How Lacework Explorer can protect your data from risky identities
Identity sprawl is a growing problem for companies of all sizes. As organizations expand, the number of user accounts and permissions multiplies quickly, making it nearly impossible for security teams to maintain visibility into who has access to what. Lacework users stay one step ahead of this challenge by pinpointing critical assets, often referred to as 'crown jewels,' that are vulnerable due to identities with excessive privileges. Identifying these assets is crucial because these privileges significantly expand the company’s attack surface, exposing numerous critical assets to potential threats.
Keep identity sprawl in check
Lacework Explorer presents an all-new way of visualizing the relationships among cloud entities and their associated risks, using advanced analytics and graph-based exploration capabilities to give users a granular view of their cloud infrastructure.
In this blog, we will explore how Lacework Explorer uses cloud infrastructure entitlement management (CIEM) to effectively identify unused identities that hold excessive privileges to critical assets. Lacework CIEM provides all the context required to fine-tune entitlements and ensure that only necessary permissions are granted (according to the principle of least privilege). This is particularly crucial in preventing privilege escalation attacks and reducing the risk of insider threats.
With the visualization capabilities of Lacework Explorer and cloud identity context provided by CIEM, security teams can easily pinpoint redundant privileges, and streamline permissions without affecting business operations. As a result, the Lacework user ensures that production systems remain both secure and efficient.
Lacework Explorer step-by-step workflow
To execute this workflow, a Lacework user would follow these steps:
- Log in to Lacework and open Explorer.

- Build the query matching the conditions. Show all risky instances that can reach critical assets that include S3 buckets, RDS, etc. Risky instances are defined by the hosts that are internet exposed and have vulnerabilities with either critical or high severity. Enhance this prioritization by leveraging the Lacework agent that focuses exclusively on vulnerable packages actively running on hosts.

- Click on Search to get visibility of all risky instances that can reach critical assets.
- Quick priority: This list is ordered by host risk to help with quick prioritization as shown in the table below.
- Click on View in Graph corresponding to the first host vulnerability showing a high host risk score of 10/10.

- The graph offers quick visibility of the identity risk.
- It shows all critical assets (crown jewels) accessed by the identity.
- More importantly, the graph provides visibility that this identity can be assumed by risky, internet-exposed assets.
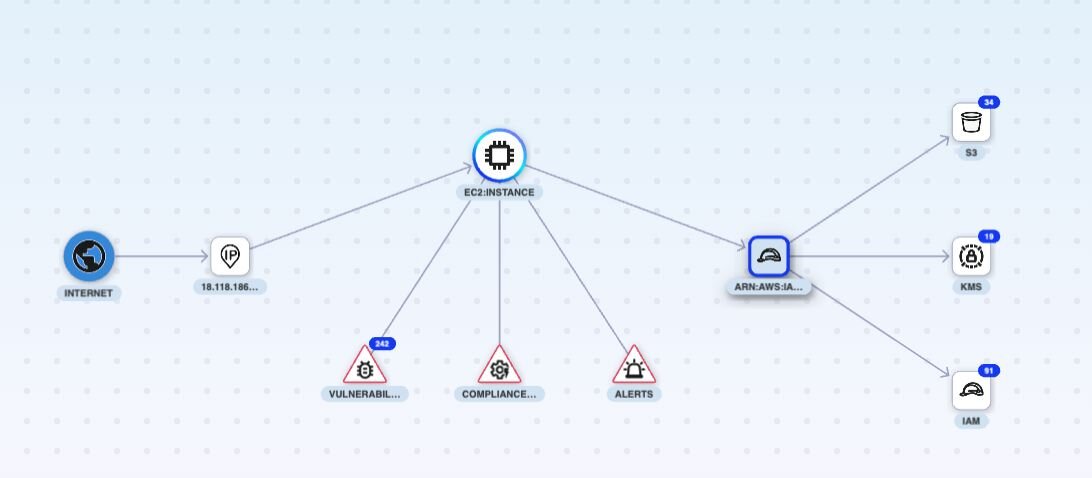
- Click on the AWS role to see additional information on the associated entitlements.
