Cloud security demands a Leader
Cybersecurity is not for the faint of heart, especially for regulated industries, including finance. There’s too much on the line. Even the smallest error can permanently break trust with customers.
And in these situations, security solutions must solve problems, not create new ones. Yet, sadly, many teams find their tools working against them when they need them most.
“We were dealing with 200 alerts a day coming in — resulting in about 10 hours on average, every day, of our front line SOC staff to triage these alerts,” says John Turner, Senior Security Architect at LendingTree. That’s a lot of alerts — a lot of stress — from the very tools they purchased to solve their cybersecurity needs.
Then Turner found Lacework. “Within a very short time of having Lacework integrated into our cloud environments, we were able to go from a couple hundred alerts a day down to just a handful, I’m talking less than five … these 5 alerts were actionable right out of the gate.”
These are the kinds of stories that Lacework hears from our amazing customers every day, across all industries. And we’re proud to, once again, be voted by our customers as Leader across multiple cloud security categories with the release of the new G2 Fall Reports.
Cloud security depth and breadth
With the release of the G2 Fall Reports, Lacework finds itself in the Leader quadrant across 7 different categories:
- Cloud-Native Application Protection Platform (CNAPP)
- Cloud Security Posture Management (CSPM)
- Cloud Workload Protection Platform (CWPP)
- Cloud Compliance
- Cloud Security
- Cloud Security Monitoring and Analytics
- Container Security
Why lead that list with the CNAPP category? Because CNAPP encompasses the other categories — one platform that covers CSPM, CWPP, compliance, container security, and more.
Yet, years before CNAPP was labeled as a category (circa 2021), Lacework had already brought a CNAPP to customers. A single platform that analyzed customer data (gathered via agent and/or agentless) to accomplish cloud security use cases (posture management, vulnerability management, threat detection, etc.) in new and innovative ways.
And, here, 8 years since we first started taking our CNAPP to market, we’re still being recognized as an innovator. A big thank you goes out to our customers. We appreciate them enabling us to be recognized as Leader for many years across so many categories. And for, frankly, being the driving force behind many of our innovative ideas.
I can’t even count how many times we’ve mentioned a feature we’d love to see, and Lacework shows us that it’s already on their product roadmap. This gives us confidence that, as time goes on, the Lacework technology will keep innovating.
Hear from the customers
Here’s a small glimpse into the experience our customers have with Lacework. This feedback comes directly from the honest customer reviews left on G2.
🌟🌟🌟🌟🌟
“Lacework normalizes visibility in the cloud, promoting better detection and response in a complex and constantly evolving threat landscape. Seeing value immediately after deployment is a significant advantage of the Lacework Platform. This immediate ROI allows even the most inexperienced members of a security team to be an active part of addressing cloud security risks.”
— David Christensen, CISO, PlanSource
🌟🌟🌟🌟🌟
“We rely on Lacework to understand and manage our workloads, security posture, and vulnerabilities throughout our enterprise. Lacework helps us meet our operational, security and compliance goals with a rich feature set that can dynamically adjust to our ever-changing requirements.”
— Gregory Garner, Global Director Security & Compliance, Software Development company
🌟🌟🌟🌟🌟
“This tool is a game-changer. Its fantastic alert system and easy-to-use interface save us hours each month. It’s the perfect solution for anyone looking to streamline their cloud security process and focus on what matters — their product. With Lacework’s capability to detect any unusual behaviour, we can focus our attention on improving our platform, knowing that we will be alerted if anything needs our immediate attention.”
— Junior Godoi, Head of Engineering, IT Services and IT Consulting company
Take a look at even more reviews from satisfied Lacework customers on our G2 page.
