4 surprising things I learned about hackers at Black Hat

- They’re operating in mostly the same ways that they did nearly two decades ago
Cybersecurity/national security journalist Kim Zetter—also the first journalist to speak at a Black Hat keynote—told a story about a source who approached her in 2006, claiming that he knew key information about hackers who were involved in massive breaches of bank card numbers.
The source said he knew this because he was arrested by the FBI while acting as a mule to help international hackers launder money. After he was arrested, the FBI recruited him to run an underground carding forum to help the government understand how cybercriminals planned their conspiracies.
Because this source was a professional liar, Kim was hesitant to believe him. However, he provided receipts of the chat logs of the forums and gave contact information that Kim used to track down witnesses and eventually verify his story.
Although this happened in 2006, Kim said that this story could easily be from last month or even last week, because hackers run their criminal enterprises mostly the same today. Hackers organize in underground forums, make a lot of money, and launder it through digital currency, just like they did more than 15 years ago. “They still bicker, still double cross each other, and still think law enforcement won’t catch them, and sometimes they’re right about that,” she said.
The biggest differences in how hackers operate today is that they have now perfected their techniques and also offer each other salaried employment.

- They look up to infamous hackers
In between Black Hat briefings, I had a chance to talk to a few of the “hackers”—some of which are actually security researchers, analysts, and engineers working for corporations as attackers and defenders to help their companies improve their security. When I asked these attendees if they had a favorite hacker, I was surprised to find that several people could identify a favorite hacker off the top of their head and were eager to discuss them.
One person said their favorite was geohot, or George Hotz, because he was one of the first people to hack the PlayStation 3. He also started his own company, Comma.ai, which developed a semi-automatic driving system.
Another hacker-favorite was Michael Lynn, who was an Internet Security Systems (now IBM) security researcher who discovered a critical Cisco router vulnerability in 2005. When his company and Cisco tried to prevent him from giving a presentation on the issue at Black Hat conference at the last minute, he quit his job to make sure he was able to share the information with the public.
A few people also discussed the hacker group Anonymous, which consists of activists from different countries and is popular because of the cyberattacks they conduct on governments.
- It’s really easy for hackers to impersonate banks and other legitimate companies via text