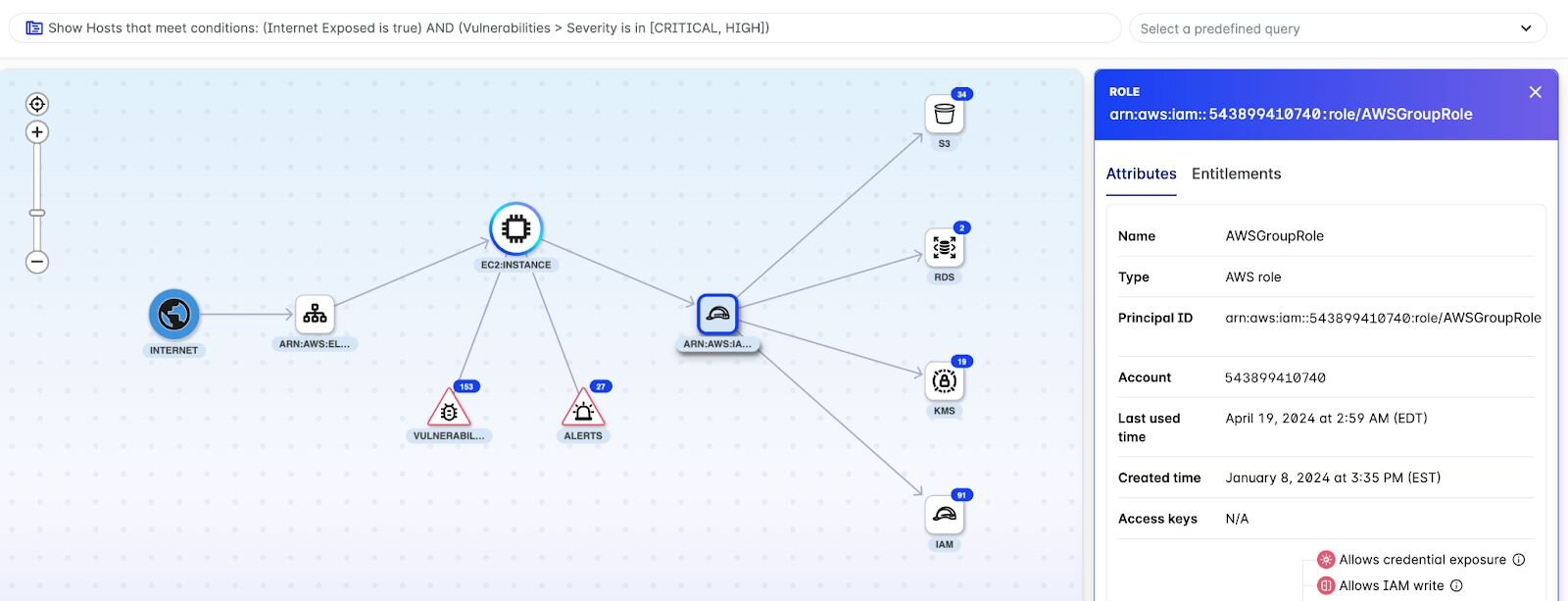
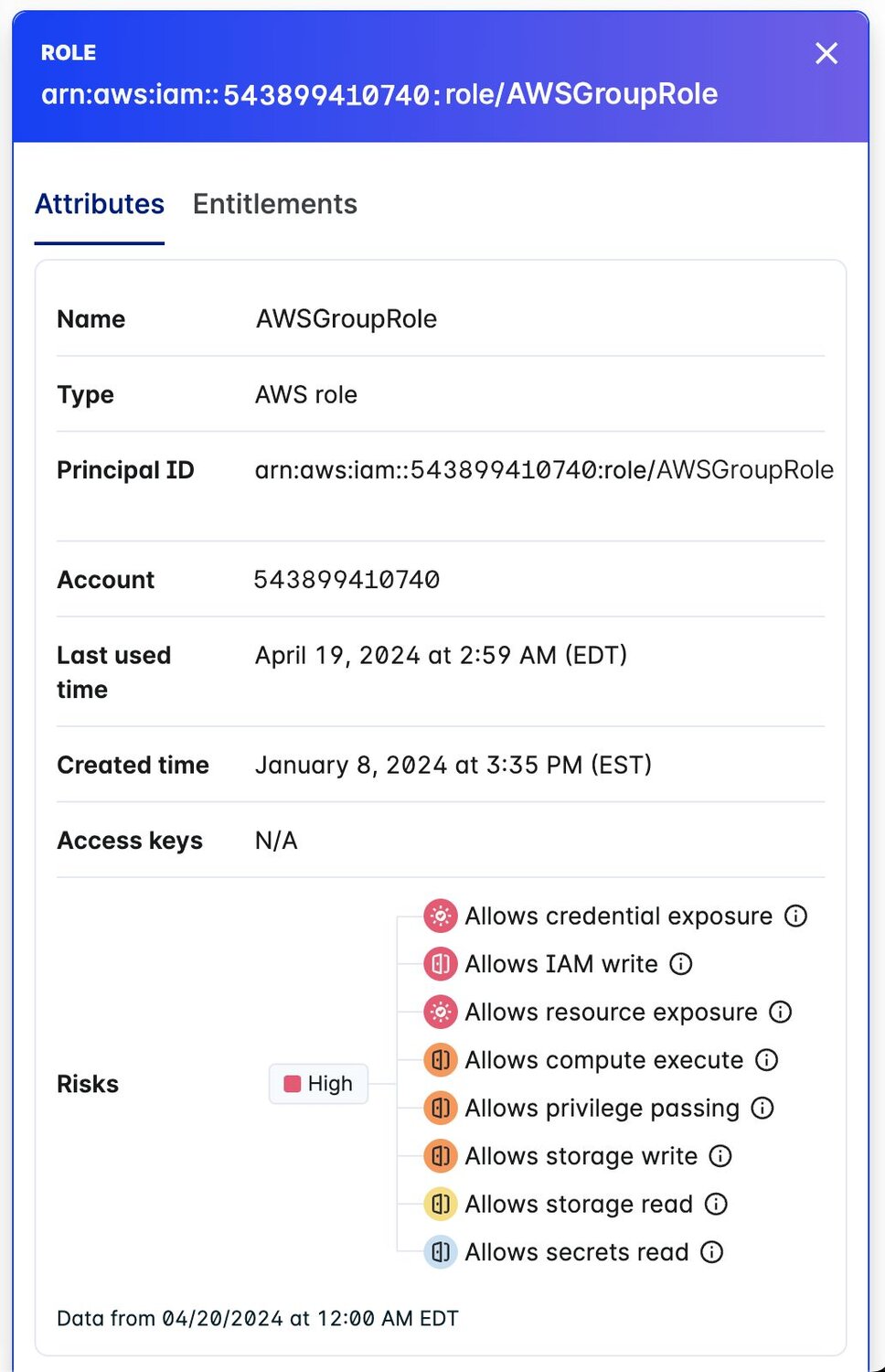
- The context panel shows important information on the identity and all of its respective entitlements. This particular identity risk is high because of all the factors described, including:
- Allows credential exposure
- Allows full admin
- Allows IAM write
- Allows resource exposure
- Critically, the risks around full admin access should raise red flags for any security team.
