Groundhog Botnet Rapidly Infecting Cloud
Chris Hall
Cloud Security Researcher, Lacework Labs
As early as 2015, the “Groundhog” DDOS botnet began proliferating via SSH brute force attacks. The botnet is believed to have a China nexus and has been active since its inception. In early December 2020, Lacework started monitoring recent activity along with botnet traffic from a sinkhole operation. Our analysis revealed the botnet is rapidly expanding by hundreds of new infections daily and has to date infected at least 26K servers. The majority of infections were found within Brazil, US, and India and include clusters of cloud infrastructure from major providers such as Amazon, GCP and Azure.
The Groundhog botnet is composed of two closely related malware variants: XOR.DDOS & Groundhog. This blog summarizes the XOR.DDOS malware component and provides details on the botnet and infrastructure.
Malware
As the name suggests XOR.DDOS is a DDOS (Distributed Denial of Service) capable Linux malware with the ability to perform related tasks such as SYN/ACK flood and DNS amplification. Additional functionality includes the ability to download other malware, perform system reconnaissance, and kill running processes.
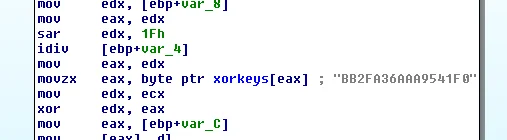
All observed variants of XOR.DDOS leverage the same XOR key for decoding of embedded and downloaded configurations. The XOR key (0xBB2FA36AAA9541F0) is statically observable and named within the binary.
|
Figure 1. XOR key
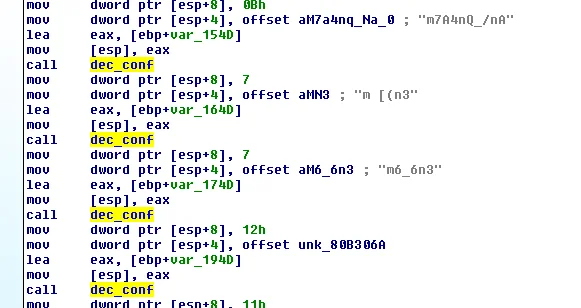
Also conveniently named is the function (dec_conf) which is responsible for decoding the configurations with the key. Figure 2 shows static strings being passed as arguments for the dec_conf function.
|
Figure 2. “dec_conf” function
Embedded configurations consist of commands for system information collection (ie netstat) and C2 domains and ports. All C2 configs are formatted in the same way and either contain a domain and port twice or a domain and port with its hosting IP. The following are examples of these decoded configurations seen in various samples:
- 118.193.207.139:8925|118.193.207.139:8925
- 185.243.242.112:8725|185.243.242.112:8725
- ishaoqian.f3322.org:2444|183.60.202.2:2444
- h0t.cktool.pw:5012|162.220.11.221:5012
- henchebazi.f3322.net:11023|henchebazi.f3322.net:11023
- ww.myserv012.com:3307|ww.search2c.com:3307
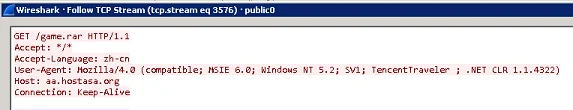
XOR.DDOS checks for new configuration data with a GET request like the one shown below. All observed samples use the same user agent which is characterized by the ‘TencentTraveler” string.
|
Figure 3. XOR.DDOS configuration download
The downloaded file is not actually a RAR file but is XOR encoded using the previously mentioned key. The following python code will decode any config using the same key.
1
2
3
4
5
6
7
8
9
10
11
#decrypts XOR.DDOS configs and C2s
#test sample:aaC20c40e23ea5fee6c105700418e8e7e1e4fab3a654484430592b10ecbfc84f
def xor(data, key):
l = len(key)
return bytearray((
(data[i] ^ key[i % l]) for i in range(0,len(data))
))
data = bytearray(open(‘leg.rar’, ‘rb’).read())
key = bytearray([0x42,0x42,0x32,0x46,0x41,0x33,0x36,0x41,0x41,0x41,0x39,0x35,0x34,0x31,0x46,0x30])
print xor(data,key)The configuration will typically contain a list of processes and IP connections to kill, both of which belong to other malware families. This is reminiscent of in-fighting seen among cryptojackers when competing for cyber real-estate. The following are example contents from downloaded configurations:
denyip=113.105.157.165,113.105.157.20,113.105.157.41,113.53.243.123,114.215.130.230
filename=/root/L26_25001,/root/myshh,/tmp/.sshdd,/root/sshdd,/root/server26,/root/26sunwukong
rmfile=/etc/dbus-daemon,/etc/gnome-system,/root/sql200,/root/Explorer-aovtu,/etc/syslogd-gonsysFor an in-depth analysis of XOR.DDOS refer to Checkpoint’s whitepaper
Botnet & Infrastructure Analysis
Lacework analyzed sinkhole logs for two XOR.DDOS domains
- hostasa.org
- dsaj2a.org
These are older domains however many new XOR.DDOS specimens are configured to connect to both recent and legacy C2s. This allowed insight into both residual and ongoing botnet activity. To date, we’ve logged over 26K unique infections with an average of 523 new bots per day. Sinkhole records were classified as bots only if they exhibited XOR.DDOS protocols. Note: The botnet observed from this sinkhole data is likely a small portion as Lacework only had visibility into two c2s.
