ELF of the Month: Linux DDoS Malware Sample
James Condon
Director of Research, Lacework Labs
Each month we take a look at a malicious Executable and Linkable Format (ELF) file, the common executable file format for Unix and Unix-like Operating Systems, and share details about the sample. In this edition of ELF of the Month, we take a look at a Linux DDoS sample recently uploaded to VirusTotal. This particular sample caught our attention from this OTX Pulse. This sample borrows from BASHLITE malware where the source code became publicly available a few years ago. The sample is commonly labeled Gafgyt by many AV vendors, recent details on this malware have been reported by Unit 42, however, Radware recently published a blog on this sample discovering the authors naming it DemonBot. In this post, we will take a look at the particular sample found in VirusTotal.
Sample Details
When executed, the malware begins by initiating a connection to the hardcoded IP 80.211.28.43 via TCP port 23. Note this is just a TCP connection over port 23, data sent back and forth is not telnet. At the time of this writing, the CNC was alive and receiving connections. After the connection is established, the malware gathers survey information from the host it is executing on:
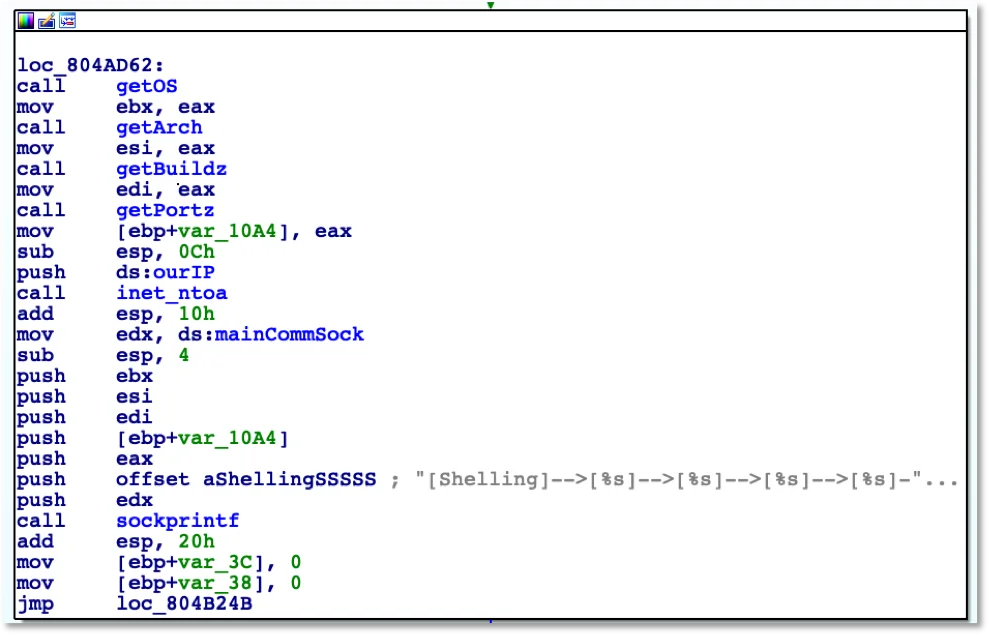
Figure 1. Disassembly of routine for gathering survey data
The malware begins checking for the presence of certain files and reports information related to what those files indicate such as a Debian device vs an REHL device, presence of Perl, Python and Telnet. The malware gathers the IP of the system and builds a string to send to the remote IP.