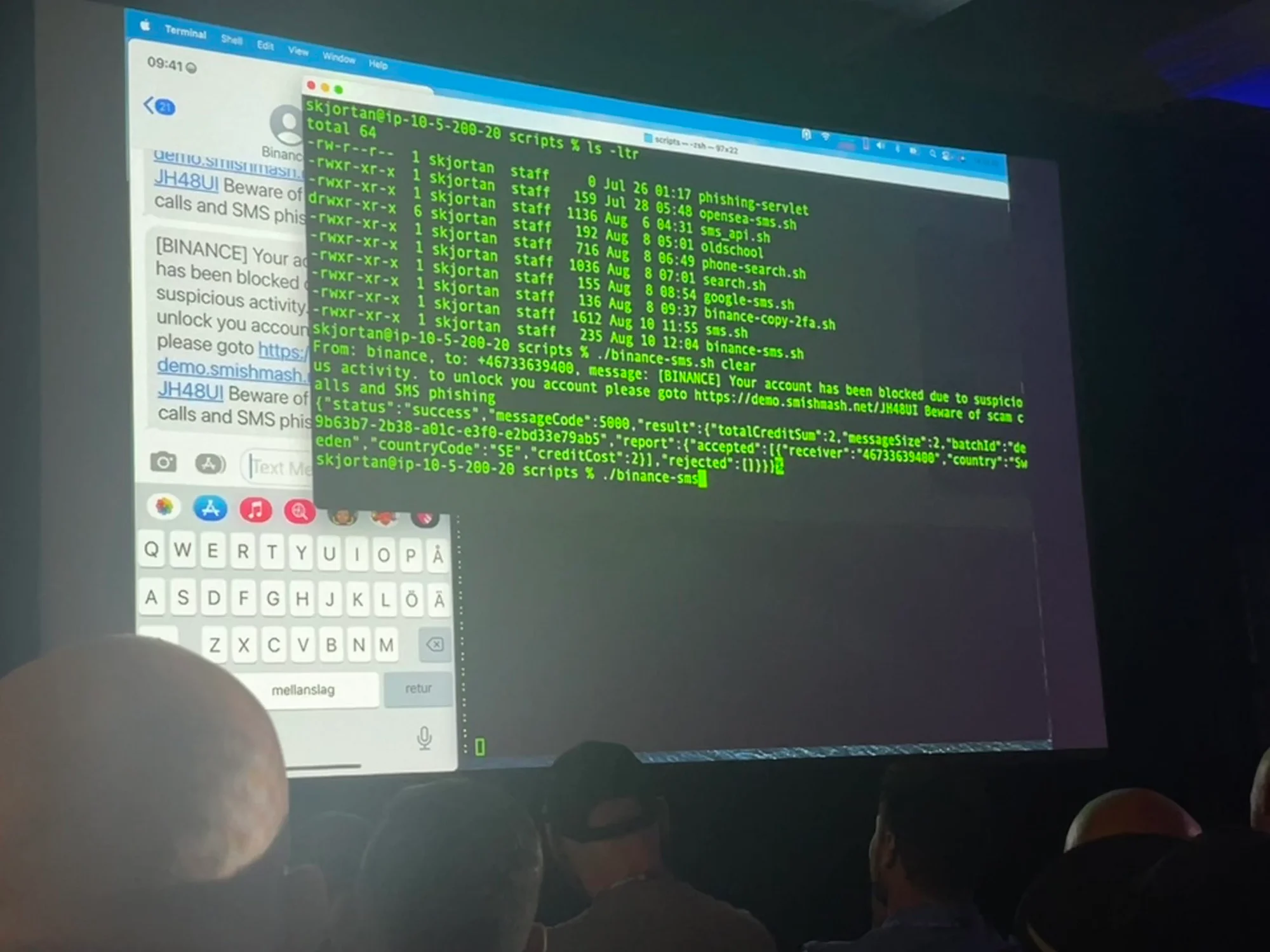
If you’ve noticed an increase in spam or spoofed text messages that appear to come from your bank or other legitimate sources, you’re not alone. SMS phishing—or “smishing,” as hacking experts Thomas Olofsson and Mikael Bystrom called it in their Black Hat presentation—attacks expanded by more than seven times in the first two quarters of 2021 compared to 2020.
If you haven’t noticed more fake texts, that doesn’t necessarily mean you’re safe—35 percent of people targeted via SMS don’t even realize they’re being attacked. It’s surprisingly simple for hackers to perform these attacks. Thomas and Mikael demonstrated how hackers can find phone numbers and the email addresses and passwords that they’re connected to online, which they then use to bypass two-factor authentication.
They then showed us how hackers use those credentials to impersonate a business like your bank—the messages actually show up in the same text message thread as legitimate texts do, which is why many people never realize they’re fake and don’t realize their accounts have been compromised until it’s too late.
- IAM solutions are prime hacker targets
Identity and access management (IAM) solutions are prime targets for hackers because they “hold all the keys to the kingdom,” Steven Seeley said in his session, “I Am Whoever I Say I Am.” If hackers can gain access to IAM, they can have full control of authentication and authorization.
“IAM is the core service and it must be protected,” security researchers Igal Gofman and Noam Dahan said in their session, “IAM the One Who Knocks.” They also shared a key IAM lesson: Default roles are an attacker’s best friend. While some default roles can sound innocent—like “viewer”—they actually give you very significant data access.

What can we do to protect our organizations’ IAM?
We should limit the effect that a mistake can have and ensure that there is no single point of failure. Stick to one AWS account/GCP project/Azure resource group per workload. Deploy organizational policies to limit disasters, avoid permanent credentials, and secure human identities.
What’s next?
While Black Hat provided a lot of valuable insight into the minds of hackers, we still have much more to learn about cyber threats and the future of security. “The unthinkable complexity of cyberspace, we’re there right now,” Chris Krebs, the first director of CISA said in his keynote speech. We need to continue to develop products that solve underlying challenges instead of focusing on temporary solutions. “Until we make meaningful consequences and impose costs on bad actors, they will continue to get their wins,” he said.
For more information on Black Hat speakers, recordings, and slides, see the Black Hat USA 2022 website.
You can also check out our blog for more info on the state of cloud security.
Categories
Suggested for you