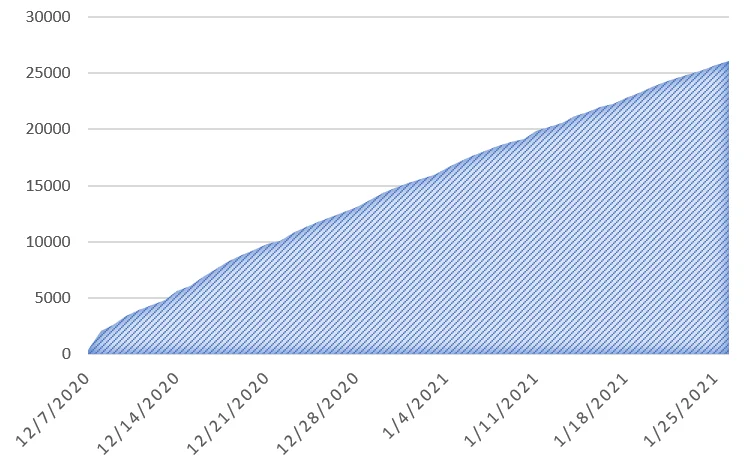
|
Figure 4. Groundhog bots from sinkhole
The following shows newly observed infection counts since tracking. For the past month new infections have been steadily ranging between 300 and 600 per day. Often with sinkhole data, new infections trend down very quickly if there is not active propagation. This indicates a steady expansion of newly added Groundhog bots.
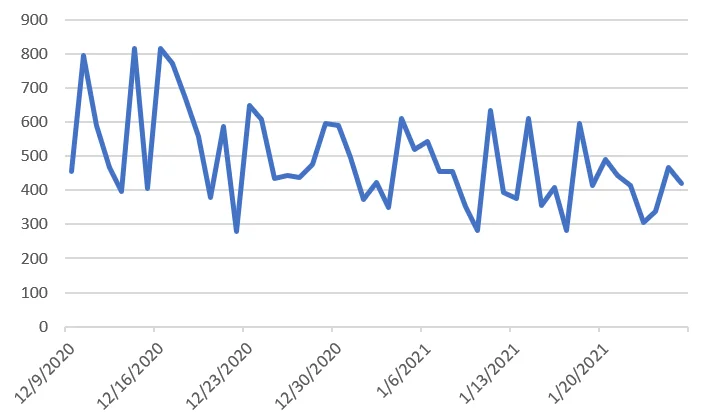
|
Figure 5. Daily new bots
Whois data on bot IPs revealed Groundhog infections in 147 countries and in over 1600 networks. The majority were geolocated to Brazil, United States, and India. This widespread distribution of the botnet is more indicative of opportunistic targeting. This means the geographic and network breakdown of Groundhog bots may also represent rankings with regards general SSH brute forcing vulnerability.
