AndroxGh0st in the news: Exploring the malware’s surge in attention
In 2022, the Lacework Labs team discovered a new, large-scale threat called AndroxGh0st, a Python malware being used to exploit AWS keys. Its discovery was a concern, but it was only last week that AndroxGh0st finally gained the widespread public attention it deserved, when the FBI and CISA issued a warning about the threat and key signs to watch out for.
When Lacework Labs first encountered AndroxGh0st while researching our first AWS composite alert (research conducted in 2022, published a little over a year ago), they found that it was capable of scanning for and exploiting exposed credentials and APIs. AndroxGh0st targets specific files known as Laravel.env files, which are crucial because they contain access keys and credentials for major services like AWS and Microsoft Office 365. The abuse actions leveraging compromised keys require the third party to already have the keys with the required privileges to take the malicious actions.
The theft of these files poses a serious risk, as it enables hackers to gain unauthorized access and potentially disrupt services. More alarmingly, this malware has been used by hackers to build a botnet, which is a network of compromised computers, to then be used for additional credential theft and launching further cyberattacks.
The recent advisory from the FBI and CISA marks a turning point in the perception of AndroxGh0st, with it now recognized as a significant national cybersecurity threat because of its potential widespread impact on both businesses and individual users. News platforms and experts are now intensively covering AndroxGh0st, offering detailed analysis of its operation, potential risks, and preventive measures.
Here’s a preview of what experts have been saying:
How Lacework can help
As we’ve seen, the AndroxGh0st malware represents a significant and evolving threat. Since Lacework Labs published the initial blog in 2022, we have helped our customers address this threat by triggering over 200 alerts that were the result of AndroxGh0st or functionally similar malware.
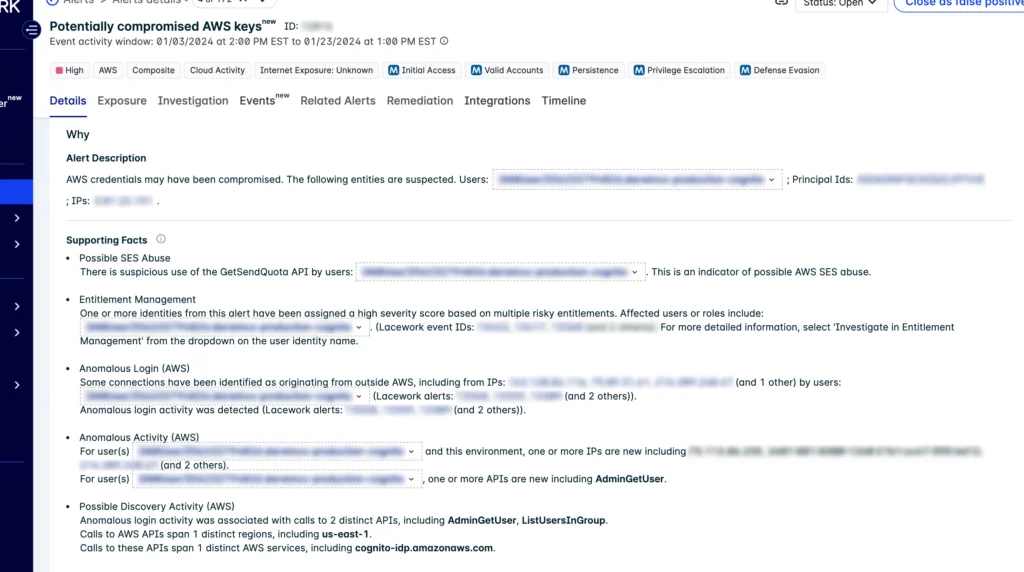
In this example composite alert below, the first signal is for AWS Simple Email Service (SES) abuse, which is a strong indicator of this activity. Composite alerting has become an effective tool for our customers to detect compromised credential usage, not only for AndroxGh0st, but other activities as well. This is because anomalies need to be taken into account in order to qualify rule-based detections.
Want to see for yourself how Lacework helps discover the latest threats? Get complete access to our platform with our 14-day free trial here.
Suggested for you