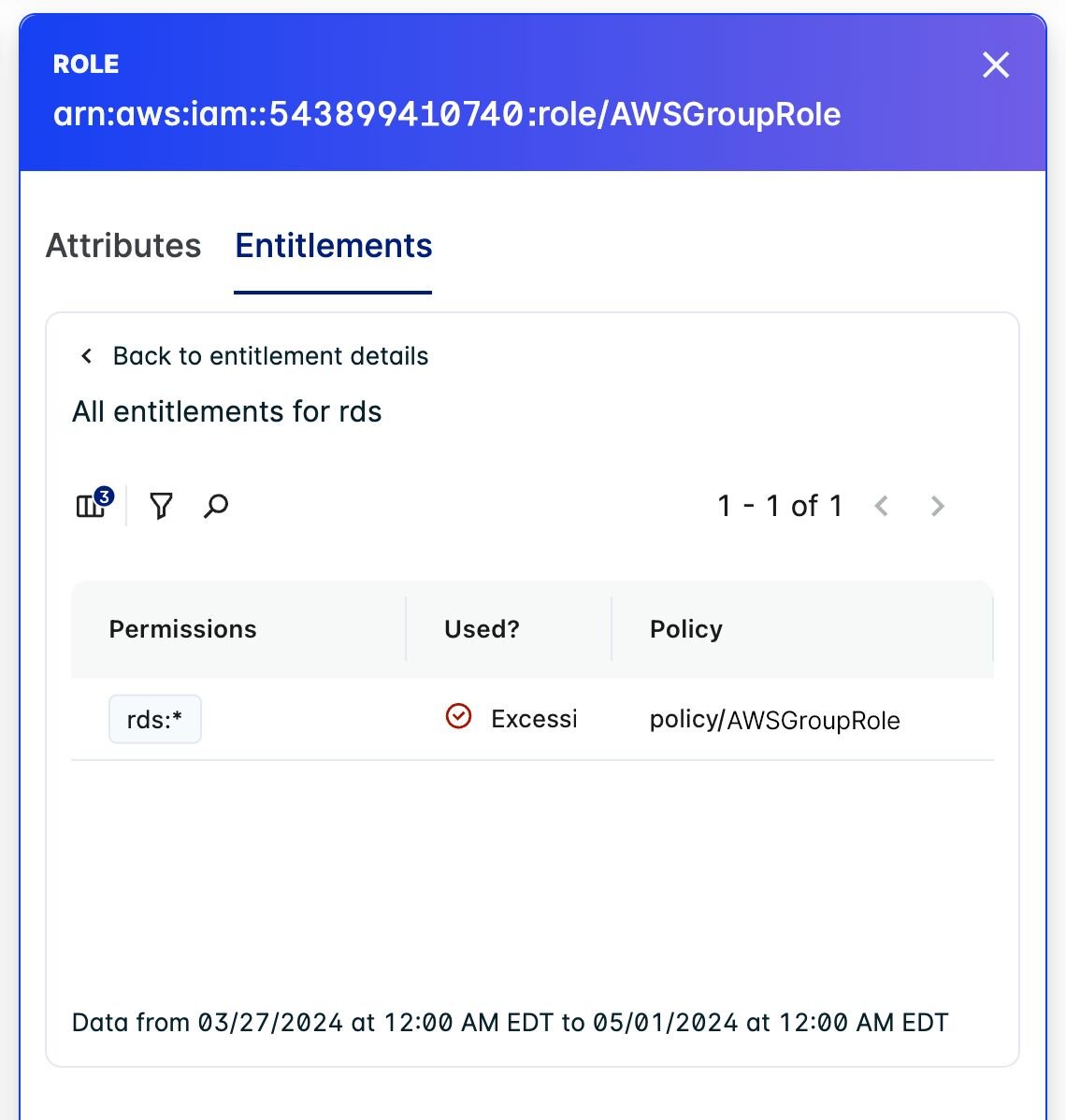
- Clicking deeper into the entitlements, the relationships among all services are shown.