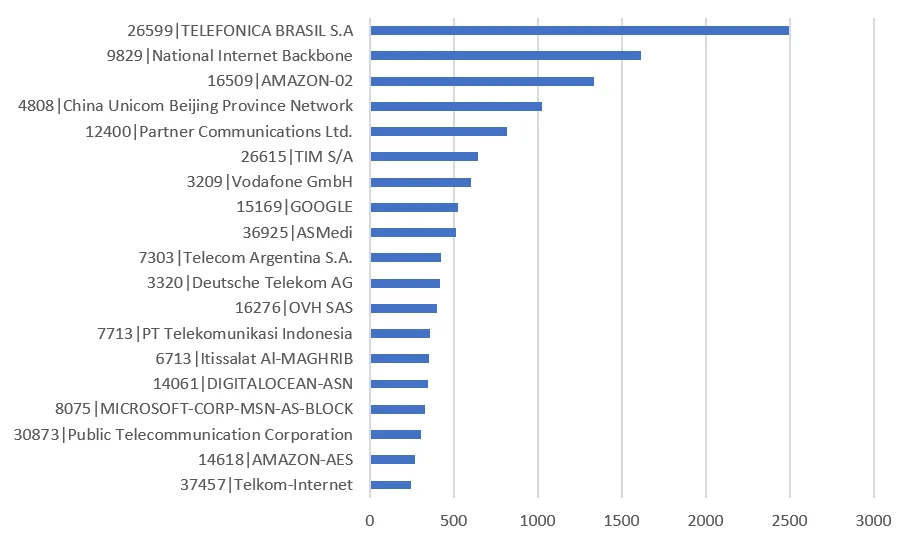
|
Figure 6. Bot networks
Groundhog has historically leveraged numerous C2 domains, many simultaneously. Several different registrars are used with a preference for Name.com, Godaddy, and various Chinese registrars. Domains are a typically a combination of characters and letters, many of which are slight permutations of one another. Subdomain reuse and naming conventions have also been used. Examples:
| Subdomains & conventions | Examples |
| p# |
p10.sb1024.net p6.fly1989.com p5.2018fly.com |
| ww |
ww.dnstells.com ww.gzcfr5axf6.com ww.gzcfr5axf7.com ww.myserv012.com ww.search2c.com |
| ns# |
ns1.hostasa.org ns2.hostasa.org ns3.hostasa.org ns4.hostasa.orga |
| aa & aaa |
aa.finance1num.org aa.hostasa.org aaa.dsaj2a.org aaa.gggatat456.com aaa.xxxatat456.com |
There were also hosting trends in Groundhogs botnet infrastructure components. For example, the malware distribution infrastructure and C2 IPS have their respective common providers. Several recent C2 IPs are hosted on OVH SAS (AS 16276), and US provider QuadraNet (AS 8100). A common thread among specimens observed during the last 90 days is the use of GorrillaServers (AS 53850). GorrillaServers is also a US provider however it’s a known source of attacks originating from China. In 2017 it was used for hosting a domain leveraged by state actors in a campaign against Uighur activists.
These samples all have payload names that are port numbers, some of which have been used by XOR.DDOS, however the payload name does not always map with the port used by the specimen.
| host | ASN | ORG | XOR.DDOS Malware URLs |
| 154.48.227.89 | 58879 | Shanghai Anchang Network Security Technology Co.,Ltd. | http://154.48.227.89/443 |
| 98.159.110.69 | 53850 | GORILLASERVERS |
http://98.159.110.69/3309 http://98.159.110.69/443 http://98.159.110.69/53 http://98.159.110.69/80 http://98.159.110.69/8000 http://98.159.110.69/8080 |
| 98.159.110.44 | 53850 | GORILLASERVERS |
http://98.159.110.44/21 http://98.159.110.44/23 http://98.159.110.44/3307 http://98.159.110.44/80 http://98.159.110.44/8080 |
| 98.159.99.26 | 53850 | GORILLASERVERS | http://98.159.99.26/23 |
| 98.159.99.92 | 53850 | GORILLASERVERS |
http://98.159.99.92/3307 http://98.159.99.92/3308 |
| 98.159.110.72 | 53850 | GORILLASERVERS | http://98.159.110.72/23 |
| 222.186.128.172 | 23650 | AS Number for CHINANET jiangsu province backbone |
http://222.186.128.172:5523/5530 http://222.186.128.172:5523/5535 |
Propagation
SSH remains by far the most attacked port in the wild as it is the most popular service for remote access and administration. Also, many systems have default credentials making them easy targets.
Checkpoint reported in 2015 that Groundhog/XOR.DDOS infections were preceded by SSH bruteforce attacks suggesting this to be the botnet’s propagation method. The XOR.DDOS malware however is not bundled with any propagation module so the occurrence of SSH brute-forcing is circumstantial and it’s very possible there are other mechanisms. Nonetheless, Groundhog bots were observed carrying out SSH brute force attacks. Lacework cross-referenced bot IPs against common blocklists such as www.blocklist.de and there were 531 matches – meaning about 2% of observed bots are known brute forcing hosts.
Logistically, botnets remain the most effective system for brute force campaigns since the larger they are, the more resistant they become to blacklisting countermeasures. This is especially true with Groundhog due to the small overlap between botnet IPS and brute force lists.
Conclusion
As demonstrated with the Groundhog sinkholes, the botnet is quite vulnerable to disruption because custom configurations can easily be served to bots. However, Groundhog is still a good case study in how poor security practices can be exploited at scale. As with many botnet threats, exposure can be effectively mitigated with simple security configurations. We presume the botnet will continue to thrive in the future and could be monetized with cryptomining if not already.
XOR.DDOS indicators from this analysis are provided in our Github repository. If you found this blog useful then please share and follow us on Twitter!
Categories
Suggested for you