Secure more within the cloud
Our customers can more effectively tackle the complexity of the cloud as we continue to enhance our platform and build better cloud security. Most recently, we have introduced:
Cloud infrastructure entitlement management (CIEM)
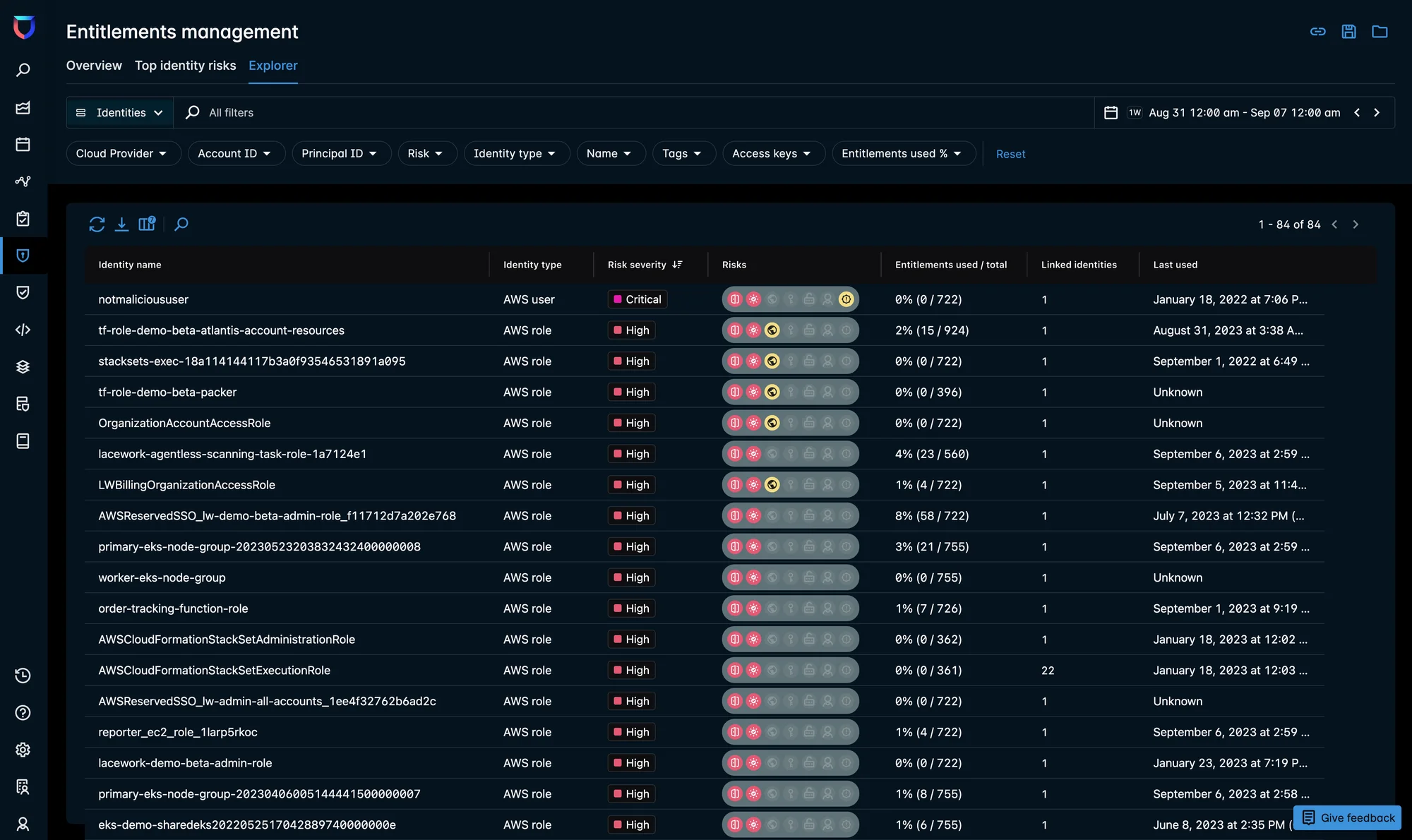
Reducing cloud identity risk plays an important role in comprehensive security. With over 35,000 granular permissions across cloud services providers, it can be a daunting task to limit and identify excessive permissions that may leave companies exposed to a breach. Our customers now have visibility into their cloud identities and associated permissions, empowering them with the keys to achieve the principle of least privilege.
Figure 1: The Entitlements Explorer lists all identities within your cloud environment prioritized by risk, with context on why each received its risk score.
