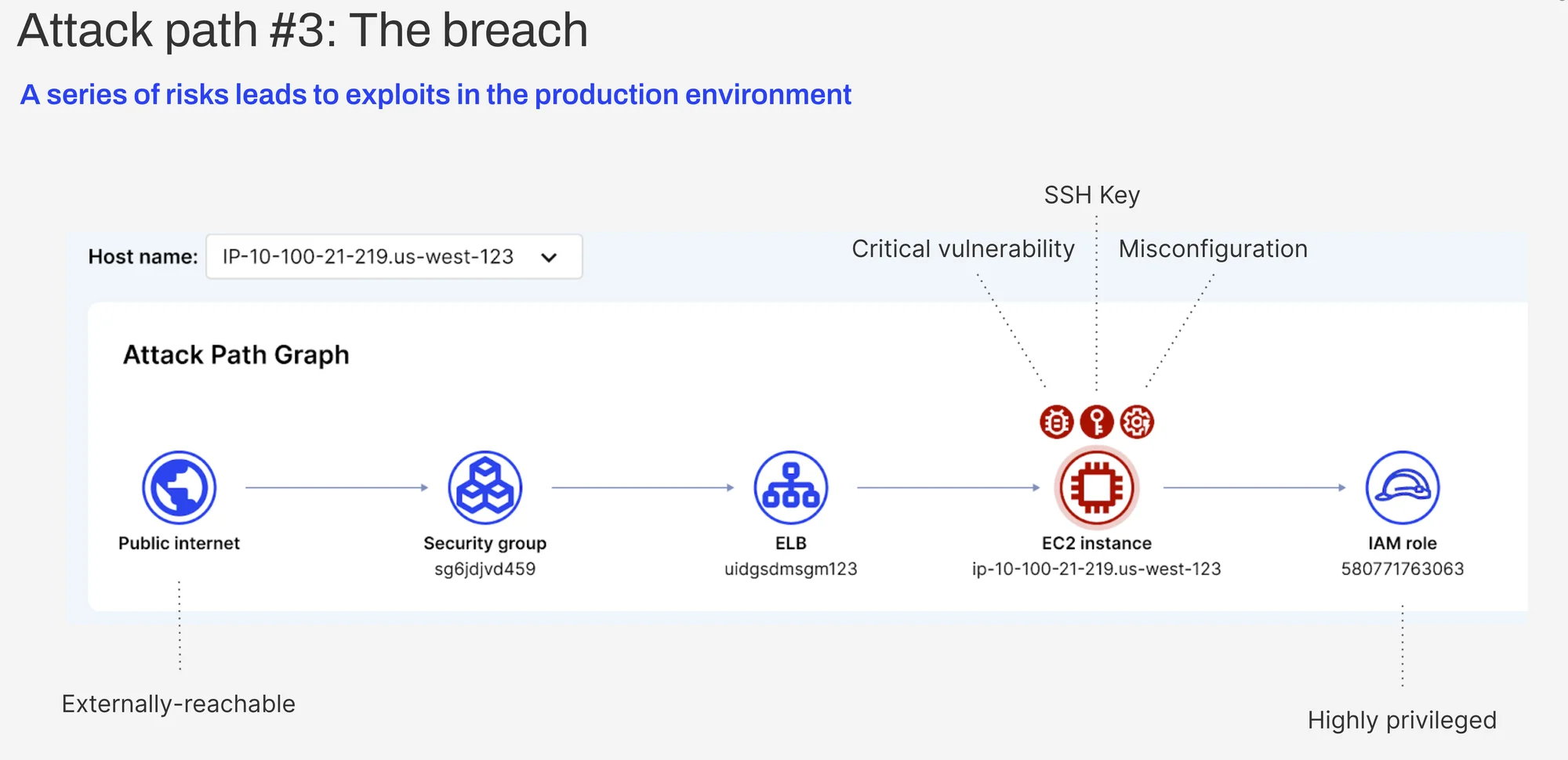
Attack path #3: The breach
When a bad actor gains access to a sensitive database or resource, how will you know? Using Exposure Polygraph, you can visualize the relationships between the host and related risk factors. In this scenario, our Polygraph Data Platform detects an anomalous process or network behavior on a cloud workload and issues an alert that correlates all the risky configurations that could have led to that behavior.
This additional layer of context is critical in protecting against a breach. For example, if the workload has a vulnerability on an internet-exposed host with plain text SSH keys, cloud API credentials, or a highly privileged IAM role, you can instantly see the connections.
Then our platform takes it one step further. By combining potential risks with what’s actually happening in your cloud environment, you can see a complete picture of your true risk. This makes it easy for teams to triage alerts and proactively prioritize the most impactful attack vectors from a single view.