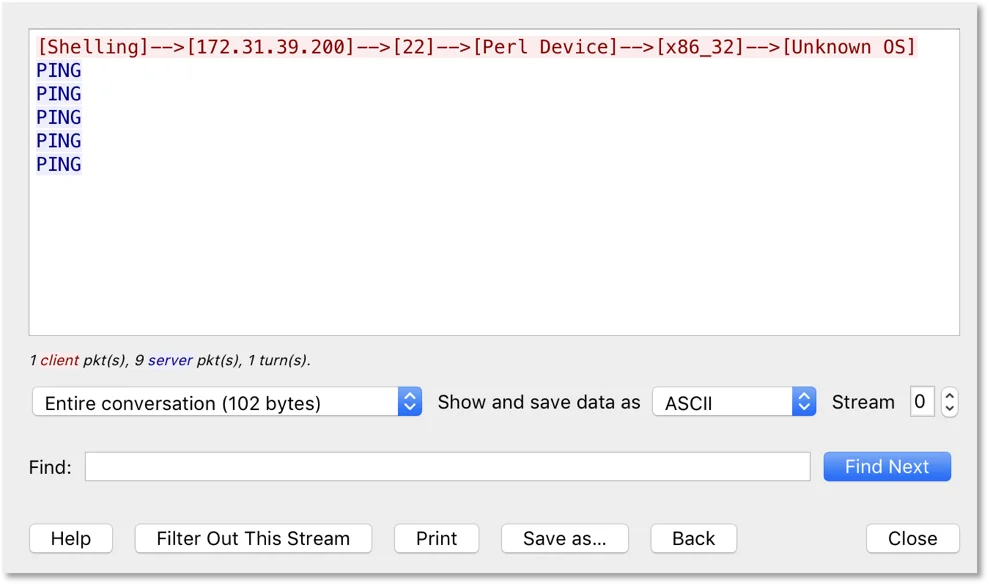
Figure 2. Wireshark capture of initial connection to CNC
After sending the initial string and survey information (which could make for a simple IDS signature) the malware parses strings that are sent back from the remote IP (CNC). Since the core functionality of the malware is to conduct denial of service, there are a number of different options for packet creation. The malware supports UDP floods, TCP floods, multiple target IPs, time durations, IP spoofing, and more. Specifically, the malware checks incoming data for the presence of the following commands:
| UDP | Send UDP packets with random data to target IPs and ports for given period of time. |
| STD | Send hardcoded data to target IPs and ports. |
| TCP | Send TCP packets to target IPs and for given period of time. |
| STOMP | Combination of STD, UDP, and TCP. |
| CNC | Connect to new CNC IP Address. |
| STOP | Kill processes associated with the malware. |
Detection in Lacework
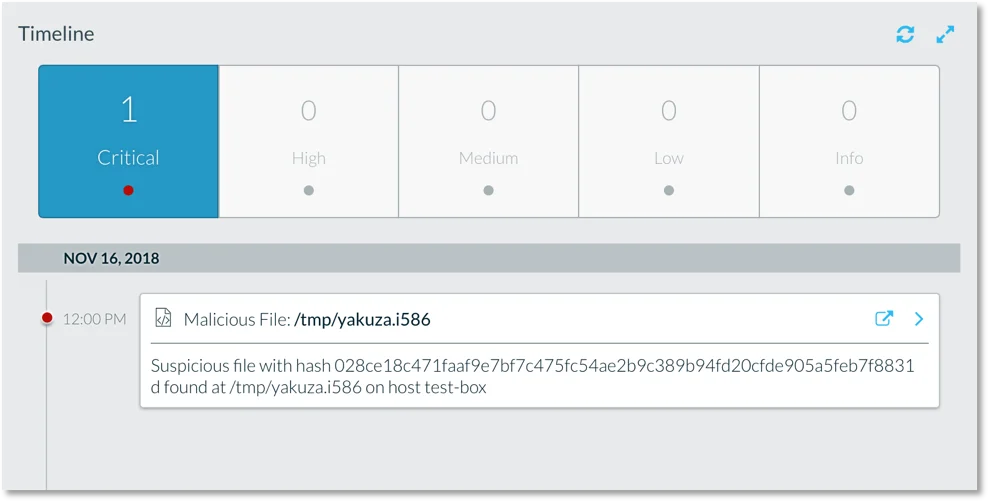
Lacework’s File Integrity Monitoring (FIM) feature in the Lacework agent regularly looks for new files and file changes. In this case, when the binary is written to disk, FIM checks this change and reports it as malicious.
Figure 3. FIM detection of the malicious binary
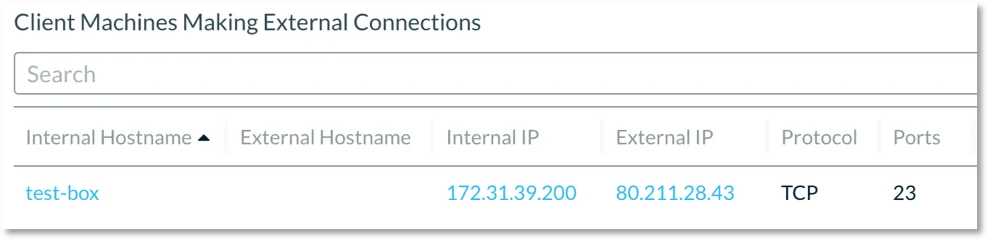
Additionally, network activity from the binary is monitored and details around the file’s execution can be investigated in the Lacework UI.
Figure 4. Network activity from the malware sample
Summary
The functionality of this sample is pretty simple, conduct denial of service attacks against supplied targets with a number of options (TCP, UDP, IP spoofing, fixed data, random data, etc). Like many DDoS samples found since Mirai, it borrows from other famous botnets. Based on the steady stream of new DDoS botnet samples and the availability of source code we can expect to see more to come.
Indicators
028ce18c471faaf9e7bf7c475fc54ae2b9c389b94fd20cfde905a5feb7f8831d, Malware Sample 80.211.28.43:23, CNC IP & Port
Categories
Suggested for you