Custom risk-based vulnerability risk score
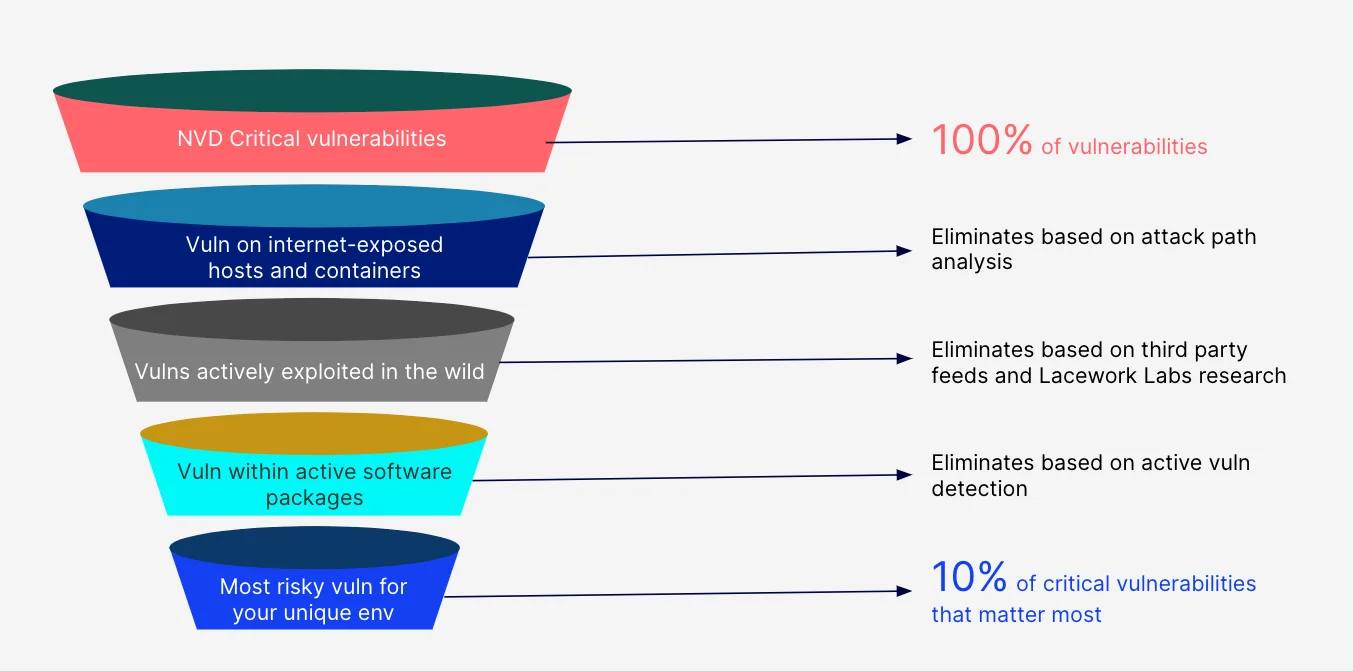
Automation is critical for security teams. It’s necessary for productivity, business growth, and cost savings, especially during a talent shortage. Lacework can now help customers simplify risk management using automation to provide teams with custom risk-based vulnerability scores unique to each customer’s environment. This enables teams to reduce 90% of vulnerability noise and only focus on their most critical active vulnerabilities.
Figure 2: Lacework provides a custom risk score that passes vulnerabilities through a number of filters until you’re left with the 10% of your most critical issues.
The innovation continues
Once again, none of this would be possible without our customers, whose voices shape the very platform that they use to secure their cloud environments.
To John Turner, Steve Lukose, David Christensen, Gregory Garnter, Junior Godoi, and the countless other security professionals that we partner with on a day-to-day basis — thank you.
Want to learn more about our data-driven approach and find out how we can help you secure your environment from build to runtime? Contact us today.
Why G2?
G2 is the world’s largest and most trusted software review platform. With 1.8 million reviews and counting, G2 helps drive better buying decisions — leveraging real customer reviews. Technology buyers, investors, and analysts go to the site to compare and select the best software based on peer reviews from verified users, as well as data aggregated from online resources and social networks.
To read more about what our customers have to say about us, visit G2.com. To read more about our products and past awards, please check out our blog.
Suggested for you