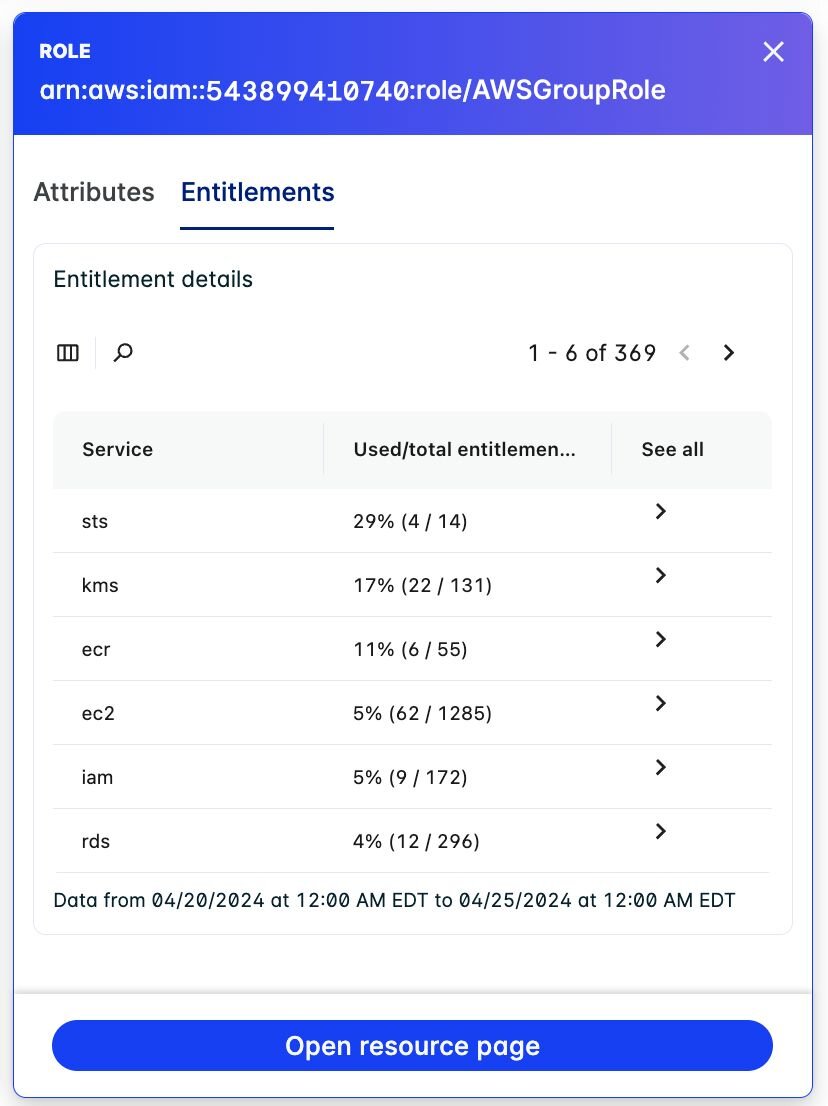
- The visibility of unused entitlements is apparent when searching for the critical asset like S3 and RDS. As shown below, this identity has 148 entitlements; none of which have been used.
