9 factors to look for in a modern CWPP
This blog covers key cloud workload protection platform (CWPP) features in 2023, as defined by Frost & Sullivan in their newest report, Frost Radar™: Cloud Workload Protection Platforms, 2023. In that report, Frost & Sullivan rated Lacework as a top Leader in both innovation and growth.
Workload protection is a core capability for any organization trying to secure today’s private, public, hybrid, or multicloud environments. While proactive measures like posture and vulnerability management are important, the level of protection at your company will never reach 100%. In a world where the average time to detect and respond to threats is around 9 months, security teams must employ automated workload monitoring to ensure bad actors are caught as early as possible.
The cybersecurity talent shortage makes the need for automated solutions even greater. In 2022, the cybersecurity workforce gap increased by 26%, giving hackers another advantage. Security teams are strained, budgets are tight, and a simple cloud configuration mistake can lead to devastating results. According to the Cloud Security Alliance, 15 million data records worldwide were exposed in the third quarter of 2022, an increase of 37% over the prior quarter.
What is a CWPP?
Think of a CWPP like your own body’s immune system — it keeps you safe from infection and harmful bugs. Like your white blood cells, CWPP detects and responds to potential threats facing your cloud workloads and neutralizes abnormal activity. When your body detects a threat, it stimulates an appropriate response to eliminate the danger to mitigate security risks.
According to Frost & Sullivan, a CWPP is a server workload-centric security solution to protect computing workloads in cloud environments (private, public, hybrid, and multicloud) from cybersecurity risks and attacks. Typical workloads that CWPPs secure include cloud hosts, virtual machines (VMs), containers, Kubernetes (K8s), databases (SQL and NoSQL), and APIs. CWPPs are also typically agent-based solutions.
Frost & Sullivan expands the traditional definition of a CWPP to include capabilities that commonly fall into build time application security, like configuration and vulnerability management and compliance. Based on Frost & Sullivan’s definition, a true CWPP platform must provide the capabilities of workload discovery, tagging, configuration, image hardening, and vulnerability management, and provide protection for workloads , which spans firewalling, segmentation, system file integrity management (SIM/FIM), application control, exploit prevention/memory protection, as well as threat detection & response in runtime environment.
Top 9 must-have CWPP features
Traditional approaches built to secure VMs, and classical servers simply don’t work for many modern cloud technologies. These techniques lack visibility, scalability, and speed. They also require extensive security expertise to maintain and manage. Today, organizations must invest in a CWPP built to secure ephemeral workloads in cloud hosts, VMs, containers, K8s, databases (SQL and NoSQL), and APIs.
According to Frost & Sullivan, customers seeking a CWPP should prioritize a range of features when evaluating solutions, including the following:
- Support across diverse environments: Support for hybrid and multicloud deployments spanning on-premise, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud, with the ability to protect modern workloads across various environments, including VMs, containers, and K8s
- Simple deployment: Solutions that are easy to deploy and manage and do not incur significant ongoing overhead costs
- A lightweight, easy-to-manage agent: An agent-based eBPF framework to avoid potential issues with kernel modules and to simplify deployment
- Continuous threat monitoring: Real-time threat detection and response to minimize the impact of security incidents
- Behavior-based monitoring: Anti-malware and behavior-based monitoring to protect customers’ workloads from malware and monitor their workloads’ behavior by detecting anomalies and threats
- Risk management automation: Vulnerability and risk automation, including automated mapping to pre-built compliance frameworks, policies with minimal performance impact, and contextual vulnerability prioritization, which correlates security events and posture findings
- Posture drift detection: Ensure that workloads remain in compliance with security policies over time
- System / file integrity monitoring (SIM/FIM): Detection of unauthorized changes, protection against malware, and behavior monitoring to detect potential threats
- Deep application control: Real-time application control to prevent unauthorized access or changes
Lacework recognized as a leader in CWPP
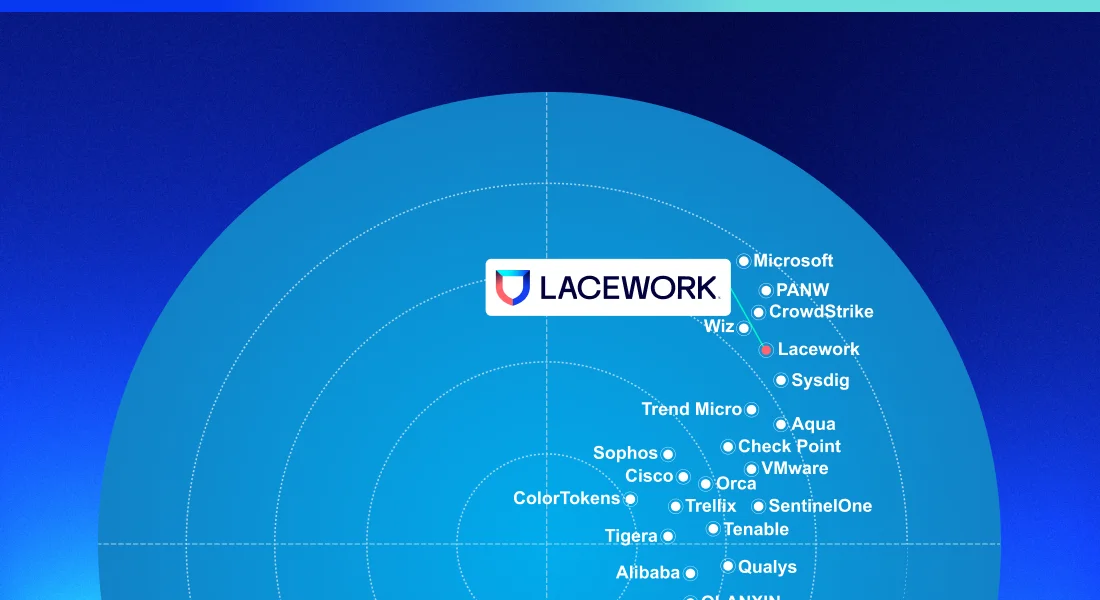
Lacework checks every box for a top-rated CWPP — an accolade recognized by analysts since the company was founded. In Frost & Sullivan’s latest report, Lacework found itself among top leaders. Of the 25 vendors, Lacework was tied for 3rd in innovation and 5th in growth.
The analyst highlighted the company’s continued growth and dedication to workload security innovation, as a part of the company’s larger security platform. Lacework was recognized for its platform’s ability to operationalize DevSecOps within organizations and for its clear innovation roadmap, focusing on posture management, threat detection and investigation, and automated remediation.
With Lacework, you can experience:
- Rapid detection and response with smart automation
- Continuous monitoring for unusual behaviors and deep insights across supply chains and complex environments
- Developer empowerment by seamlessly integrating security into development environments
- Integration of security into existing workflows like ticketing systems and collaboration platforms
- Choice and flexibility, with both agentless and agent-based techniques and approaches
- A single platform that combines CWPP alongside other functions — cloud security posture management (CSPM), cloud infrastructure entitlement management (CIEM), infrastructure as code (IaC) security, cloud detection and response (CDR), and more — to enable security across the full application lifecycle
To learn more, read Frost & Sullivan’s latest report, Frost Radar™: Global Cloud Workload Protection Platform (CWPP).
Suggested for you