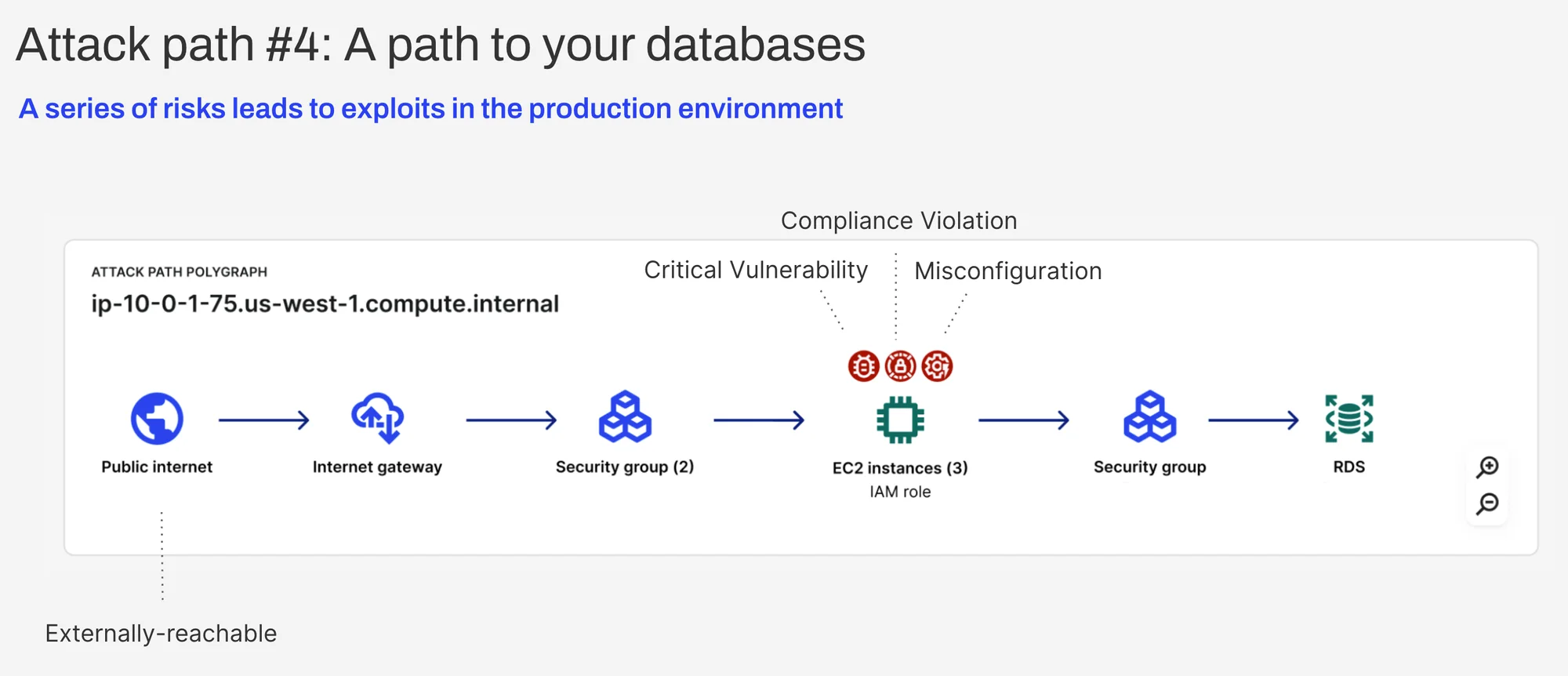
Attack path #4: A path to your databases
Amazon defines its Relational Database Service (Amazon RDS) as a “collection of managed services that makes it simple to set up, operate, and scale databases in the cloud.” RDS is an extremely popular offering that paves the way for brands to more easily build applications and break free from legacy databases. In fact, over 500 Lacework customers are leveraging 10+ RDS instances.
As the primary data persistence layer for so many of our customers, it’s critical to understand the security posture of RDS (and other such database services) and how attackers could maneuver in your environment to gain access to this “crown jewel.” While RDS should never be directly exposed to the internet, an attacker could create an intermediate foothold (via a vulnerability, misconfiguration, or other risk) on one workload in your environment, then move laterally to gain access to this database.
Uncovering an attack like this is no easy task. The complex web of network configurations and risks is difficult to understand and manually analyze. Lacework can automatically assess these multi-hop paths to RDS and can clearly identify the high-risk vulnerabilities, compliance violations, and secrets that could lead to RDS compromise.
What’s in it for you?
Knowing what to fix and when to fix it is priceless. One of our customers said it best: “Everything can’t be a ten out of ten.” Knowing what’s happening and how to protect against your biggest risks is the holy grail of security.
With Lacework, you can receive:
- Alerts that deliver context
Combine exposure path visualizations with real production data so security administrators can understand the connections and uncover the biggest risks facing their environment.
- Simple, actionable data
Prioritize remediation efforts to limit exposure, while equipping incident response teams with accurate and reliable information for faster fixes.
- Single source of truth
Share information across teams and reduce the mean time to respond by providing access to all necessary incident information in a single view.
By taking a data-driven approach, all teams — posture management, incident response, and security teams — get a visualized single source of truth to help them secure their environment.
In the words of another Lacework customer:
“With a cloud environment as complex as ours, [having a] clear understanding of what we consider the most important attack surface is key for every investigation, and creates a shared understanding of importance between security and development.”
Think like an attacker
Lacework is the only vendor that combines the ability to see potential risks from the lens of an attacker with the knowledge of what’s actively happening to uncover attacks without needing to write a single rule. This enables customers to prioritize mitigating the most critical risks and automatically detect if or when they are exploited.
If you’re tired of patching together too many point solutions and sifting through silos of data, you may want to give yourself (and your team) a break and get a demo or free trial of Lacework. Our platform puts your data to work for you — automatically. Experience easy prioritization, risk-based remediation, and speedy investigation, all from a single place.
Categories
Suggested for you