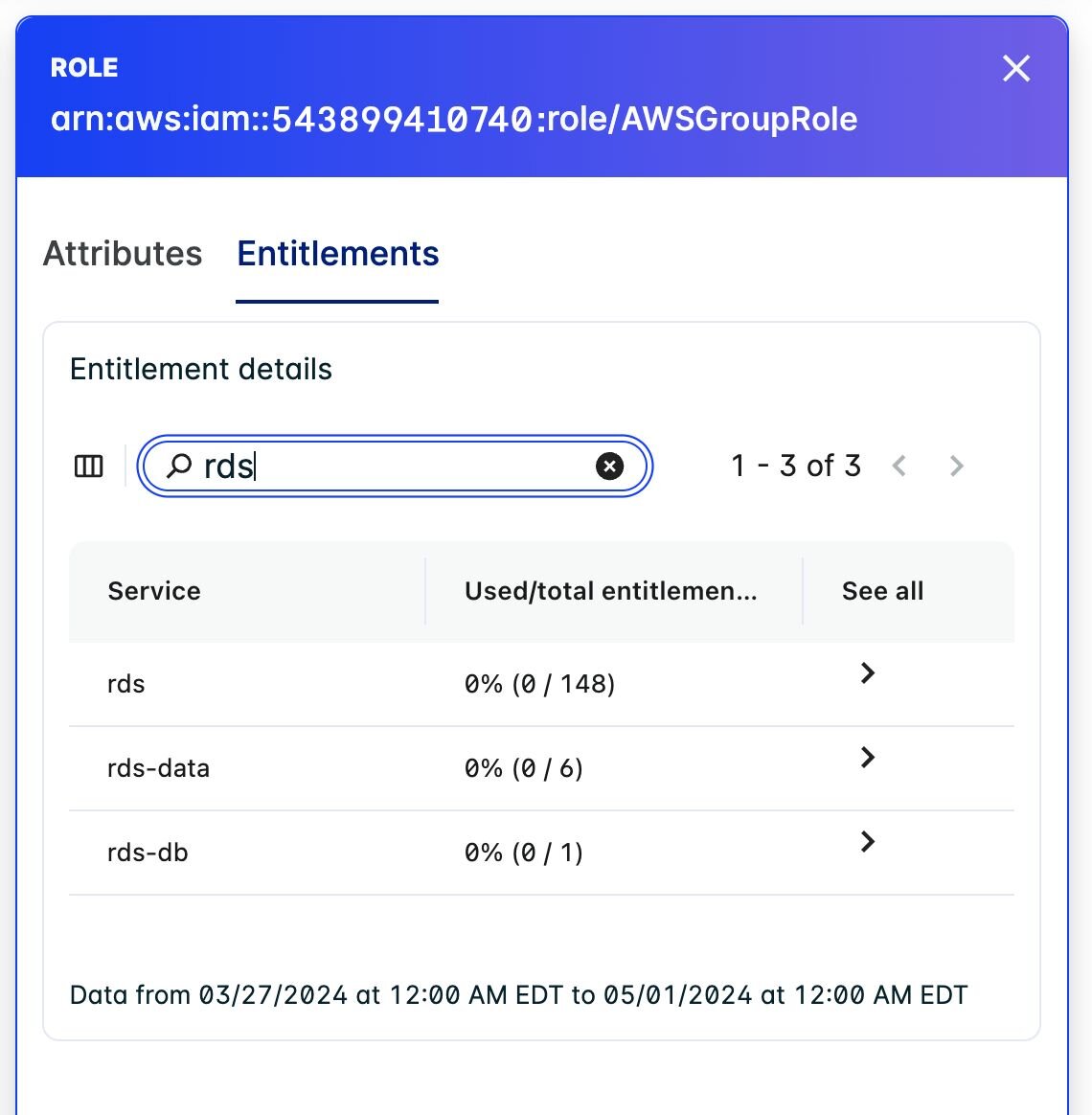
- Identification of excessive entitlements is possible through navigating into the exact entitlement. To mitigate this identity sprawl, It is recommended to rightsize the permissions by adjusting the policy to have only appropriate entitlements.
Save time and secure your cloud with Lacework Explorer
This walkthrough shows how Lacework Explorer easily enables users to query for the crown jewel assets that can be accessed by risky instances via an identity. The explorer graph enables users to get full context on all the affected services due to an over privileged identity. Users are able to quickly get visibility into the excessive privileges by exploring the context for each entitlement; then, they’re able to prioritize the next steps that involve streamlining permissions without affecting business operations.
Learn more about Lacework Explorer in the solution brief or schedule a demo.
Learn more about lacework explorer
Read the Solution Brief
Categories
Suggested for you


